[ad_1]
This weblog was collectively written with Alejandro Prada and Ofer Caspi.
Executive abstract
SeroXen is a brand new Remote Access Trojan (RAT) that confirmed up in late 2022 and is gaining popularity in 2023. Advertised as a professional instrument that provides entry to your computer systems undetected, it’s being bought for less than $30 for a month-to-month license or $60 for a lifetime bundle, making it accessible.
Key takeaways:
- SeroXen is a fileless RAT, performing effectively at evading detections on static and dynamic evaluation.
- The malware combines a number of open-source initiatives to enhance its capabilities. It is a mixture of Quasar RAT, r77-rootkit and the command line NirCmd.
- Hundreds of samples have proven up since its creation, being hottest within the gaming neighborhood. It is barely a matter of time earlier than it’s used to focus on firms as an alternative of particular person customers.
Analysis
Quasar RAT is a professional open-source distant administration instrument. It is obtainable on github web page to offer consumer assist or worker monitoring. It has been traditionally related to malicious exercise carried out by menace actors, APT teams (like on this Mandiant report from 2017), or authorities assaults (on this report by Unit42 in 2017).
It was first launched in July 2014 as “xRAT” and renamed to “Quasar” in August 2015. Since then, there have been launched updates to the code till v1.4.1 in March 2023, which is essentially the most present model. As an open-source RAT instrument with updates 9 years after its creation, it’s no shock that it continues to be a standard instrument utilized by itself or mixed with different payloads by menace actors as much as at the present time.
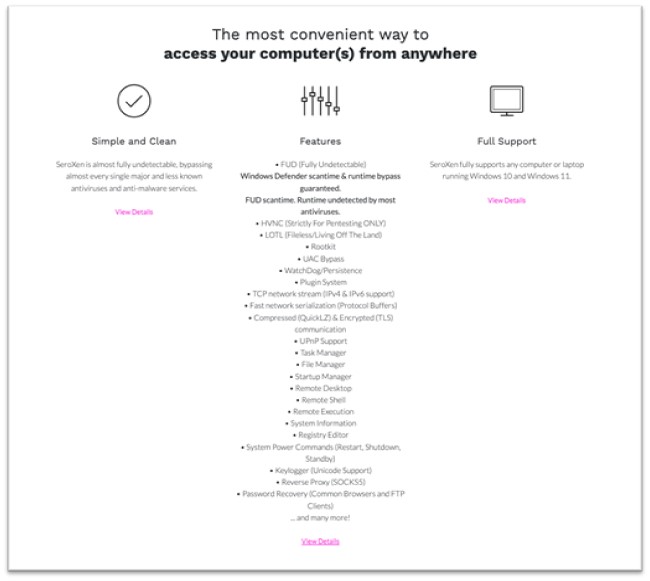
In a assessment of the latest samples, a brand new Quasar variant was noticed by Alien Labs within the wild: SeroXen. This new RAT is a modified department of the open-source model, including some modifications options to the unique RAT. They’re promoting it for month-to-month or lifetime charge. Figure 1 comprises among the options marketed on their web site.
Figure 1. SeroXen options introduced on its web site.
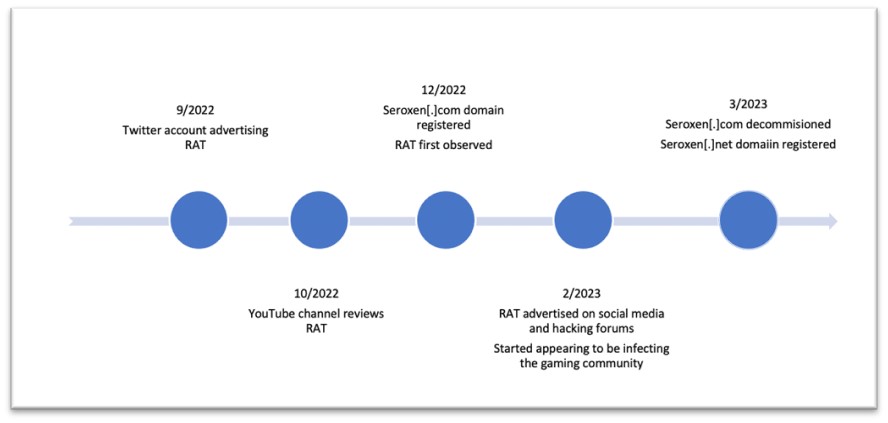
This new RAT first confirmed up on a Twitter account, established in September 2022. The individual promoting the RAT gave the impression to be an English-speaking teenager. The identical Twitter deal with printed a assessment of the RAT on YouTube. The video approached the assessment from an attacking/Red Team standpoint, encouraging individuals to purchase the instrument as a result of it’s definitely worth the cash. They have been claiming to be a reseller of the instrument.
In December 2022, a selected area was registered to market/promote the instrument, seroxen[.]com. The RAT was distributed by way of a month-to-month license for $30 USD or a lifetime license of $60 USD. It was round that point that the malware was first noticed within the wild, showing with 0 detections on VirusTotal.
After just a few months, on the first of February, the YouTuber CyberSec Zaado printed a video alerting the neighborhood in regards to the capabilities of the RAT from a defensive perspective. In late February, the RAT was marketed on social media platforms reminiscent of TikTok, Twitter, YouTube, and several other cracking boards, together with hackforums. There have been some conversations on gaming boards complaining about being contaminated by malware after downloading some video video games. The artifacts described by the customers matched with SeroXen RAT.
The menace actor up to date the area identify to seroxen[.]web by the top of March. This area identify was registered on March twenty seventh, 2023, after seroxen[.]com was decommissioned. The menace actor used GoDaddy for registration and Cloudflare for internet hosting the web site. These domains are solely used for promoting and advertising and marketing functions, and never for Command and Control (C&C) communications.
Figure 2: SeroXen web site
Based on the packed variations uploaded to VT, it seems that the RAT is getting used for concentrating on online game customers. Several lure injector cheat recordsdata have been noticed with names invoking fashionable videogames reminiscent of Fortnite, Valorant, Roblox or Warzone2. The menace actor used Discord for the distribution of among the samples.
Figure 3. SeroXen timeline.
One of essentially the most related introduced options is that it’s a absolutely undetectable model. This is at the moment true from a static evaluation standpoint, because the RAT is packaged into an obfuscated EnergyShell batch file. The file’s measurement usually ranges between 12-14 megabytes, as we will see in pattern 8ace121fae472cc7ce896c91a3f1743d5ccc8a389bc3152578c4782171c69e87 uploaded to VT on May 21. Due to its comparatively massive measurement, sure antivirus might select to not analyze it, doubtlessly bypassing detection. This pattern at the moment has 0 detections on VT, however among the crowdsourced Sigma Rules do detect the exercise as suspicious.
As the malware is fileless and executed solely in reminiscence after going by way of a number of decryptions and decompression routines, it’s tougher to detect by antiviruses. In addition, its rootkit hundreds a recent copy of ntdll.dll, which makes it tougher to detect by Endpoint Detection & Response (EDR) options that hook into it to detect course of injections.
Regarding the dynamic evaluation, it’s price noting that some sandbox environments would possibly fail to detect the RAT on account of its utilization of a number of methods to evade virtualization and sandbox detection mechanisms and string encryption subsequent payloads.
The RAT employs anti-debugging methods by leveraging Windows Management Instrumentation (WMI) to determine the system’s producer. This permits it to determine virtualization environments reminiscent of VMware and abort the execution to delay and make the evaluation tougher. The RAT additionally checks for the presence of debuggers and makes use of pings make the threads sleep.
Currently, most youngster processes and recordsdata dropped in the course of the execution of the RAT have a low detection charge.
Execution evaluation
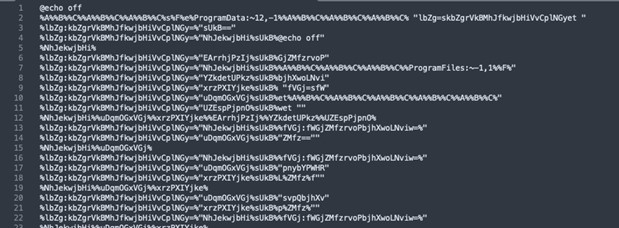
When the malicious payload is delivered to the sufferer, generally by way of a phishing mail or a Discord channel – the sufferer typically receives a ZIP file containing a benign file in plain sight, and the closely obfuscated batch file is hidden and mechanically executed when launched. The bat file format is at all times very comparable and appears just like the contents of Figure 4, adopted by base64 encoded textual content later within the file.
Figure 4. Obfuscated bat script.
During the bat execution, the script extracts two separate binaries from the base64 encoded textual content, AES decrypts, and GZIP decompresses it to supply two separate byte arrays. These byte arrays are then used with .NET reflection to carry out an in-memory load of the meeting from its bytes, find the binary’s entry level, and carry out an Invoke on each.
Throughout the decryption course of, the attackers had the necessity to create a professional trying folder to drop a bootleg model of the System Configuration Utility msconfig.exe that’s required later. For this goal, the script creates the folder “C:Windows System32”, with an area after Windows and deletes it as quickly because the utility is operating. If it wasn’t for this file briefly dropped into disk, the RAT can be absolutely fileless.
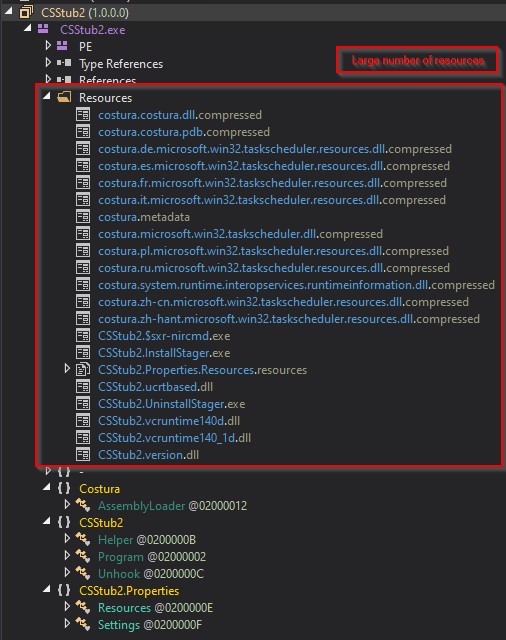
The execution of one of many above-mentioned binaries results in one other obfuscated binary carrying an embedded useful resource. This useful resource is hidden behind anti-sandboxing and debugger methods, solely to result in extra obfuscation and encryption methods that result in the ultimate payload. This payload has been constructed utilizing the Github mission Costura, which permits SeroXen to pack the code’s dependencies into the .NET meeting so it may possibly run self-contained.
Figure 5. Payload embedded assets.
The extraction of the assets results in the ultimate payloads. This is within the type of two .NET assemblies: CSStub2.InstallStager.exe, and CSStub2.UninstallStager.exe. And a Win32 binary referred to as CSStub2.$sxr-nircmd.exe, which corresponds to the unmodified command-line utility NirCmd.
The payload InstallStager.exe is a compilation of the open-source rootkit named r77-rootkit – a fileless ring 3 rootkit written in .NET. This rootkit helps each x32 and x64 Windows processes and has the next options:
- Fileless persistence: The rootkit is saved as obfuscated information within the registry and is spawned with EnergyShell by way of Task Scheduler to be injected into the winlogon.exe course of.
- Child course of hooking.
- Option to embed further malware to be executed with the rootkit – on this case NirCmd and/or Quasar. The added malware will likely be decompressed and decrypted earlier than it’s injected into different processes.
- In reminiscence course of injection: the rootkit injects itself and extra malware(s) into all processes. Injection is completed from reminiscence: no recordsdata are wanted to be saved on disk.
- Hooking: Hooks a number of features from ntdll.dll to cover its presence.
- Communicating by way of NamedPipe: The rootkit can obtain a command from any operating course of.
- Antivirus / EDR evasion: The rootkit makes use of a number of evasion methods:
- AMSI bypass: EnergyShell inline script patches “amsi.dll!AmsiScanBuffer” to at all times return “AMSI_RESULT_CLEAN”.
- DLL unhooking: Removes EDR hooks by loading a recent copy of “ntdll.dll” from disk to keep away from course of hollowing detection
- Hiding entities: Hiding all entities begins with a configurable prefix, which in SeroXen’s case its “$sxr”. This prefix hardens the visualization of the assault on the system, however eases attribution of the malware household in the course of the evaluation. The prefix is used to cover recordsdata, directories, NamedPipes, scheduled duties, processes, registry keys/values, and companies.
R77 technical documentation supplies a tenet of the place can the prefix be discovered:
|
Config parameter |
Details |
Example |
|
HIDE_PREFIX |
The prefix for name-based hiding (e.g. processes, recordsdata, and so forth…). |
L”$sxr” |
|
R77_SERVICE_NAME32 |
Name for the scheduled job that begins the r77 service for 32-bit processes. |
HIDE_PREFIX L”svc32″ |
|
R77_SERVICE_NAME64 |
Name for the scheduled job that begins the r77 service for 64-bit processes. |
HIDE_PREFIX L”svc64″ |
|
CHILD_PROCESS_PIPE_NAME32 |
Name for the named pipe that notifies the 32-bit r77 service about new youngster processes. |
L”\.pipe” HIDE_PREFIX L”childproc32″ |
|
CHILD_PROCESS_PIPE_NAME64 |
Name for the named pipe that notifies the 64-bit r77 service about new youngster processes. |
L”\.pipe” HIDE_PREFIX L”childproc64″ |
|
CONTROL_PIPE_NAME |
Name for the named pipe that receives instructions from exterior processes. |
L”\.pipe” HIDE_PREFIX L”management” |
The two major elements on this mission are the InstallStager service and the Rootkit. The InstallStager service is answerable for:
- Creating a registry key to retailer the malware code and writes it as encrypted information.
- Creating a scheduled job to execute the malware utilizing EnergyShell. EnergyShell will decompress and decrypt the ultimate payload (Service) that will likely be injected into the winlogon.exe course of and executed by way of dllhost.exe utilizing course of hollowing methods.
Figure 6. Starting payload after decryption utilizing course of hollowing.
Now the second and major stage of the Rootkit is able to begin. The service kicks off the load of the rootkit’s DLL that’s embedded as a useful resource and saves its configuration as a registry key. (In SeroXen case it is [HKEY_LOCAL_MACHINESOFTWARE$sxrconfig]).
The service creates 3 listener threads:
- NewProcessListener: Enumerates all operating processes and injects the rootkit when new processes are created.
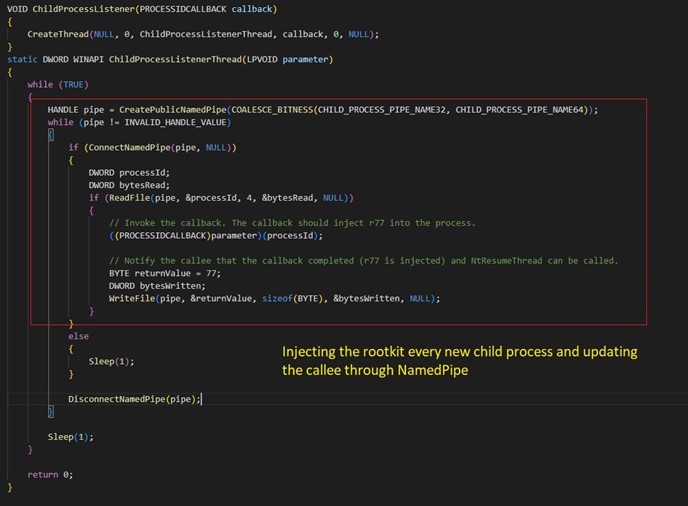
- ChildProcessListener: Injects the rootkit to a newly created course of by one other course of and updates the callee by way of NamedPipe.
Figure 7. Child course of injection.
- ControlPipeListener: Creates a NamedPipe to obtain instructions from any course of. Supported instructions are listed beneath:
|
Command |
Details |
|
CONTROL_R77_UNINSTALL |
The management code that uninstalls r77. |
|
CONTROL_R77_PAUSE_INJECTION |
The management code that briefly pauses injection of recent processes. |
|
CONTROL_R77_RESUME_INJECTION |
The management code that resumes injection of recent processes. |
|
CONTROL_PROCESSES_INJECT |
The management code that injects r77 into a selected course of, if it isn’t but injected. |
|
CONTROL_PROCESSES_INJECT_ALL |
The management code that injects r77 into all processes that aren’t but injected. |
|
CONTROL_PROCESSES_DETACH |
The management code detaches r77 from a selected course of. |
|
CONTROL_PROCESSES_DETACH_ALL |
The management code detaches r77 from all processes. |
|
CONTROL_USER_SHELLEXEC |
The management code that executes a file utilizing ShellExecute. |
|
CONTROL_USER_RUNPE |
The management code that executes an executable utilizing course of hollowing. |
|
CONTROL_SYSTEM_BSOD |
The management code that triggers a BSOD. |
|
CONTROL_R77_TERMINATE_SERVICE |
The management code that terminates the r77 service. |
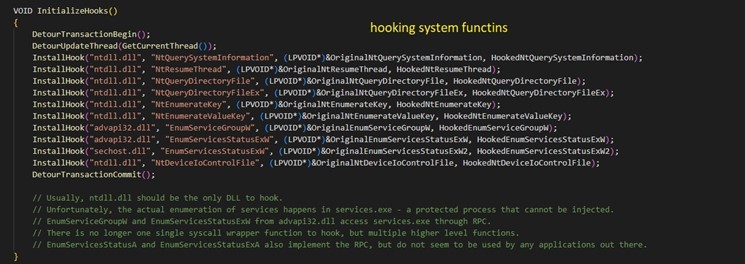
The DLL rootkit carries out course of injections, executes instructions acquired by different processes, and retains out of sight any signal of SeroXen being executed inside the system.
Figure 8. System perform hooking.
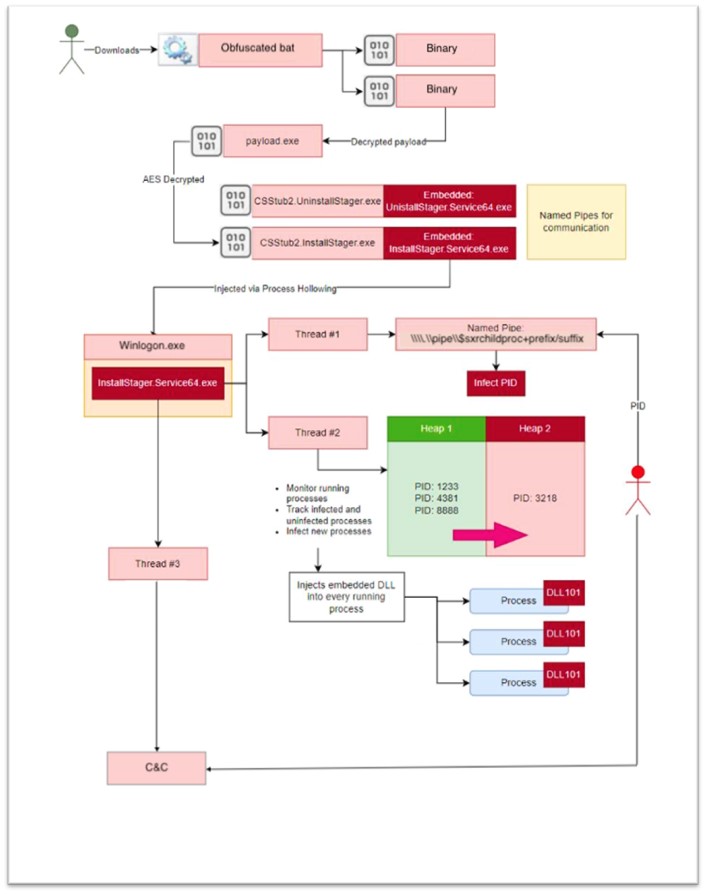
As a abstract of the execution course of:
Figure 9. SeroXen decryption move.
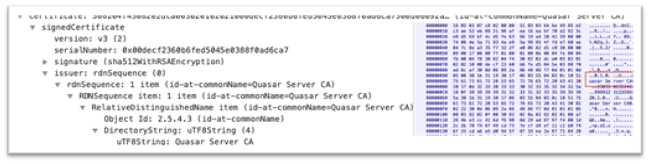
Since Seroxen is predicated on QuasarRAT, the C&C server makes use of the identical Common Name of their TLS certificates. The functionalities supplied by the menace actor for the C&C server carefully mirror these discovered within the Quasar Github repository, together with assist for TCP community streams (each IPv4 and IPv6), environment friendly community serialization, compression utilizing QuickLZ, and safe communication by way of TLS encryption.
Figure 10. Quasar Server Certificate.
Conclusion
The SeroXen developer has discovered a formidable mixture of free assets to develop a tough to detect in static and dynamic evaluation RAT. The use of an elaborated open-source RAT like Quasar, with nearly a decade since its first look, makes an advantageous basis for the RAT. While the mix of NirCMD and r77-rootkit are logical additions to the combo, since they make the instrument extra elusive and tougher to detect.
The Alien Labs crew will proceed to watch the menace panorama for SeroXen samples and infrastructure.
Detection strategies
The following related detection strategies are in use by Alien Labs. They can be utilized by readers to tune or deploy detections in their very own environments or for aiding further analysis.
|
SURICATA IDS SIGNATURES |
|
2035595: ET TROJAN Generic AsyncRAT Style SSL Cert |
|
2027619: ET TROJAN Observed Malicious SSL Cert (Quasar CnC) |
Associated indicators (IOCs)
The following technical indicators are related to the reported intelligence. A listing of indicators can be out there within the OTX Pulse. Please be aware, the heart beat might embody different actions associated however out of the scope of the report.
|
TYPE |
INDICATOR |
DESCRIPTION |
|
SHA256 |
8ace121fae472cc7ce896c91a3f1743d5ccc8a389bc3152578c4782171c69e87 |
Example malware hash |
Mapped to MITRE ATT&CK
The findings of this report are mapped to the next MITRE ATT&CK Matrix methods:
- TA0002 : Execution
- T1053: Scheduled Task/Job
- T1053.005: Scheduled Task
- T1059: Command and Scripting Interpreter
- T1059.003: Windows Command Shell
- TA0003: Persistence
- T1547: Boot or Logon Autostart Execution
- T1547.001 Registry Run Keys / Startup Folder
- TA0004: Privilege Escalation
- T1548: Abuse Elevation Control Mechanism
- T1548.002: Bypass User Account Control
- TA0005: Defense Evasion
- T1112: Modify Registry
- T1553: Subvert Trust Controls
- T1553.002: Code Signing
- T1564: Hide Artifacts
- T1564.001: Hidden Files and Directories
- T1564.003: Hidden Window
- TA0006: Credential Access
- T1552: Unsecured Credentials
- T1552.001: Credentials In Files
- T1555: Credentials from Password Stores
- T1555.003: Credentials from Web Browsers
- TA0007: Discovery
- T1016: System Network Configuration Discovery
- T1033: System Owner/User Discovery
- T1082: System Information Discovery
- T1614: System Location Discovery
- TA0008: Lateral Movement
- T1021: Remote Services
- T1021.001: Remote Desktop Protocol
- TA009: Collection
- T1005: Data from Local System
- T1056: Input Capture
- T1056.001: Keylogging
- T1125: Video Capture
- TA0011: Command and Control
- T1090: Proxy
- T1095: Non-Application Layer Protocol
- T1105: Ingress Tool Transfer
- T1571: Non-Standard Port
- T1573: Encrypted Channel:
- T1573.001: Symmetric Cryptography