[ad_1]
First-year faculty college students are understandably annoyed once they can’t get into widespread upper-level electives. But they normally simply gripe. Paras Jha was an exception. Enraged that upper-class college students got precedence to enroll in a computer-science elective at Rutgers, the State University of New Jersey, Paras determined to crash the registration web site in order that nobody may enroll.
On Wednesday night time, 19 November 2014, at 10:00 p.m. EST—because the registration interval for first-year college students in spring programs had simply opened—Paras launched his first distributed denial-of-service (DDoS) assault. He had assembled a military of some 40,000 bots, primarily in Eastern Europe and China, and unleashed them on the Rutgers central authentication server. The botnet despatched hundreds of fraudulent requests to authenticate, overloading the server. Paras’s classmates couldn’t get by means of to register.
The subsequent semester Paras tried once more. On 4 March 2015, he despatched an electronic mail to the campus newspaper, The Daily Targum: “A while back you had an article that talked about the DDoS attacks on Rutgers. I’m the one who attacked the network.… I will be attacking the network once again at 8:15 pm EST.” Paras adopted by means of on his risk, knocking the Rutgers community offline at exactly 8:15 p.m.
On 27 March, Paras unleashed one other assault on Rutgers. This assault lasted 4 days and introduced campus life to a standstill. Fifty thousand college students, college, and employees had no laptop entry from campus.
On 29 April, Paras posted a message on Pastebin, an internet site widespread with hackers for sending nameless messages. “The Rutgers IT department is a joke,” he taunted. “This is the third time I have launched DDoS attacks against Rutgers, and every single time, the Rutgers infrastructure crumpled like a tin can under the heel of my boot.”
Paras was livid that Rutgers selected Incapsula, a small cybersecurity agency primarily based in Massachusetts, as its DDoS-mitigation supplier. He claimed that Rutgers selected the most cost effective firm. “Just to show you the poor quality of Incapsula’s network, I have gone ahead and decimated the Rutgers network (and parts of Incapsula), in the hopes that you will pick another provider that knows what they are doing.”
Paras’s fourth assault on the Rutgers community, going down throughout finals, prompted chaos and panic on campus. Paras reveled in his skill to close down a significant state college, however his final goal was to pressure it to desert Incapsula. Paras had began his personal DDoS-mitigation service, ProTraf Solutions, and wished Rutgers to choose ProTraf over Incapsula. And he wasn’t going to cease attacking his college till it switched.
A Hacker Forged in Minecraft
Paras Jha was born and raised in Fanwood, a leafy suburb in central New Jersey. When Paras was within the third grade, a trainer beneficial that he be evaluated for consideration deficit hyperactivity dysfunction, however his dad and mom didn’t observe by means of.
As Paras progressed by means of elementary college, his struggles elevated. Because he was so clearly clever, his academics and fogeys attributed his lackluster efficiency to laziness and apathy. His perplexed dad and mom pushed him even tougher.
Paras sought refuge in computer systems. He taught himself easy methods to code when he was 12 and was hooked. His dad and mom fortunately indulged this ardour, shopping for him a pc and offering him with unrestricted Internet entry. But their indulgence led Paras to isolate himself additional, as he spent all his time coding, gaming, and hanging out together with his on-line pals.
Paras was significantly drawn to the net sport Minecraft. In ninth grade, he graduated from enjoying Minecraft to internet hosting servers. It was in internet hosting sport servers that he first encountered DDoS assaults.
Minecraft server directors usually rent DDoS providers to knock rivals offline. As Paras discovered extra refined DDoS assaults, he additionally studied DDoS protection. As he grew to become proficient in mitigating assaults on Minecraft servers, he determined to create ProTraf Solutions.
Paras’s obsession with Minecraft assaults and protection, compounded by his untreated ADHD, led to a good larger retreat from household and college. His poor tutorial efficiency in highschool annoyed and depressed him. His solely solace was Japanese anime and the admiration he gained from the net neighborhood of Minecraft DDoS specialists.
Paras’s struggles deteriorated into paralysis when he enrolled in Rutgers, finding out for a B.S. in laptop science. Without his mom’s assist, he was unable to control the traditional calls for of dwelling on his personal. He couldn’t handle his sleep, schedule, or examine. Paras was additionally acutely lonely. So he immersed himself in hacking.
Paras and two hacker pals, Josiah White and Dalton Norman, determined to go after the kings of DDoS—a gang often known as VDoS. The gang had been offering these providers to the world for 4 years, which is an eternity in cybercrime. The resolution to combat skilled cybercriminals could appear courageous, however the trio had been really older than their rivals. The VDoS gang members had been solely 14 years previous once they began to supply DDoS providers from Israel in 2012. These 19-year-old American youngsters could be going to battle towards two 18-year-old Israeli youngsters. The warfare between the 2 teenage gangs wouldn’t solely change the character of malware. Their battle for dominance in our on-line world would create a doomsday machine.
Botnet Madness
Botnet malware is beneficial for financially motivated crime as a result of botmasters can inform the bots of their thrall to implant malware on weak machines, ship phishing emails, or have interaction in click on fraud, by which botnets revenue by directing bots to click on pay-per-click advertisements. Botnets are additionally nice DDoS weapons as a result of they are often skilled on a goal and barrage it from all instructions. One day in February 2000, for instance, the hacker MafiaBoy knocked out Fifa.com, Amazon.com, Dell, E-Trade, eBay, CNN, in addition to Yahoo, on the time the most important search engine on the Internet.
After taking so many main web sites offline, MafiaBoy was deemed a nationwide–safety risk. President Clinton ordered a nationwide manhunt to search out him. In April 2000, MafiaBoy was arrested and charged, and in January 2001 he pled responsible to 58 expenses of denial-of-service assaults. Law enforcement didn’t reveal MafiaBoy’s actual title, as this nationwide–safety risk was 15 years previous.
Both MafiaBoy and the VDoS crew had been adolescent boys who crashed servers. But whereas MafiaBoy did it for the game, VDoS did it for the cash. Indeed, these teenage Israeli youngsters had been pioneering tech entrepreneurs. They helped launch a brand new type of cybercrime: DDoS as a service. With it, anybody may now hack with the clicking of a button, no technical information wanted.
It is perhaps shocking that DDoS suppliers may promote brazenly on the Web. After all, DDoSing one other web site is unlawful in every single place. To get round this, these “booter services” have lengthy argued they carry out a professional perform: offering those that arrange Web pages a method to emphasize check web sites.
In principle, such providers do play an essential perform. But solely in principle. As a booter-service supplier admitted to University of Cambridge researchers, “We do try to market these services towards a more legitimate user base, but we know where the money comes from.”
The Botnets of August
Paras dropped out of Rutgers in his sophomore yr and, together with his father’s encouragement, spent the subsequent yr centered on constructing ProTraf Solutions, his DDoS-mitigation enterprise. And similar to a mafia don working a safety racket, he needed to make that safety wanted. After launching 4 DDoS assaults his freshman yr, he attacked Rutgers but once more in September 2015, nonetheless hoping that his former college would surrender on Incapsula. Rutgers refused to budge.
ProTraf Solutions was failing, and Paras wanted money. In May 2016, Paras reached out to Josiah White. Like Paras, Josiah frequented Hack Forums. When he was 15, he developed main parts of Qbot, a botnet worm that at its top in 2014 had enslaved half 1,000,000 computer systems. Now 18, Josiah switched sides and labored together with his buddy Paras at ProTraf doing DDoS mitigation.
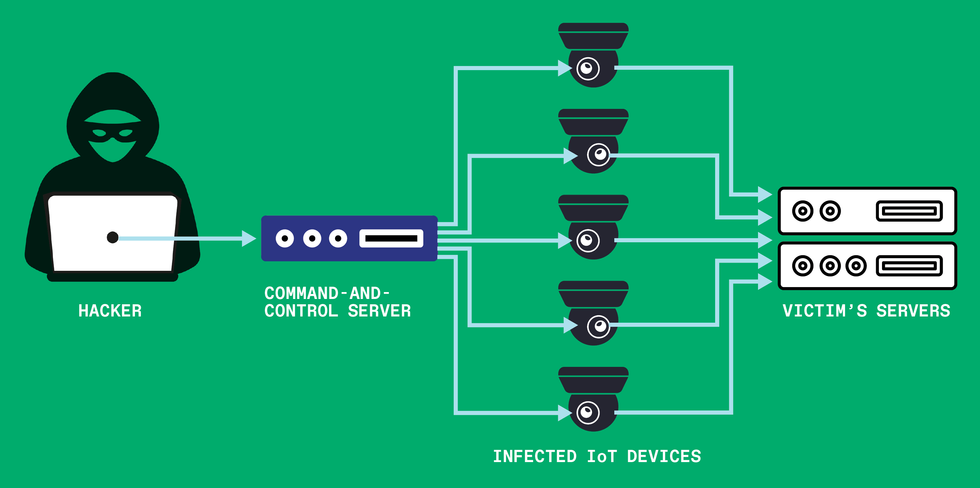 The hacker’s command-and-control (C2) server orchestrates the actions of many geographically distributed bots (computer systems underneath its management). Those computer systems, which could possibly be IoT units like IP cameras, could be directed to overwhelm the sufferer’s servers with undesirable site visitors, making them unable to answer professional requests.IEEE Spectrum
The hacker’s command-and-control (C2) server orchestrates the actions of many geographically distributed bots (computer systems underneath its management). Those computer systems, which could possibly be IoT units like IP cameras, could be directed to overwhelm the sufferer’s servers with undesirable site visitors, making them unable to answer professional requests.IEEE Spectrum
But Josiah quickly returned to hacking and began working with Paras to take the Qbot malware, enhance it, and construct an even bigger, extra highly effective DDoS botnet. Paras and Josiah then partnered with 19-year-old Dalton Norman. The trio changed into a well-oiled group: Dalton discovered the vulnerabilities; Josiah up to date the botnet malware to take advantage of these vulnerabilities; and Paras wrote the C2—software program for the command-and-control server—for controlling the botnet.
But the trio had competitors. Two different DDoS gangs—Lizard Squad and VDoS—determined to band collectively to construct an enormous botnet. The collaboration, often known as PoodleCorp, was profitable. The quantity of site visitors that could possibly be unleashed on a goal from PoodleCorp’s botnet hit a file worth of 400 gigabits per second, nearly 4 instances the speed that any earlier botnet had achieved. They used their new weapon to assault banks in Brazil, U.S. authorities websites, and Minecraft servers. They achieved this firepower by hijacking 1,300 Web-connected cameras. Web cameras are likely to have highly effective processors and good connectivity, and they’re hardly ever patched. So a botnet that harnesses video has huge cannons at its disposal.
While PoodleCorp was on the rise, Paras, Josiah, and Dalton labored on a brand new weapon. By the start of August 2016, the trio had accomplished the primary model of their botnet malware. Paras referred to as the brand new code Mirai, after the anime sequence Mirai Nikki.
When Mirai was launched, it unfold like wildfire. In its first 20 hours, it contaminated 65,000 units, doubling in dimension each 76 minutes. And Mirai had an unwitting ally within the botnet warfare then raging.
Up in Anchorage, Alaska, the FBI cyber unit was constructing a case towards VDoS. The FBI was unaware of Mirai or its warfare with VDoS. The brokers didn’t recurrently learn on-line boards reminiscent of Hack Forums. They didn’t know that the goal of their investigation was being decimated. The FBI additionally didn’t understand that Mirai was able to step into the void.
The head investigator in Anchorage was Special Agent Elliott Peterson. A former U.S. Marine, Peterson is a peaceful and confident agent with a buzz reduce of purple hair. At the age of 33, Peterson had returned to his native state of Alaska to prosecute cybercrime.
On 8 September 2016, the FBI’s Anchorage and New Haven cyber models teamed up and served a search warrant in Connecticut on the member of PoodleCorp who ran the C2 that managed all its botnets. On the identical day, the Israeli police arrested the VDoS founders in Israel. Suddenly, PoodleCorp was no extra.
The Mirai group waited a few days to evaluate the battlefield. As far as they might inform, they had been the one botnet left standing. And they had been prepared to make use of their new energy. Mirai gained the warfare as a result of Israeli and American regulation enforcement arrested the masterminds behind PoodleCorp. But Mirai would have triumphed anyway, because it was ruthlessly environment friendly in taking management of Internet of Things units and excluding competing malware.
A couple of weeks after the arrests of these behind VDoS, Special Agent Peterson discovered his subsequent goal: the Mirai botnet. In the Mirai case, we have no idea the precise steps that Peterson’s group took of their investigation: Court orders on this case are at the moment “under seal,” that means that the courtroom deems them secret. But from public reporting, we all know that Peterson’s group acquired its break within the standard approach—from a Mirai sufferer: Brian Krebs, a cybersecurity reporter whose weblog was DDoSed by the Mirai botnet on 25 September.
The FBI uncovered the IP deal with of the C2 and loading servers however didn’t know who had opened the accounts. Peterson’s group probably subpoenaed the internet hosting corporations to study the names, emails, cellphones, and cost strategies of the account holders. With this data, it will search courtroom orders after which search warrants to amass the content material of the conspirators’ conversations.
Still, the hunt for the authors of the Mirai malware should have been a troublesome one, given how intelligent these hackers had been. For instance, to evade detection Josiah didn’t simply use a VPN. He hacked the house laptop of a teenage boy in France and used his laptop because the “exit node.” The orders for the botnet, subsequently, got here from this laptop. Unfortunately for the proprietor, he was a giant fan of Japanese anime and thus match the profile of the hacker. The FBI and the French police found their mistake after they raided the boy’s home.
Done and Done For
After wielding its energy for 2 months, Paras dumped practically the whole supply code for Mirai on Hack Forums. “I made my money, there’s lots of eyes looking at IOT now, so it’s time to GTFO [Get The F*** Out],” Paras wrote. With that code dump, Paras had enabled anybody to construct their very own Mirai. And they did.
Dumping code is reckless, however commonplace. If the police discover supply code on a hacker’s units, they will declare that they “downloaded it from the Internet.” Paras’s irresponsible disclosure was a part of a false-flag operation meant to throw off the FBI, which had been gathering proof indicating Paras’s involvement in Mirai and had contacted him to ask questions. Though he gave the agent a fabricated story, getting a textual content from the FBI in all probability terrified him.
Mirai had captured the eye of the cybersecurity neighborhood and of regulation enforcement. But not till after Mirai’s supply code dropped would it not seize the eye of all the United States. The first assault after the dump was on 21 October, on Dyn, an organization primarily based in Manchester, N.H., that gives Domain Name System (DNS) decision providers for a lot of the East Coast of the United States.
![]() Mike McQuade
Mike McQuade
It started at 7:07 a.m. EST with a sequence of 25-second assaults, considered assessments of the botnet and Dyn’s infrastructure. Then got here the sustained assaults: of 1 hour, after which 5 hours. Interestingly, Dyn was not the one goal. Sony’s PlayStation video infrastructure was additionally hit. Because the torrents had been so immense, many different web sites had been affected. Domains reminiscent of cnn.com, fb.com, and nytimes.com wouldn’t work. For the overwhelming majority of those customers, the Internet grew to become unusable. At 7:00 p.m., one other 10-hour salvo hit Dyn and PlayStation.
Further investigations confirmed the purpose of the assault. Along with Dyn and PlayStation site visitors, the botnet focused Xbox Live and Nuclear Fallout game-hosting servers. Nation-states weren’t aiming to hack the upcoming U.S. elections. Someone was making an attempt as well gamers off their sport servers. Once once more—similar to MafiaBoy, VDoS, Paras, Dalton, and Josiah—the attacker was a teenage boy, this time a 15-year-old in Northern Ireland named Aaron Sterritt.
Meanwhile, the Mirai trio left the DDoS enterprise, simply as Paras stated. But Paras and Dalton didn’t surrender on cybercrime. They simply took up click on fraud.
Click fraud was extra profitable than working a booter service. While Mirai was now not as massive because it had been, the botnet may however generate important promoting income. Paras and Dalton earned as a lot cash in a single month from click on fraud as they ever made with DDoS. By January 2017, that they had earned over US $180,000, versus a mere $14,000 from DDoSing.
Had Paras and his pals merely shut down their booter service and moved on to click on fraud, the world would probably have forgotten about them. But by releasing the Mirai code, Paras created imitators. Dyn was the primary main copycat assault, however many others adopted. And because of the huge injury these imitators wrought, regulation enforcement was intensely within the Mirai authors.
After gathering data tying Paras, Josiah, and Dalton to Mirai, the FBI quietly introduced every as much as Alaska. Peterson’s group confirmed the suspects its proof and gave them the prospect to cooperate. Given that the proof was irrefutable, every folded.
Paras Jha was indicted twice, as soon as in New Jersey for his assault on Rutgers, and as soon as in Alaska for Mirai. Both indictments carried the identical cost—one violation of the Computer Fraud and Abuse Act. Paras confronted as much as 10 years in federal jail for his actions. Josiah and Dalton had been solely indicted in Alaska and so confronted 5 years in jail.
The trio pled responsible. At the sentencing listening to held on 18 September 2018, in Anchorage, every of the defendants expressed regret for his actions. Josiah White’s lawyer conveyed his consumer’s realization that Mirai was “a tremendous lapse in judgment.”
Unlike Josiah, Paras spoke on to Judge Timothy Burgess within the courtroom. Paras started by accepting full duty for his actions and expressed his deep remorse for the difficulty he’d prompted his household. He additionally apologized for the hurt he’d prompted companies and, particularly, Rutgers, the school, and his fellow college students.
The Department of Justice made the bizarre resolution to not ask for jail time. In its sentencing memo, the federal government famous “the divide between [the defendants’] online personas, where they were significant, well-known, and malicious actors in the DDoS criminal milieu and their comparatively mundane ‘real lives’ where they present as socially immature young men living with their parents in relative obscurity.” It beneficial 5 years of probation and a couple of,500 hours of neighborhood service.
The authorities had yet another request—for that neighborhood service “to include continued work with the FBI on cybercrime and cybersecurity matters.” Even earlier than sentencing, Paras, Josiah, and Dalton had logged near 1,000 hours serving to the FBI hunt and shut down Mirai copycats. They contributed to greater than a dozen regulation enforcement and analysis efforts. In one occasion, the trio assisted in stopping a nation-state hacking group. They additionally helped the FBI forestall DDoS assaults aimed toward disrupting Christmas-holiday procuring. Judge Burgess accepted the federal government’s advice, and the trio escaped jail time.
The most poignant moments within the listening to had been Paras’s and Dalton’s singling out for reward the very one who caught them. “Two years ago, when I first met Special Agent Elliott Peterson,” Paras instructed the courtroom, “I was an arrogant fool believing that somehow I was untouchable. When I met him in person for the second time, he told me something I will never forget: ‘You’re in a hole right now. It’s time you stop digging.’ ” Paras completed his remarks by thanking “my family, my friends, and Agent Peterson for helping me through this.”
From Your Site Articles
Related Articles Around the Web
