[ad_1]
SideWinder, a prolific nation-state actor primarily recognized for concentrating on Pakistan army entities, compromised the official web site of the National Electric Power Regulatory Authority (NEPRA) to ship a tailor-made malware referred to as WarHawk.
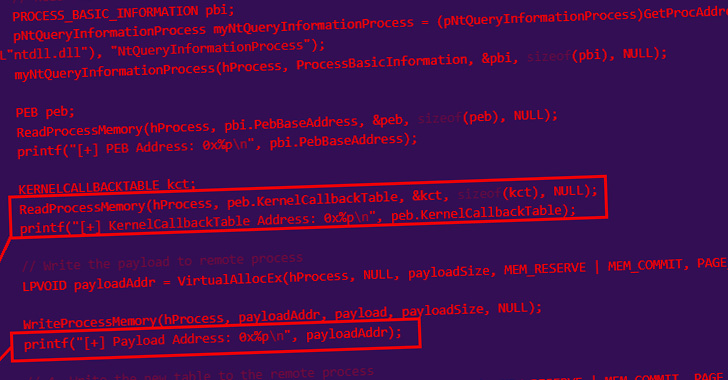
“The newly found WarHawk backdoor accommodates varied malicious modules that ship Cobalt Strike, incorporating new TTPs reminiscent of KernelCallBackTable injection and Pakistan Standard Time zone examine with the intention to guarantee a victorious marketing campaign,” Zscaler ThreatLabz mentioned.
The risk group, additionally referred to as APT-C-17, Rattlesnake, and Razor Tiger, is suspected to be an Indian state-sponsored group, though a report from Kaspersky earlier this May acknowledged earlier indicators that led to the attribution have since disappeared, making it difficult it to hyperlink the risk cluster to a selected nation.
More than 1,000 assaults are mentioned to have been launched by the group since April 2020, a sign of SideWinder’s newfound aggression because it commenced operations a decade in the past in 2012.
The intrusions have been vital not solely with regard to their frequency but in addition of their persistence, even because the group takes benefit of an enormous arsenal of obfuscated and newly-developed parts.
In June 2022, the risk actor was discovered leveraging an AntiBot script that is designed to filter their victims to examine the consumer browser surroundings, particularly the IP handle, to make sure the targets are positioned in Pakistan.
The September marketing campaign noticed by Zscaler entails using a weaponized ISO file hosted on NEPRA’s web site to activate a killchain that results in the deployment of the WarHawk malware, with the artifact additionally performing as a decoy to cover the malicious exercise by displaying a official advisory issued by the Cabinet Division of Pakistan on July 27, 2022.
WarHawk, for its half, masquerades as official apps reminiscent of ASUS Update Setup and Realtek HD Audio Manager to lure unsuspecting victims into execution, ensuing the exfiltration of system metadata to a hard-coded distant server, whereas additionally receiving further payloads from the URL.
This features a command execution module that is liable for the execution of system instructions on the contaminated machine acquired from the command-and-control server, a file supervisor module that recursively enumerates recordsdata current in several drives, and an add module that transmits recordsdata of curiosity to the server.
Also deployed as a second-stage payload utilizing the aforementioned command execution module is a Cobalt Strike Loader, which validates the host’s time zone to substantiate it matches the Pakistan Standard Time (PKT), failing which the method is terminated.
Following the anti-anThe loader injects shellcode right into a notepad.exe course of utilizing a way referred to as KernelCallbackTable course of injection, with the malware writer lifting supply code from a technical write-up revealed in April 2022 by a researcher who goes by the net alias Capt. Meelo.
The shellcode then decrypts and hundreds Beacon, the default malware payload utilized by Cobalt Strike to ascertain a connection to its command-and-control server.
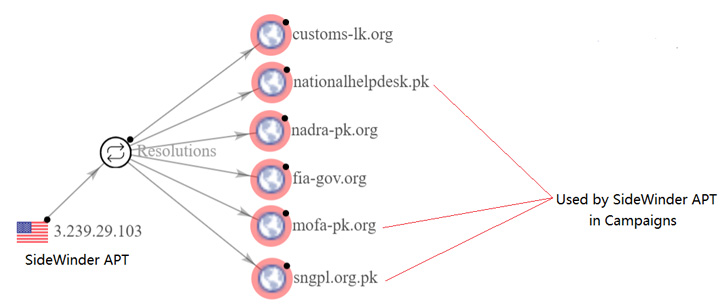
Per the cybersecurity firm, the assault marketing campaign’s connections to the SideWinder APT stem from the reuse of community infrastructure that has been recognized as utilized by the group in prior espionage-focused actions towards Pakistan.
“The SideWinder APT Group is repeatedly evolving their ways and including new malware to their arsenal with the intention to perform profitable espionage assault campaigns towards their targets,” the researchers concluded.