[ad_1]
cyberstress.org seizure banner (DOJ)
The U.S. Justice Department introduced immediately the seizure of 13 extra domains linked to DDoS-for-hire platforms, also called ‘booter’ or ‘stressor’ providers.
This week’s seizures are a part of a coordinated worldwide legislation enforcement effort (often known as Operation PowerOFF) to disrupt on-line platforms permitting anybody to launch huge distributed denial-of-service (DDoS) assaults towards any goal for the appropriate amount of cash.
“As a part of an ongoing initiative concentrating on pc assault ‘booter’ providers, the Justice Department immediately introduced the court-authorized seizure of 13 web domains related to these DDoS-for-hire providers,” the Department of Justice mentioned.
“The seizures this week are the third wave of U.S. legislation enforcement actions towards distinguished booter providers that allowed paying customers to launch highly effective distributed denial-of-service, or DDoS, assaults that flood focused computer systems with info and stop them from having the ability to entry the web.”
The FBI additionally focused prime stresser providers in December 2022 when it seized one other 48 domains, with ten beforehand disrupted platforms registering new domains, permitting them to remain on-line.
“Ten of the 13 domains seized immediately are reincarnations of providers that had been seized throughout a previous sweep in December, which focused 48 prime booter providers,” the DOJ mentioned.
“For instance, one of many domains seized this week – cyberstress.org – seems to be the identical service operated below the area cyberstress.us, which was seized in December.”
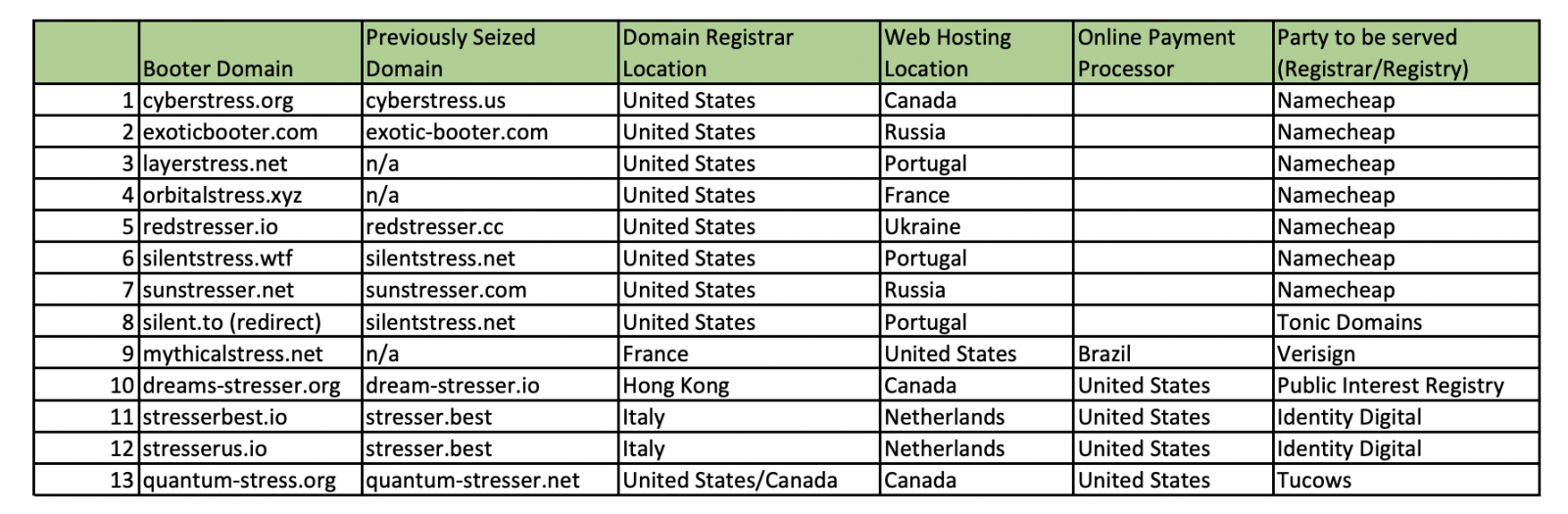
The full checklist of domains taken down this week by the FBI and beforehand seized domains linked to the identical operations is embedded under.
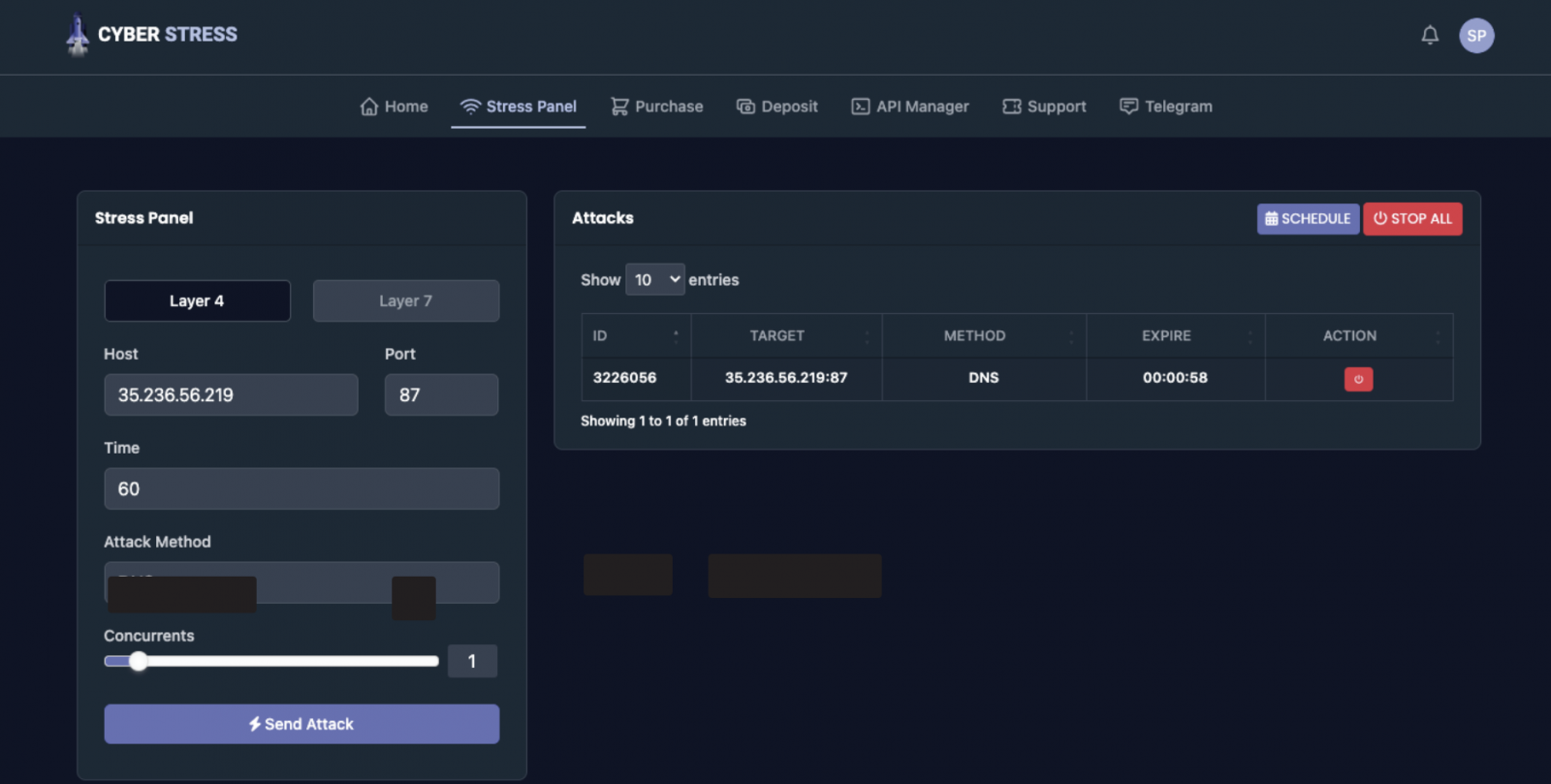
According to the affidavit, the FBI examined the booter providers whose domains had been seized by opening or renewing accounts with every of them and assessed the results on track computer systems by way of DDoS assaults launched on computer systems managed by the company.
These assessments helped affirm the booters’ performance, with the FBI saying that some assaults took the focused gadgets offline regardless that they had been utilizing high-capacity Internet connections.
“The FBI examined every of providers related to the SUBJECT DOMAINS, that means that brokers or different personnel visited every of the web sites and both used earlier login info or registered a brand new account on the service to conduct assaults,” FBI Special Agent Elliott Peterson mentioned.
“I imagine that every of the SUBJECT DOMAINS is getting used to facilitate the fee of assaults towards unwitting victims to stop the victims from accessing the Internet, to disconnect the sufferer from or degrade communication with established Internet connections, or to trigger different related harm.”
Four defendants charged in late 2022 additionally pleaded responsible earlier this 12 months to federal expenses, admitting that they had been both concerned in or operated a number of the booter providers focused by legislation enforcement.
The checklist of defendants and the fees they pleaded responsible to consists of:
- Jeremiah Sam Evans Miller, aka “John The Dev,” 23, of San Antonio, Texas, admitted on April 6 to conspiracy and violating the pc fraud and abuse act associated to the operation of a booter service named RoyalStresser.com (previously often known as Supremesecurityteam.com);
- Angel Manuel Colon Jr., aka “Anonghost720” and “Anonghost1337,” 37, of Belleview, Florida, pleaded responsible on February 13 to conspiracy and violating the pc fraud and abuse act associated to the operation of a booter service named SecurityTeam.io;
- Shamar Shattock, 19, of Margate, Florida, pleaded responsible on March 22 to conspiracy to violate the pc fraud and abuse act associated to the operation of a booter service often known as Astrostress.com; and
- Cory Anthony Palmer, 23, of Lauderhill, Florida, pleaded responsible on February 16 to conspiracy to violate the pc fraud and abuse act associated to the operation of a booter service often known as Booter.sx.
Law enforcement’s current seizures present their dedication to concentrating on booter service platforms, regardless that some beforehand taken down domains have resurfaced.
