[ad_1]

An enormous, malicious marketing campaign is underway utilizing over 200 typosquatting domains that impersonate twenty-seven manufacturers to trick guests into downloading numerous Windows and Android malware.
Typosquatting is an outdated methodology of tricking individuals into visiting a pretend web site by registering a site identify much like that utilized by real manufacturers.
The domains used on this marketing campaign are very near the genuine ones, that includes a single letter place swap or an extra “s,” making them simple for individuals to overlook.
In phrases of look, generally seen by BleepingComputer, the malicious web sites are clones of the originals or a minimum of convincing sufficient, so there’s not a lot to offer away the fraud.
Victims usually find yourself on these websites by mistyping the web site identify they wish to go to within the browser’s URL bar, which isn’t unusual when typing on cell.
However, customers is also led on these websites by way of phishing emails or SMS, direct messages, malicious social media and discussion board posts, and different methods.
An unlimited community of pretend websites
Some of the malicious websites have been found by cyber-intelligence agency Cyble, which printed a report this week specializing in domains mimicking common Android app shops like Google Play, APKCombo, and APKPure, in addition to obtain portals for PayPal, VidMate, Snapchat, and TikTook.
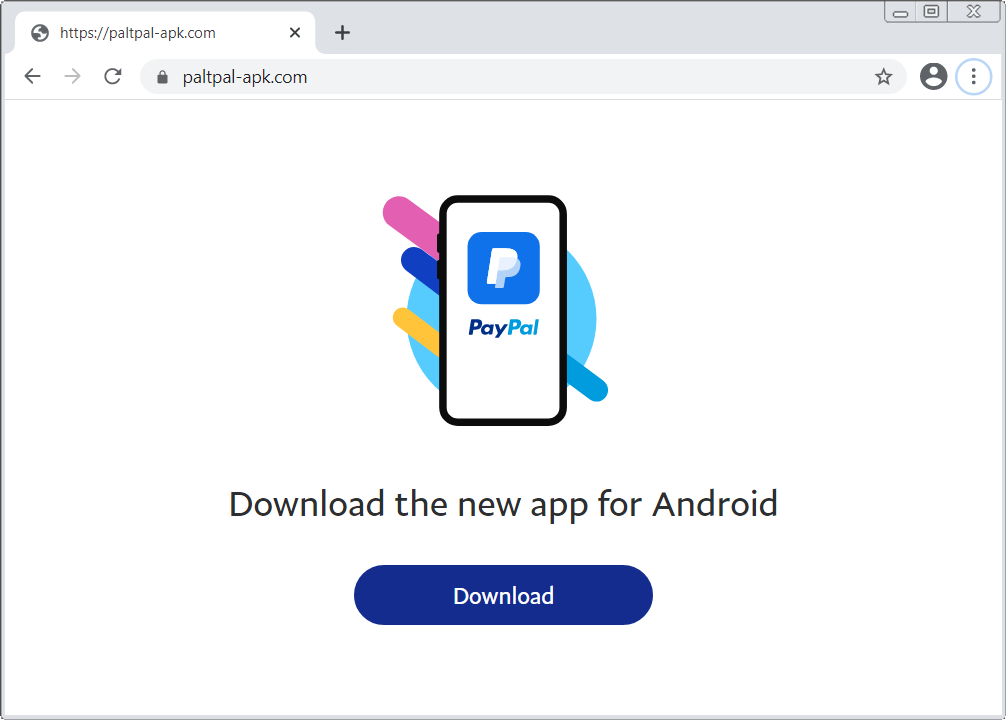
Some of the domains used for this function are:
- payce-google[.]com – impersonates Google Wallet
- snanpckat-apk[.]com – impersonates Snapchat
- vidmates-app[.]com – impersonates VidMate
- paltpal-apk[.]com – impersonates PayPal
- m-apkpures[.]com – impersonates APKPure
- tlktok-apk[.]hyperlink – impersonates obtain portal for TikTook app
In all these instances, the malware delivered to customers making an attempt to obtain the APKs is ERMAC, a banking trojan concentrating on banking accounts and cryptocurrency wallets from 467 apps.
Part of a a lot bigger marketing campaign
While Cyble’s report targeted on the marketing campaign’s Android malware, BleepingComputer discovered a a lot bigger typosquatting marketing campaign from the identical operators, distributing Windows malware.
This marketing campaign consists of over 90 web sites created to impersonate over twenty-seven common manufacturers to distribute Windows malware, steal cryptocurrency restoration keys, and, as described above, push Android malware.
| Category | Impersonated Brands |
| Mobile Apps & Services | TikTook Vidmate SnapChat Paypal APK Pure APKCombo Google Wallet |
| Software | Microsoft Visual Studio Brave Browser ThunderBird Notepad+ Tor Browser |
| Cryptocurrency | TronLink MetaMask Phantom Cosmos Wallet Mintable Ethermine GenoPets |
| Crypto and Stock buying and selling | Trading View IQ Option NinjaTrader Tiger.Trade |
| Web websites | Figma Quatro Casinos Big Time CS:Money |
A notable instance of certainly one of these typosquat websites is for the extremely popular Notepad++ textual content editor. This pretend website makes use of the area “notepads-plus-plus[.]org”, which is barely a personality away from the genuine at “notepad-plus-plus.org”.
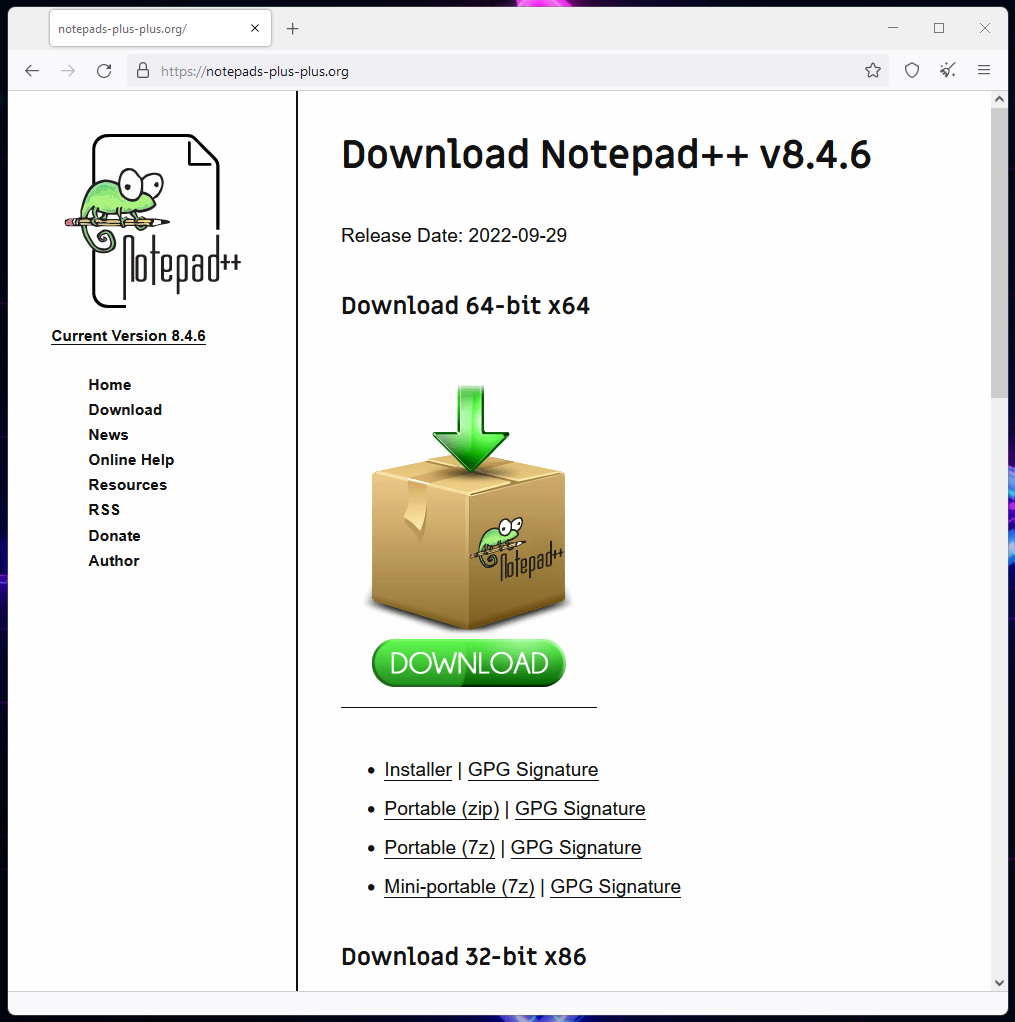
The information from this website set up the Vidar Stealer information-stealing malware, which has had its measurement inflated to 700MB to evade evaluation.
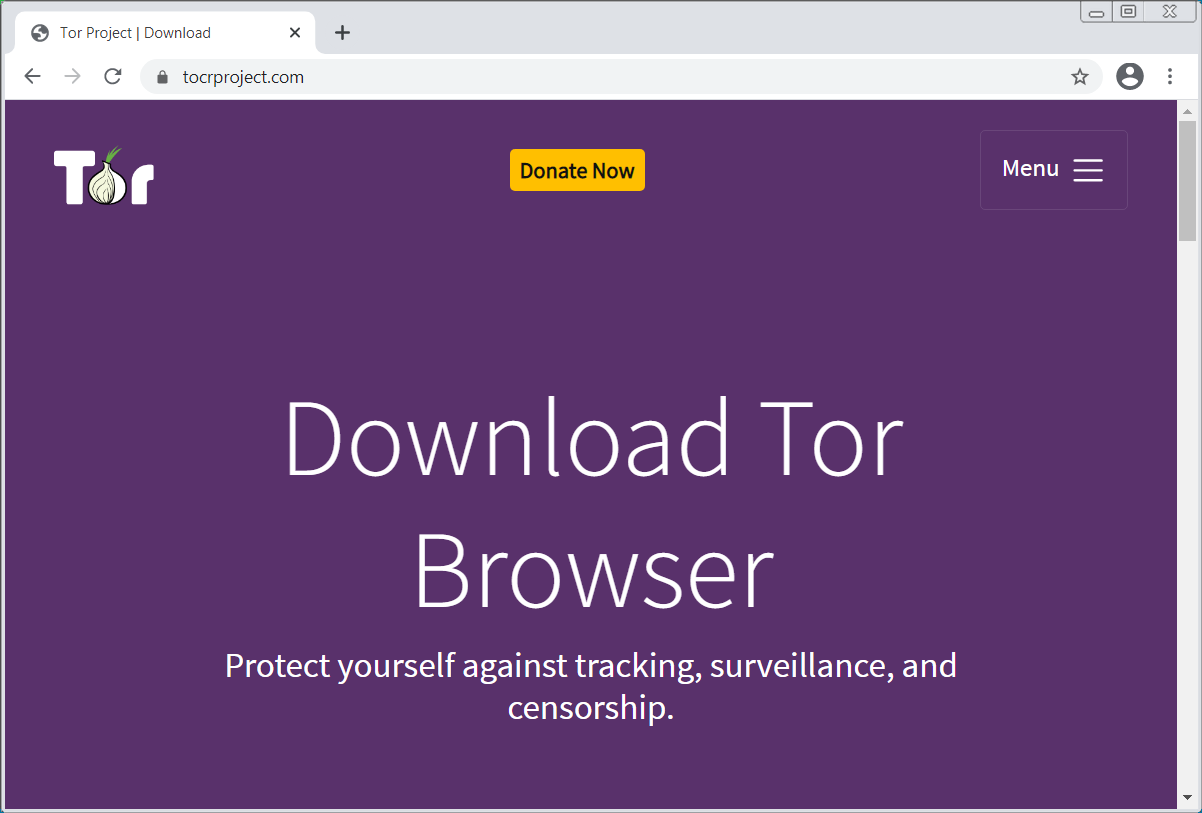
Another website found by BleepingComputer impersonates the Tor Project utilizing the “tocproject.com” area. In this case, the web site drops the Agent Tesla keylogger and RAT.
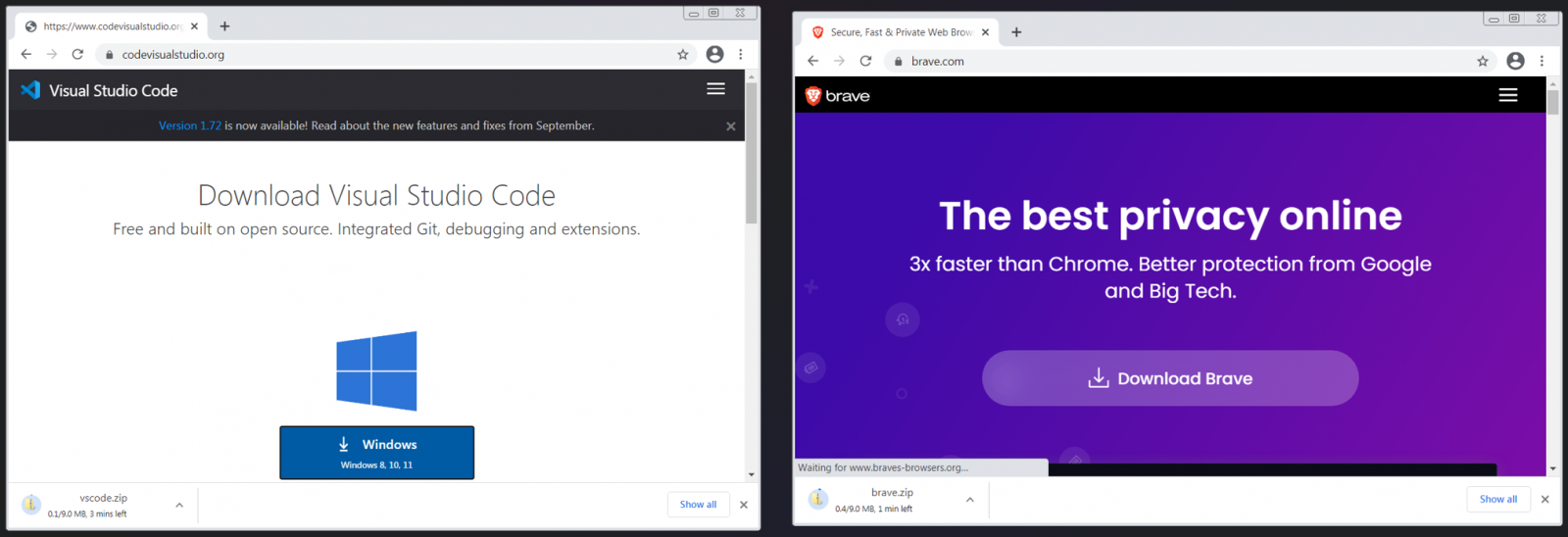
By digging deeper into the lengthy listing of the domains, we have discovered a number of concentrating on common software program like:
- thundersbird[.]org – Impersonates the favored Thunderbird open-source e-mail suite, dropping Vidar Stealer
- codevisualstudio[.]org – Impersonates Microsoft’s Visual Studio Code to drop Vidar
- braves-browsers[.]org – Impersonates the Brave internet browser to drop Vidar
The selection within the malware households delivered to victims could point out that the marketing campaign operators experiment with numerous strains to see what works greatest.
Another portion of those websites goal cryptocurrency wallets and seed phrases, a really worthwhile exercise for risk actors.
For instance, BleepingComputer discovered “ethersmine[.]com”, which makes an attempt to steal the customer’s Ethereum pockets seed phrase.
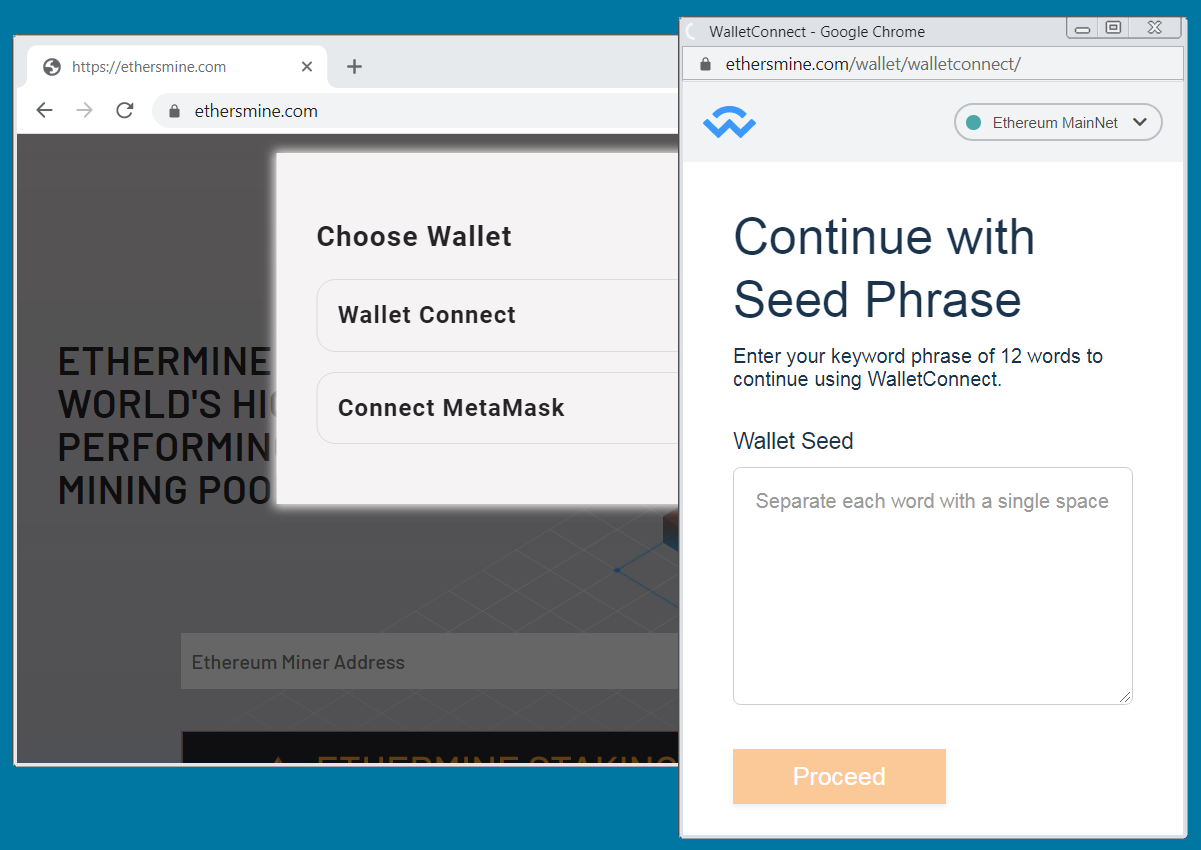
Other websites within the marketing campaign goal cryptocurrency holders and digital asset buyers impersonating common crypto wallets, buying and selling apps, and NFT websites.
Of course, the risk actors use a number of variants of every area to cowl as many mistypes as doable, so these domains are solely a small pattern of the whole community of domains used within the marketing campaign.
Some browsers like Google Chrome and Microsoft Edge embody typosquatting safety. However, in our exams, the browsers didn’t block any of the domains we examined.
To shield your self from typosquatting domains, the most effective methodology to discover a professional website is to seek for a specific model in a search engine.
However, you need to keep away from clicking on advertisements proven in search outcomes, as there have been many instances the place malicious advertisements are created to impersonate an actual website.
