[ad_1]
A brand new Android subscription malware named Fleckpe has been unearthed on the Google Play Store, amassing greater than 620,000 downloads in complete since 2022.
Kaspersky, which recognized 11 apps on the official app storefront, mentioned the malware masqueraded as official picture modifying apps, digital camera, and smartphone wallpaper packs. The apps have since been taken down.
The operation primarily focused customers from Thailand, though telemetry information gathered by the Russian cybersecurity agency has revealed victims in Poland, Malaysia, Indonesia, and Singapore.
The apps supply the promised performance to keep away from elevating pink flags, however conceal their actual goal underneath the hood. The listing of the offending apps is as follows –
- Beauty Camera Plus (com.magnificence.digital camera.plus.photoeditor)
- Beauty Photo Camera (com.apps.digital camera.pictures)
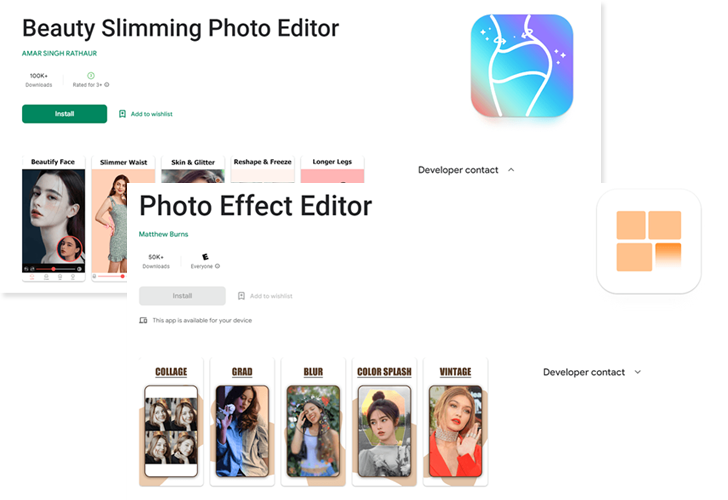
- Beauty Slimming Photo Editor (com.magnificence.slimming.professional)
- Fingertip Graffiti (com.draw.graffiti)
- GIF Camera Editor (com.gif.digital camera.editor)
- HD 4K Wallpaper (com.hd.h4ks.wallpaper)
- Impressionism Pro Camera (com.impressionism.prozs.app)
- Microclip Video Editor (com.microclip.vodeoeditor)
- Night Mode Camera Pro (com.urox.opixe.nightcamreapro)
- Photo Camera Editor (com.toolbox.photoeditor)
- Photo Effect Editor (com.image.pictureframe)
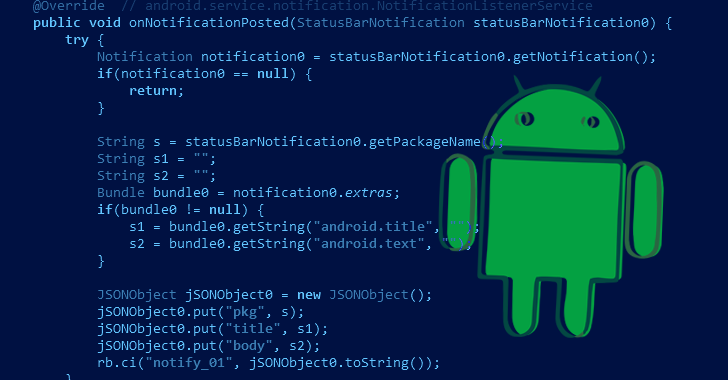
“When the app begins, it masses a closely obfuscated native library containing a malicious dropper that decrypts and runs a payload from the app property,” Kaspersky researcher Dmitry Kalinin mentioned.
The payload, for its half, is designed to contact a distant server and transmit details about the compromised system (e.g., Mobile Country Code and Mobile Network Code), following which the server responds again with a paid subscription web page.
The malware subsequently opens the web page in an invisible internet browser window and makes an attempt to subscribe on the person’s behalf by abusing its permissions to entry notifications and procure the affirmation code required to finish the step.
In an indication that Fleckpe is being actively developed, current variations of the malware have moved a lot of the malicious performance to the native library in a bid to evade detection by safety instruments.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and discover ways to cease ransomware assaults of their tracks with real-time MFA and repair account safety.
“The payload now solely intercepts notifications and views internet pages, performing as a bridge between the native code and the Android elements required for buying a subscription,” Kalinin famous.
“Unlike the native library, the payload has subsequent to no evasion capabilities, though the malicious actors did add some code obfuscation to the newest model.”
This is just not the primary time subscription malware has been discovered on the Google Play Store. Fleckpe joins different fleeceware households like Joker (aka Bread or Jocker) and Harly, which subscribe contaminated units to undesirable premium companies and conduct billing fraud.
While such apps are usually not as harmful as spyware and adware or monetary trojans, they’ll nonetheless incur unauthorized expenses and be repurposed by its operators to reap a variety of delicate info and function entry factors for extra nefarious malware.
If something, the findings are one more indication that risk actors are persevering with to find new methods to sneak their apps onto official app marketplaces to scale their campaigns, requiring that customers train warning when downloading apps and granting permissions to them.
“Growing complexity of the trojans has allowed them to efficiently bypass many anti-malware checks carried out by the marketplaces, remaining undetected for lengthy intervals of time,” Kalinin mentioned.