[ad_1]
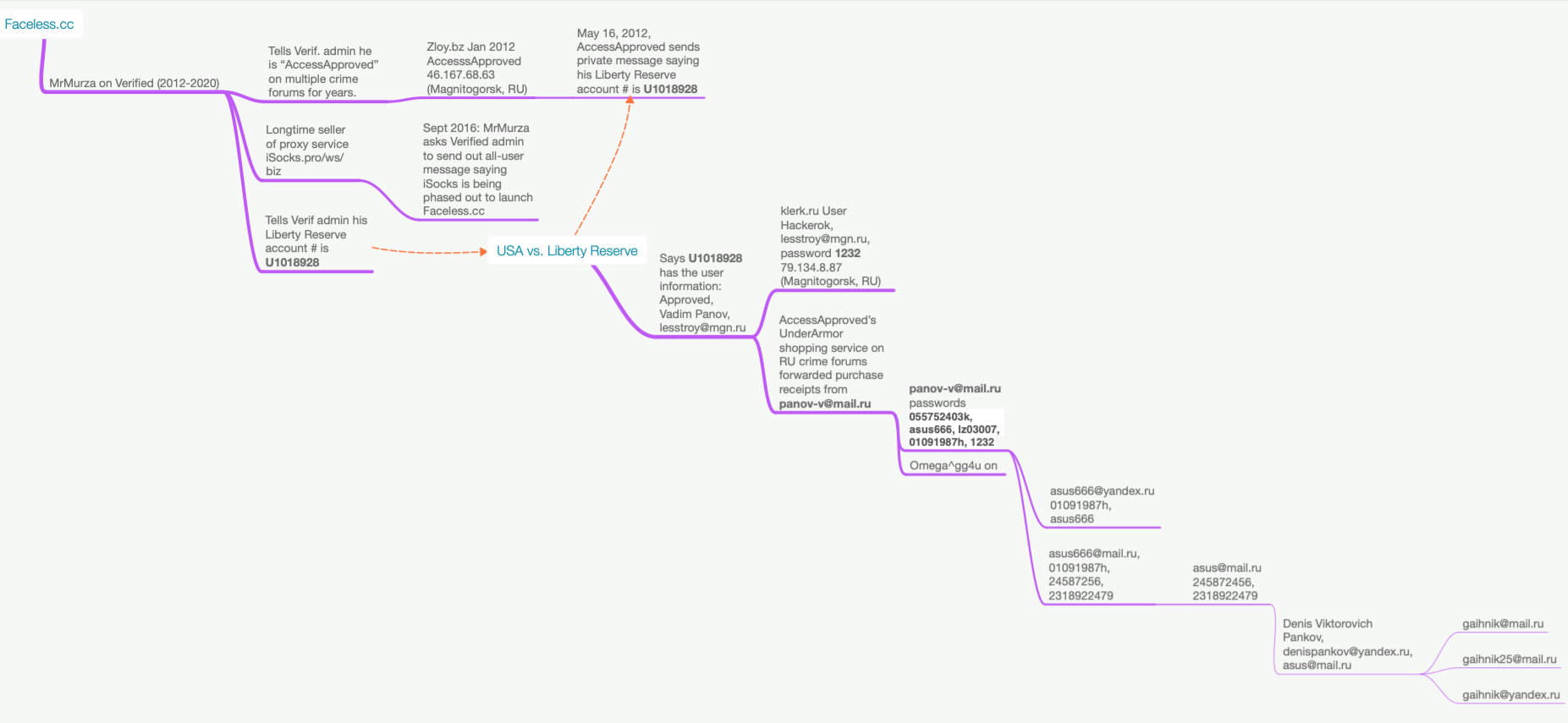
For the previous seven years, a malware-based proxy service generally known as “Faceless” has bought anonymity to numerous cybercriminals. For lower than a greenback per day, Faceless clients can route their malicious site visitors by means of tens of 1000’s of compromised methods marketed on the service. In this publish we’ll look at clues left behind over the previous decade by the proprietor of Faceless, together with some that will assist put a face to the title.
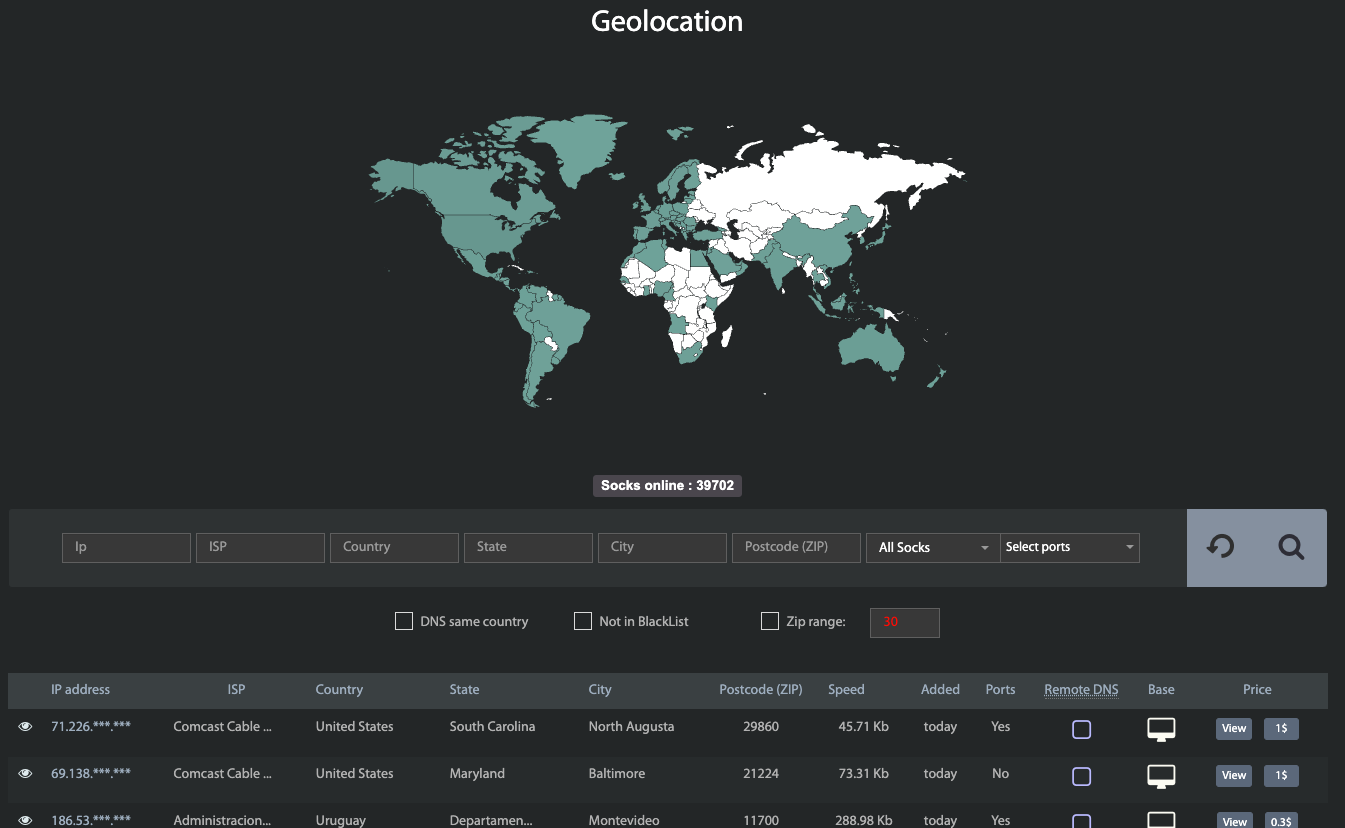
The proxy lookup web page contained in the malware-based anonymity service Faceless. Image: spur.us.
Riley Kilmer is co-founder of Spur.us, an organization that tracks 1000’s of VPN and proxy networks, and helps clients establish site visitors coming by means of these anonymity companies. Kilmer stated Faceless has emerged as one of many underground’s most dependable malware-based proxy companies, primarily as a result of its proxy community has historically included a fantastic many compromised “Internet of Things” gadgets — reminiscent of media sharing servers — which are seldom included on malware or spam block lists.
Kilmer stated when Spur first began trying into Faceless, they observed virtually each Internet tackle that Faceless marketed for hire additionally confirmed up within the IoT search engine Shodan.io as a media sharing gadget on an area community that was by some means uncovered to the Internet.
“We could reliably look up the [fingerprint] for these media sharing devices in Shodan and find those same systems for sale on Faceless,” Kilmer stated.
In January 2023, the Faceless service web site stated it was prepared to pay for details about beforehand undocumented safety vulnerabilities in IoT gadgets. Those with IoT zero-days might count on cost if their exploit concerned a minimum of 5,000 methods that could possibly be recognized by means of Shodan.
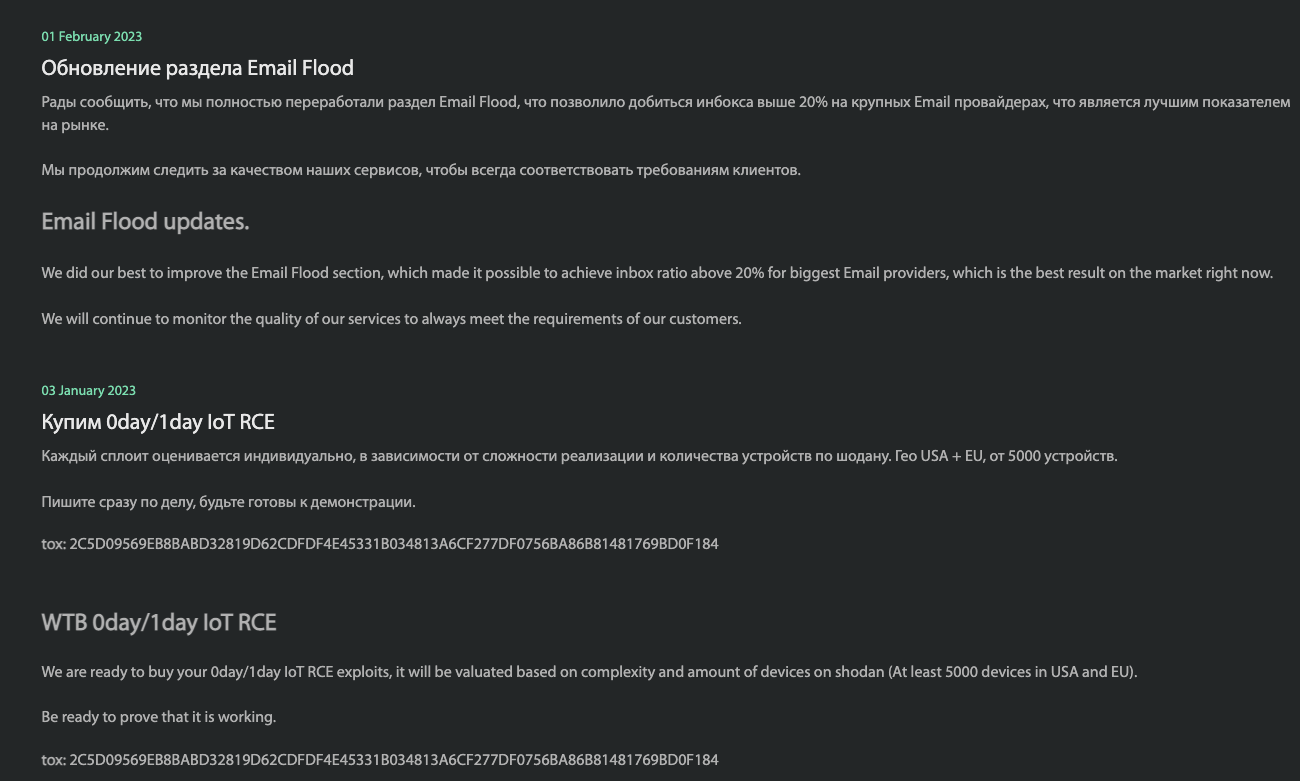
Notices posted for Faceless customers, promoting an e mail flooding service and soliciting zero-day vulnerabilities in Internet of Things gadgets.
Recently, Faceless has proven ambitions past simply promoting entry to poorly-secured IoT gadgets. In February, Faceless re-launched a service that lets customers drop an e mail bomb on somebody — inflicting the goal’s inbox to be crammed with tens of 1000’s of junk messages.
And in March 2023, Faceless began advertising a service for trying up Social Security Numbers (SSNs) that claims to supply entry to “the largest SSN database on the market with a very high hit rate.”
Kilmer stated Faceless desires to turn into a one-stop-fraud-shop for cybercriminals who’re searching for stolen or artificial identities from which to transact on-line, and a short lived proxy that’s geographically near the identification being bought. Faceless presently sells this bundled product for $9 — $8 for the identification and $1 for the proxy.
“They’re trying to be this one-stop shop for anonymity and personas,” Kilmer stated. “The service basically says ‘here’s an SSN and proxy connection that should correspond to that user’s location and make sense to different websites.’”
MRMURZA
Faceless is a venture from MrMurza, a very talkative member of greater than a dozen Russian-language cybercrime boards over the previous decade. According to cyber intelligence agency Flashpoint, MrMurza has been lively within the Russian underground since a minimum of September 2012. Flashpoint stated MrMurza seems to be extensively concerned in botnet exercise and “drops” — fraudulent financial institution accounts created utilizing stolen identification information which are usually utilized in cash laundering and cash-out schemes.
Faceless grew out of a well-liked anonymity service referred to as iSocks, which was launched in 2014 and marketed on a number of Russian crime boards as a proxy service that clients might use to route their malicious Web site visitors by means of compromised computer systems.
Flashpoint says that within the months earlier than iSocks went on-line, MrMurza posted on the Russian language crime discussion board Verified asking for a severe associate to help in opening a proxy service, noting that they had a botnet that was powered by malware that collected proxies with a 70 % an infection charge.
MrMurza’s Faceless marketed on the Russian-language cybercrime discussion board ProCrd. Image: Darkbeast/Ke-la.com.
In September 2016, MrMurza despatched a message to all iSocks customers saying the service would quickly be phased out in favor of Faceless, and that current iSocks customers might register at Faceless free of charge in the event that they did so rapidly — earlier than Faceless started charging new customers registration charges between $50 and $100.
Verified and different Russian language crime boards the place MrMurza had a presence have been hacked through the years, with contact particulars and personal messages leaked on-line. In a 2014 personal message to the administrator of Verified explaining his bona fides, MrMurza stated he acquired years of optimistic suggestions as a vendor of stolen Italian bank cards and a vendor of drops companies.
MrMurza instructed the Verified admin that he used the nickname AccessApproved on a number of different boards through the years. MrMurza additionally instructed the admin that his account quantity on the now-defunct digital foreign money Liberty Reserve was U1018928.
According to cyber intelligence agency Intel 471, the consumer AccessApproved joined the Russian crime discussion board Zloy in Jan. 2012, from an Internet tackle in Magnitogorsk, RU. In a 2012 personal message the place AccessApproved was arguing with one other cybercriminal over a deal gone dangerous, AccessApproved requested to be paid on the Liberty Reserve tackle U1018928.
In 2013, U.S. federal investigators seized Liberty Reserve and charged its founders with facilitating billions of {dollars} in cash laundering tied to cybercrime. The Liberty Reserve case was prosecuted out of the Southern District of New York, which in 2016 printed an inventory of account data (PDF) tied to 1000’s of Liberty Reserve addresses the federal government asserts have been concerned in cash laundering.
That doc signifies the Liberty Reserve account claimed by MrMurza/AccessApproved — U1018928 — was assigned in 2011 to a “Vadim Panov” who used the e-mail tackle lesstroy@mgn.ru.
PANOV
Constella Intelligence, a risk intelligence agency that tracks breached databases, says lesstroy@mgn.ru was used for an account “Hackerok” on the accounting service klerk.ru that was created from an Internet tackle in Magnitogorsk. The password chosen by this consumer was “1232.”
In addition to promoting entry to hacked computer systems and financial institution accounts, each MrMurza and AccessApproved ran facet hustles on the crime boards promoting clothes from fashionable retailers that refused to ship on to Russia.
On one cybercrime discussion board the place AccessApproved had clothes clients, denizens of the discussion board created a prolonged dialogue thread to assist customers establish incoming emails related to numerous reshipping companies marketed inside their neighborhood. Reshippers are likely to depend on numerous folks within the United States and Europe serving to to ahead packages abroad, however in lots of circumstances the notifications about purchases and delivery particulars can be forwarded to reshipping service clients from a constant e mail account.
That thread stated AccessApproved’s clothes reshipping service forwarded affirmation emails from the tackle panov-v@mail.ru. This tackle is related to accounts on two Russian cybercrime boards registered from Magnitogorsk in 2010 utilizing the deal with “Omega^gg4u.”
This Omega^gg4u identification bought software program that may quickly examine the validity of huge batches of stolen bank cards. Interestingly, each Omega^gg4u and AccessApproved additionally had one other area of interest: Reselling closely managed substances — reminiscent of human development hormone and anabolic steroids — from chemical suppliers in China.
A search in Constella on the tackle panov-v@mail.ru and lots of variations on that tackle exhibits these accounts cycled by means of the identical passwords, together with 055752403k, asus666, 01091987h, and the comparatively weak password 1232 (recall that 1232 was picked by whoever registered the lesstroy@mgn.ru account at Klerk.ru).
Constella says the e-mail tackle asus666@yandex.ru relied on the passwords asus666 and 01091987h. The 01091987h password additionally was utilized by asus666@mail.ru, which additionally favored the password 24587256.
Constella additional studies that whoever owned the a lot shorter tackle asus@mail.ru additionally used the password 24587256. In addition, it discovered the password 2318922479 was tied to each asus666@mail.ru and asus@mail.ru.
The e mail addresses asus@mail.ru, asus2504@mail.ru, and zaxar2504@rambler.ru have been all used to register Vkontakte social media accounts for a Denis ***@VIP*** Pankov. There are quite a few different Vkontakte accounts registered to asus@mail.ru and lots of variations of this tackle below a distinct title. But none of these different profiles seem tied to real-life identities.
PANKOV
Constella’s information exhibits the e-mail addresses asus2504@mail.ru and zaxar2504@rambler.ru used the quite distinctive password denis250485, which was additionally utilized by the e-mail tackle denispankov@yandex.ru and virtually a dozen variations at different Russian-language e mail suppliers.
Russian automobile registration information from 2016 present the e-mail tackle denispankov@yandex.ru belongs to Denis Viktorovich Pankov, born on April 25, 1985. That explains the “250485” portion of Pankov’s favored password. The registration information additional point out that in 2016 Pankov’s automobile was registered in a suburb of Moscow.
Russian incorporation information present that denispankov@yandex.com is tied to IP Pankov Denis Viktorovich, a now-defunct transportation firm within the Volograd Oblast, a area in southern Russia that shares an extended border with western Kazazkhstan.
More latest information for IP Pankov Denis Viktorovich present a microenterprise with this title in Omsk that described its fundamental exercise as “retail sale by mail or via the Internet.” Russian company information point out this entity was liquidated in 2021.
A reverse password search on “denis250485” through Constella exhibits this password was utilized by greater than 75 e mail addresses, most of that are some variation of gaihnik@mail.ru — reminiscent of gaihnik25@mail.ru, or gaihnik2504@rambler.ru.
In 2012, somebody posted solutions to a questionnaire on behalf of Denis Viktorovich Pankov to a Russian-language dialogue discussion board on Chinese crested canine breeds. The message stated Pankov was searching for a pet of a selected breed and was a resident of Krasnogorsk, a metropolis that’s adjoining to the northwestern boundary of Moscow.
The message stated Pankov was a then 27-year-old supervisor in an promoting firm, and could possibly be reached on the e mail tackle gaihnik@mail.ru.
GAIHNIK
Constella Intelligence exhibits gaihnik@mail.ru registered on the now-defunct e mail advertising service Smart Responder from an tackle in Gagarin, which is about 115 miles west of Moscow.
Back in 2015, the consumer Gaihnik25 was banned from the net recreation World of Tanks for violating the sport’s phrases that prohibit “bot farming,” or the automated use of huge numbers of participant accounts to win some benefit that’s often associated to cashing out recreation accounts or stock.
For the previous few years, somebody utilizing the nickname Gaihnik25 has been posting messages to the Russian-language hacking discussion board Gerki[.]pw, on dialogue threads concerning software program designed to “brute force” or mass-check on-line accounts for weak or compromised passwords.
A brand new member of the Russian hacking discussion board Nohide[.]Space utilizing the deal with Gaihnik has been commenting lately about proxy companies, credential checking software program, and the sale of hacked mailing lists. Gaihnik’s first publish on the discussion board involved personal software program for checking World of Tanks accounts.
The tackle gaihnik@mail.ru exhibits how so many e mail addresses tied to Pankov have been additionally linked to apparently deceptive identities on Vkontakte and elsewhere. Constella discovered this tackle was tied to a Vkontakte account for a Dmitriy Zakarov.
Microsoft’s Bing search engine says gaihnik@mail.ru belongs to 37-year-old Denis Pankov, but clicking the Mail.ru profile for that consumer brings up a profile for a a lot older man by the title Gavril Zakarov. However, while you log in to a Mail.ru account and think about that profile, it exhibits that many of the account’s profile photographs are of a a lot youthful man.
Many of those self same photographs present up in an on-line courting profile at courting.ru for the consumer Gaihnik, a.okay.a “Denchik,” who says he’s a 37-year-old Taurus from Gagarin who enjoys going for walks in nature, staying up late, and being on the Internet.
Mr. Pankov didn’t reply to a number of requests for remark despatched to the entire e mail addresses talked about on this story. However, a few of these addresses produced detailed error responses; Mail.ru reported that the customers panov-v@mail.ru, asus666@mail.ru, and asus2504@mail.ru have been terminated, and that gaihnik25@mail.ru is now disabled.
Messages despatched to many different e mail addresses linked through passwords to Pankov and utilizing some variation of asus####@mail.ru additionally returned comparable account termination messages.