[ad_1]

Threat actors use a brand new hacking device dubbed AuKill to disable Endpoint Detection & Response (EDR) Software on targets’ techniques earlier than deploying backdoors and ransomware in Bring Your Own Vulnerable Driver (BYOVD) assaults.
In such assaults, malicious actors drop professional drivers signed with a legitimate certificates and able to working with kernel privileges on the victims’ gadgets to disable safety options and take over the system.
This method is widespread amongst numerous menace actors, from state-backed hacking teams to financially-motivated ransomware gangs.
The AuKill malware, first noticed by Sophos X-Ops safety researchers, drops a weak Windows driver (procexp.sys) subsequent to the one utilized by Microsoft’s Process Explorer v16.32. This is a extremely popular and bonafide utility that helps accumulate data on lively Windows processes.
To escalate privileges, it first checks if it is already working with SYSTEM privileges, and if not, it impersonates the TrustedInstaller Windows Modules Installer service to escalate to SYSTEM.
To disable safety software program, AuKill begins a number of threads to constantly probe and disable safety processes and companies (and guarantee they continue to be disabled by stopping them from restarting).
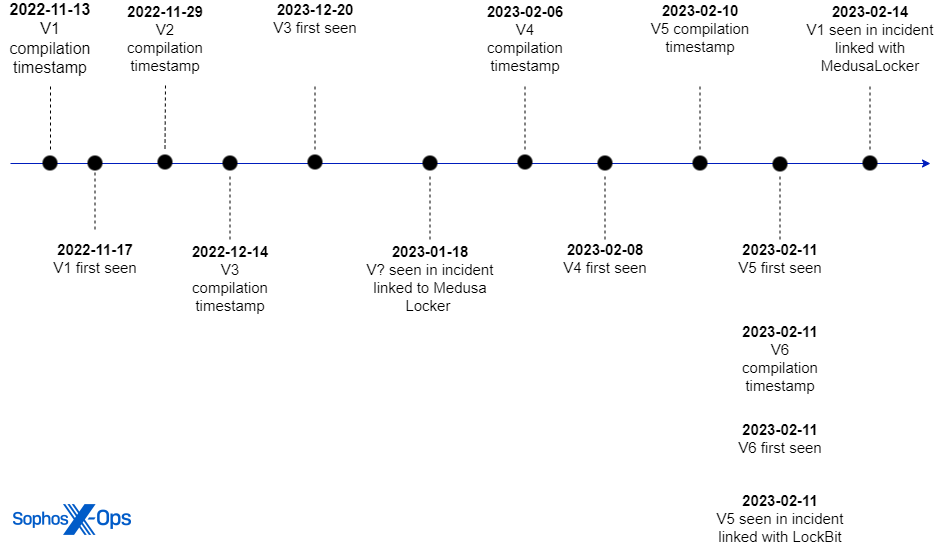
So far, a number of AuKill variations have been noticed within the wild, some deployed in a minimum of three separate incidents which have led to Medusa Locker and LockBit ransomware infections for the reason that begin of the 12 months.
“The device was used throughout a minimum of three ransomware incidents for the reason that starting of 2023 to sabotage the goal’s safety and deploy the ransomware,” Sophos X-Ops mentioned.
“In January and February, attackers deployed Medusa Locker ransomware after utilizing the device; in February, an attacker used AuKill simply previous to deploying Lockbit ransomware.”
AuKill is much like an open-source device referred to as Backstab, which additionally makes use of a Process Explorer driver to disable safety options working on compromised gadgets.
Backstab was beforehand deployed by the LockBit gang in a minimum of one assault noticed by Sophos X-Ops whereas analyzing the cybercrime group’s newest malware model, LockBit 3.0 or LockBit Black.
“We have discovered a number of similarities between the open-source device Backstab and AuKill,” the researchers mentioned.
“Some of those similarities embrace comparable, attribute debug strings, and almost equivalent code circulate logic to work together with the motive force.”
The oldest AuKill pattern has a November 2022 compilation timestamp, whereas the most recent was compiled in mid-February when it was additionally used as a part of an assault linked to the LockBit ransomware group.
