[ad_1]
Two U.S. males have been charged with hacking right into a U.S. Drug Enforcement Agency (DEA) on-line portal that faucets into 16 totally different federal regulation enforcement databases. Both are alleged to be half of a bigger legal group that makes a speciality of utilizing faux emergency knowledge requests from compromised police and authorities e-mail accounts to publicly threaten and extort their victims.

Prosecutors for the Eastern District of New York at the moment unsealed legal complaints towards Sagar Steven Singh — a.ok.a “Weep” — a 19-year-old from Pawtucket, Rhode Island; and Nicholas Ceraolo, 25, of Queens, NY, who allegedly glided by the handles “Convict” and “Ominus.”
The Justice Department says Singh and Ceraolo belong to a bunch of cybercriminals recognized to its members as “ViLE,” who concentrate on acquiring private details about third-party victims, which they then use to harass, threaten or extort the victims, a observe often known as “doxing.”
“ViLE is collaborative, and the members routinely share tactics and illicitly obtained information with each other,” prosecutors charged.
The authorities alleges the defendants and different members of ViLE use numerous strategies to acquire victims’ private data, together with:
-tricking customer support staff;
-submitting fraudulent authorized course of to social media firms to elicit customers’ registration data;
-co-opting and corrupting company insiders;
-searching private and non-private on-line databases;
-accessing a nonpublic United States authorities database with out authorization
-unlawfully utilizing official e-mail accounts belonging to different international locations.
The grievance says as soon as they obtained a sufferer’s data, Singh and Ceraolo would publish the knowledge in an internet discussion board. The authorities refers to this neighborhood solely as “Forum-1,” saying that it’s administered by the chief of ViLE (referenced within the grievance as “CC-1”).
“Victims are extorted into paying CC-1 to have their information removed from Forum-1,” prosecutors allege. “Singh also uses the threat of revealing personal information to extort victims into giving him access to their social media accounts, which Singh then resells.”
Sources inform KrebsOnSecurity along with being members of ViLE, each Weep and Ominous are or had been workers members for Doxbin, a extremely poisonous on-line neighborhood that gives a discussion board for digging up private data on folks and posting it publicly. This is supported by the Doxbin administrator’s claimed accountability for a high-profile intrusion on the DEA’s regulation enforcement knowledge sharing portal final yr.
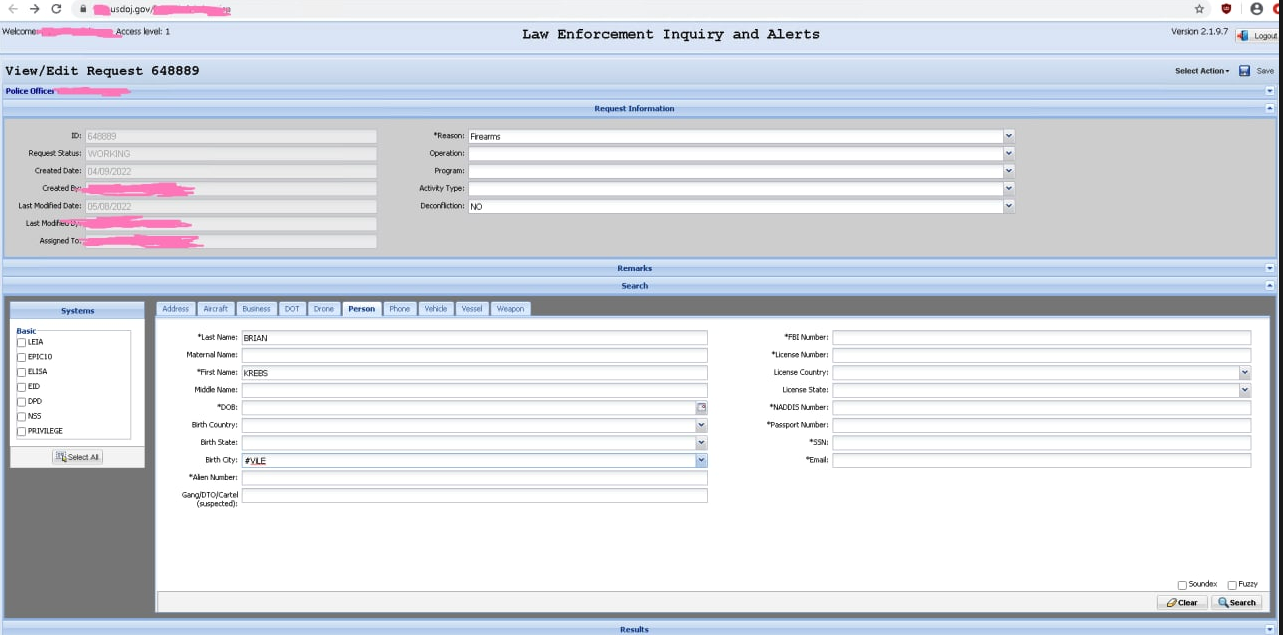
A screenshot of alleged entry to the Drug Enforcement Agency’s intelligence sharing portal, shared by “KT,” the present administrator of the doxing and harassment neighborhood Doxbin.
The authorities alleges that on May 7, 2022, Singh used stolen credentials to log right into a U.S. federal authorities portal with out authorization. The grievance doesn’t specify which company portal was hacked, however it does state that the portal included entry to regulation enforcement databases that observe narcotics seizures within the United States.
On May 12, 2022, KrebsOnSecurity broke the information that hackers had gained entry to a DEA portal that faucets into 16 totally different federal regulation enforcement databases. As reported on the time, the within scoop on how that hack went down got here from KT, the present administrator of the Doxbin and the person referenced within the authorities’s grievance as “CC-1.”
Indeed, a screenshot of the ViLE group web site contains the group’s official roster, which lists KT on the high, adopted by Weep and Ominus.

A screenshot of the web site for the cybercriminal group “ViLE.” Image: USDOJ.
In March 2022, KrebsOnSecurity warned that a number of cybercrime teams had been discovering success with fraudulent Emergency Data Requests (EDRs), whereby the hackers use compromised police and authorities e-mail accounts to file warrantless knowledge requests with social media corporations and cellular telephony suppliers, testifying that the knowledge being requested can’t watch for a warrant as a result of it pertains to an pressing matter of life and loss of life.
That story confirmed that the earlier proprietor of the Doxbin additionally was a part of a teenage hacking group that specialised in providing faux EDRs as a service on the darkish net.
Prosecutors say they tied Singh to the federal government portal hack as a result of he related to it from an Internet handle that he’d beforehand used to entry a social media account registered in his identify. When they raided Singh’s residence on Sept. 8, 2022 and seized his gadgets, investigators with Homeland Security discovered a cellular telephone and laptop computer that allegedly “contained extensive evidence of access to the Portal.”
The grievance alleges that between February 2022 and May 2022, Ceraolo used an official e-mail account belonging to a Bangladeshi police official to pose as a police officer in communication with U.S.-based social media platforms.
“In these communications, Ceraolo requested personal information about users of these platforms, under the false pretense that the users were committing crimes or in life-threatening danger,” the grievance states.
For instance, on or about March 13, 2022, Ceraolo allegedly used the Bangladeshi police e-mail account to falsely declare that the goal of the EDR had despatched bomb threats, distributed baby pornography and threatened officers of the Bangladeshi authorities.
On or about May 9, 2022, the federal government says, Singh despatched a good friend screenshots of textual content messages between himself and somebody he had doxed on the Doxbin and was attempting to extort for his or her Instagram deal with. The knowledge included the sufferer’s Social Security quantity, driver’s license quantity, cellphone quantity, and residential handle.
“Look familiar?” Singh allegedly wrote to the sufferer. “You’re gonna comply to me if you don’t want anything negative to happen to your parents. . . I have every detail involving your parents . . . allowing me to do whatever I desire to them in malicious ways.”
Neither of the defendants could possibly be instantly reached for remark. KT, the present administrator of Doxbin, declined a request for touch upon the costs.
Ceraolo is a self-described safety researcher who has been credited in many information tales over time with discovering safety vulnerabilities at AT&T, T-Mobile, Comcast and Cox Communications.
Ceraolo’s said associate in most of those discoveries — a 30-year-old Connecticut man named Ryan “Phobia” Stevenson — was charged in 2019 with being a part of a bunch that stole hundreds of thousands of {dollars} value of cryptocurrencies by way of SIM-swapping, a criminal offense that entails tricking a cellular supplier into routing a goal’s calls and textual content messages to a different gadget.
In 2018, KrebsOnSecurity detailed how Stevenson earned bug bounty rewards and public recognition from high telecom firms for locating and reporting safety holes of their web sites, all of the whereas secretly peddling those self same vulnerabilities to cybercriminals.
According to the Justice Department, if convicted Ceraolo faces as much as 20 years’ imprisonment for conspiracy to commit wire fraud; each Ceraolo and Singh face 5 years’ imprisonment for conspiracy to commit pc intrusions.
A replica of the grievance towards Ceraolo and Singh is right here (PDF).
