[ad_1]
A brand new Emotet phishing marketing campaign is concentrating on U.S. taxpayers by impersonating W-9 tax types allegedly despatched by the Internal Revenue Service and corporations you’re employed with.
Emotet is a infamous malware an infection distributed via phishing emails that previously contained Microsoft Word and Excel paperwork with malicious macros that set up the malware.
However, after Microsoft started blocking macros by default in downloaded Office paperwork, Emotet switched to utilizing Microsoft OneNote recordsdata with embedded scripts to put in the Emotet malware.
Once Emotet is put in, the malware will steal victims’ emails to make use of in future reply-chain assaults, ship additional spam emails, and in the end set up different malware that present preliminary entry to different risk actors, comparable to ransomware gangs.
Emotet gears up for the US tax season
The Emotet malware operations generally use themed phishing campaigns to coincide with holidays and yearly enterprise actions, comparable to the present U.S. tax season.
In new phishing campaigns seen by safety researchers at Malwarebytes and Palo Alto Networks Unit42, the Emotet malware targets customers with emails containing pretend W-9 tax kind attachments.
In the marketing campaign seen by Malwarebytes, the risk actors ship emails titled ‘IRS Tax Forms W-9,’ whereas impersonating an ‘Inspector’ from the Internal Revenue Service.
These phishing emails include a ZIP archive named ‘W-9 kind.zip’ that comprises a malicious Word doc. This Word doc has been inflated to over 500MB to make it more durable for safety software program to detect it as malicious.
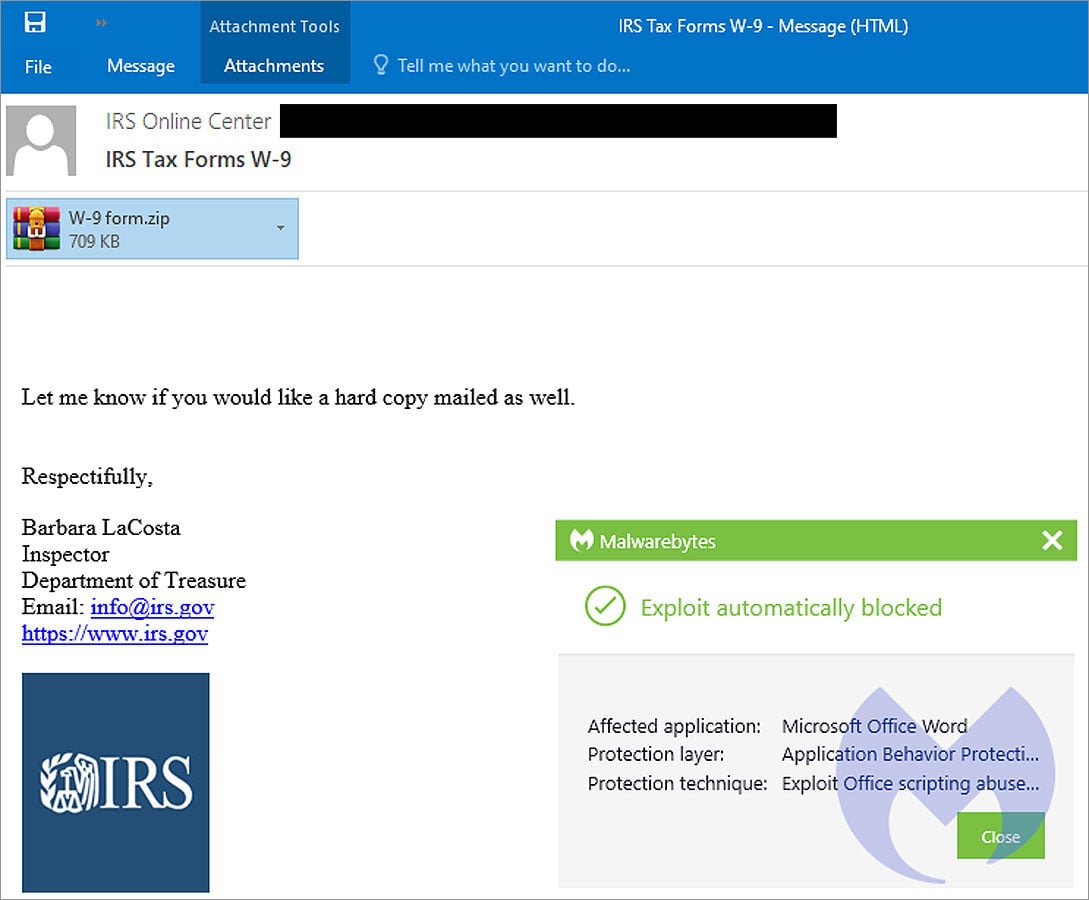
Source: Malwarebytes
However, now that Microsoft is obstructing macros by default, customers are much less more likely to undergo the difficulty of enabling the macros and turn into contaminated utilizing malicious Word paperwork.
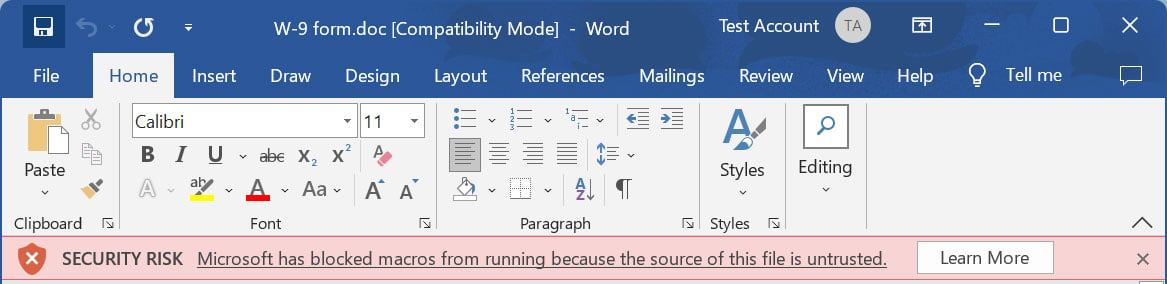
Source: BleepingComputer
In a phishing marketing campaign seen by Brad Duncan of Unit42, the risk actors bypass these restrictions through the use of Microsoft OneNote paperwork with embedded VBScript recordsdata that set up the Emotet malware.
This phishing marketing campaign makes use of reply-chain emails containing pretending to be from enterprise companions sending you W-9 Forms, as proven beneath.
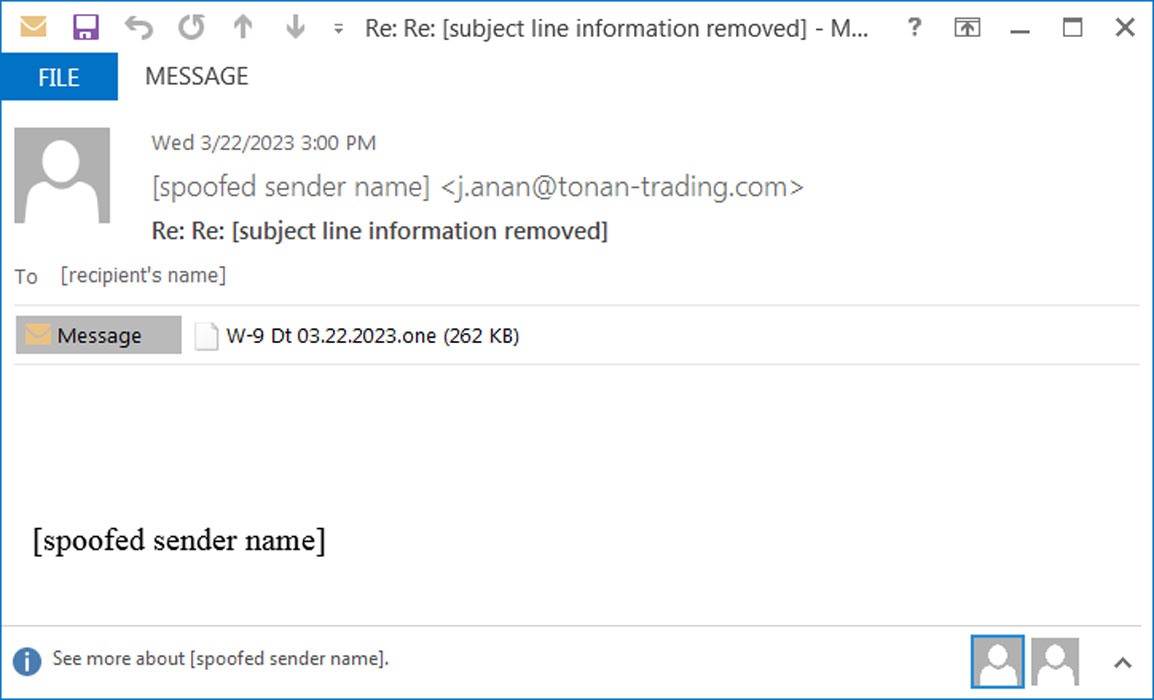
Source: Unit42
The connected OneNote paperwork will faux to be protected, requesting that you just double-click the ‘View’ button to see the doc accurately. However, hidden beneath that View button is a VBScript doc that will probably be launched as a substitute.
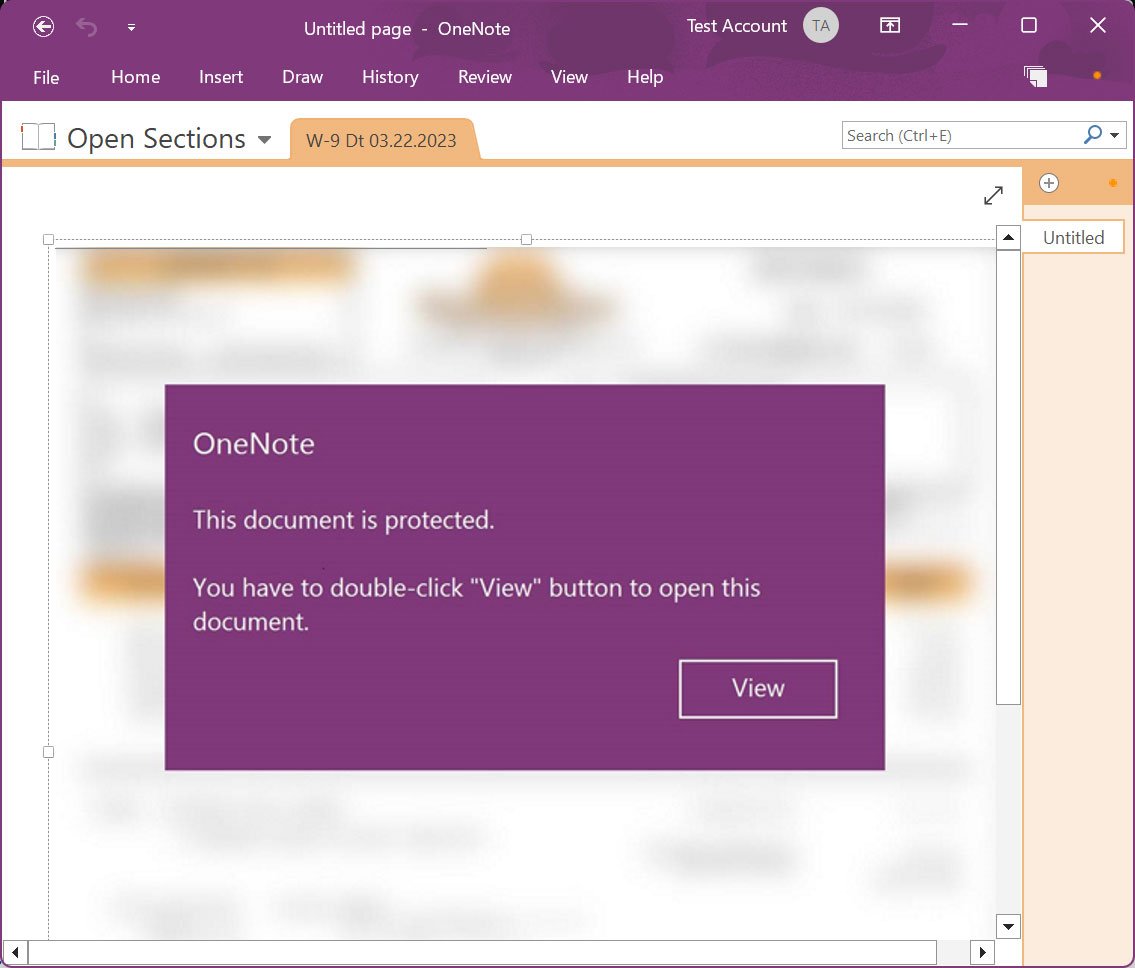
Source: BleepingComputer
When launching the embedded VBScript file, Microsoft OneNote will warn the consumer that the file could also be malicious. Unfortunately, historical past has proven us that many customers ignore these warnings and easily permit the recordsdata to run.
Once executed, the VBScript will obtain the Emotet DLL and run it utilizing regsvr32.exe.
The malware will now quietly run within the background, stealing electronic mail, contacts, and ready for additional payloads to put in on the machine.
If you obtain any emails claiming to be W-9 or different tax types, first scan the paperwork together with your native antivirus software program. However, as a result of delicate nature of those types, it isn’t recommended that you just add them to cloud-based scanning providers like VirusTotal.
Normally, tax types are distributed as PDF paperwork and never as Word attachments, so should you obtain one, you need to keep away from opening it and enabling macros.
Finally, it’s uncertain that tax types would ever be despatched as OneNote paperwork, so instantly delete the e-mail and don’t open it should you obtain one.
As at all times, the very best line of protection is to discard any electronic mail from folks you have no idea, and should you do know them, contact them by cellphone first to verify in the event that they despatched it.
