[ad_1]
New report says far too many companies have too many IT property they can’t see or aren’t utilizing, with some Windows servers missing endpoint safety and patch administration.

If you might be fortunate sufficient to have a Lambo in your storage, you’ll certainly have cameras a minimum of on the storage door, again door, cellar door and possibly the lavatory home windows.Translating that to enterprise cybersecurity, a sphere through which the losses may quantity to that of numerous unique vehicles: Organizations want visibility on all outward dealing with property, in addition to a complete overview of licensed however unused instruments that generate hidden prices.
Unfortunately, in response to asset intelligence platform Sevco Security, too many organizations have home windows (and Windows) and doorways that their IT and safety groups might not even find out about, or might don’t have any correct digital locks. In its second annual State of the Cybersecurity Attack Surface Report, which culled information from 500 organizations and practically a million IT property, Sevco stories that the overwhelming majority of the organizations it checked out should not have complete visibility of the property they should safe.
According to the report, roughly 20% of IT property are invisible to safety groups. These are ingress factors to company networks, however don’t seem in an enterprise supply, equivalent to endpoint safety, configuration/patch administration programs, listing providers or cellular gadget administration instruments.
“These assets consist largely of employees’ personal devices connecting from home, as well as devices and servers used in shadow IT projects conducted outside the scope and purview of IT and security teams,” stated the agency’s CEO J.J. Guy within the examine. “In either case, these devices are missing the security tools that will protect your IT environment if the device is exploited. The risk here is clear: you can’t protect the assets you can’t see.”
SEE: Visibility throughout property overlaps with cloud safety, a crucial apply, however daunting for the C-suite (TechRepublic)
Jump to:
Windows, some macOS units lack safety
Besides the IT property lacking endpoint safety, the agency stated practically 27% of IT property are uncovered by enterprise patch administration options. The agency stated:
- 23% of Windows servers are lacking endpoint safety.
- 21% of Windows servers go uncovered by patch administration.
- 6% of Windows servers usually are not in any enterprise software program stock.
- 14% of Windows purchasers accessing company property usually are not enterprise units.
- 5% of macOS units accessing company property usually are not enterprise units.
The report’s authors stated the Windows purchasers evading detection are on private units or programs, or a minimum of on units which can be accessing an organization’s software-as-a-service workplace automation property or different IT infrastructure, however occur to not be within the firm’s cellular gadget administration applied sciences (Figure A).
Figure A

“While connecting to SaaS automation tools may be permissible, doing so at scale and without visibility into what assets are accessing the network introduces significant risk,” stated the examine.
SEE: Learn how information theft can come from inside the home (TechRepublic)
The examine stated the truth that 6% of Windows servers usually are not in any enterprise software program stock is an issue. “The likelihood is that these are the result of Shadow IT: instances unsanctioned by IT or security teams that were spun up — likely without applying the company’s security protocols — to accomplish some sort of specific task,” stated the authors. “Instead of decommissioning these servers, teams may have simply abandoned them. As a result these servers remain connected to the network as a potential attack surface access point. In other instances, the servers may be actively being used as part of an ongoing Shadow IT initiative.”
Stale licenses are invisible prices
The report additionally checked out “stale licenses,” which represents units or programs whose licenses expired, don’t exist or had been taken offline incorrectly. The examine discovered:
- Approximately 17% of endpoint safety software program is licensed however not in use.
- Approximately 6% of patch and configuration administration software program is licensed however not in use (Figure B).
Figure B
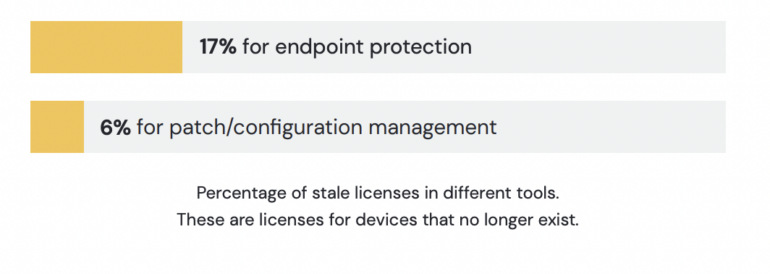
It additionally reported that orphaned property — those who seem within the safety management console with a supply agent put in, however haven’t checked in for a substantial time frame — pose a menace.
“Organizations with orphaned devices are rife with unknown security gaps, and organizations with stale licenses are overpaying for software,” stated the corporate.
Finding cracks within the window, and instruments you aren’t utilizing
The Sevco report suggests steps IT groups can take to safe their uncovered property, together with:
- Audit safety/IT instruments for protection gaps, by correlating and deduplicating units throughout sources.
- Find orphaned units that is perhaps susceptible.
- Implement cellular gadget administration to raised safe private units.
- ID and take away any stale licenses in units that haven’t been checked or utilized in a month.
- Either reallocate the licenses to different units, or downgrade the licenses to avoid wasting prices or use the funds for extra productive ends.
“IT environments are constantly changing as new devices and new tools are introduced,” from the examine. “Malicious actors have become very adept at leveraging those changes to take advantage of vulnerabilities.”
The agency instructed taking inventory of all units and programs providing ingress to networks. “In order to maintain the upper hand against sophisticated adversaries, it is critical for IT and security teams to maintain an accurate and up to date asset inventory that reflects the reality of their dynamic IT environment.”
Download: This Shadow IT coverage from TechRepublic Premium.
