[ad_1]
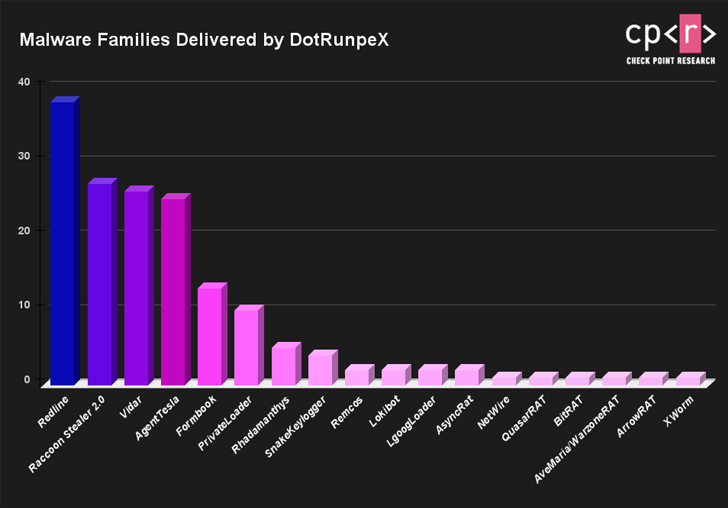
A brand new piece of malware dubbed dotRunpeX is getting used to distribute quite a few identified malware households corresponding to Agent Tesla, Ave Maria, BitRAT, FormBook, LokiBot, NetWire, Raccoon Stealer, RedLine Stealer, Remcos, Rhadamanthys, and Vidar.
“DotRunpeX is a brand new injector written in .NET utilizing the Process Hollowing method and used to contaminate methods with quite a lot of identified malware households,” Check Point mentioned in a report revealed final week.
Said to be in energetic growth, dotRunpeX arrives as a second-stage malware within the an infection chain, typically deployed by way of a downloader (aka loader) that is transmitted by way of phishing emails as malicious attachments.
Alternatively, it is identified to leverage malicious Google Ads on search outcome pages to direct unsuspecting customers trying to find widespread software program corresponding to AnyDesk and LastPass to copycat websites internet hosting trojanized installers.
The newest DotRunpeX artifacts, first noticed in October 2022, add an additional obfuscation layer by utilizing the KoiVM virtualizing protector.
It’s value stating that the findings dovetail with a malvertising marketing campaign documented by SentinelOne final month by which the loader and the injector parts had been collectively known as MalVirt.
Check Point’s evaluation has additional revealed that “every dotRunpeX pattern has an embedded payload of a sure malware household to be injected,” with the injector specifying an inventory of anti-malware processes to be terminated.
Discover the Hidden Dangers of Third-Party SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Join our webinar to study concerning the sorts of permissions being granted and easy methods to reduce danger.
This, in flip, is made attainable by abusing a weak course of explorer driver (procexp.sys) that is integrated into dotRunpeX in order to acquire kernel mode execution.
There are indicators that dotRunpeX may very well be affiliated to Russian-speaking actors based mostly on the language references within the code. The most regularly delivered malware households delivered by the rising risk embrace RedLine, Raccoon, Vidar, Agent Tesla, and FormBook.
[ad_2]