[ad_1]

The builders of the BlackLotus UEFI bootkit have improved the malware with Secure Boot bypass capabilities that permit it to contaminated even absolutely patched Windows 11 programs.
BlackLotus is the primary public instance of UEFI malware that may keep away from the Secure Boot mechanism, thus having the ability to disable safety protections that include the working system.
The malware might be used to impair the BitLocker information safety characteristic, the Microsoft Defender Antivirus, and the Hypervisor-protected Code Integrity (HVCI) – also referred to as the Memory Integrity characteristic that protects in opposition to makes an attempt to take advantage of the Windows Kernel.
The Unified Extensible Firmware Interface (UEFI) is the software program that connects the working system with the {hardware} that runs it.
It is low-level code that executes when the pc powers up and dictates the booting sequence earlier than the working system begins any of its routines.
BlackLotus commodity bootkit
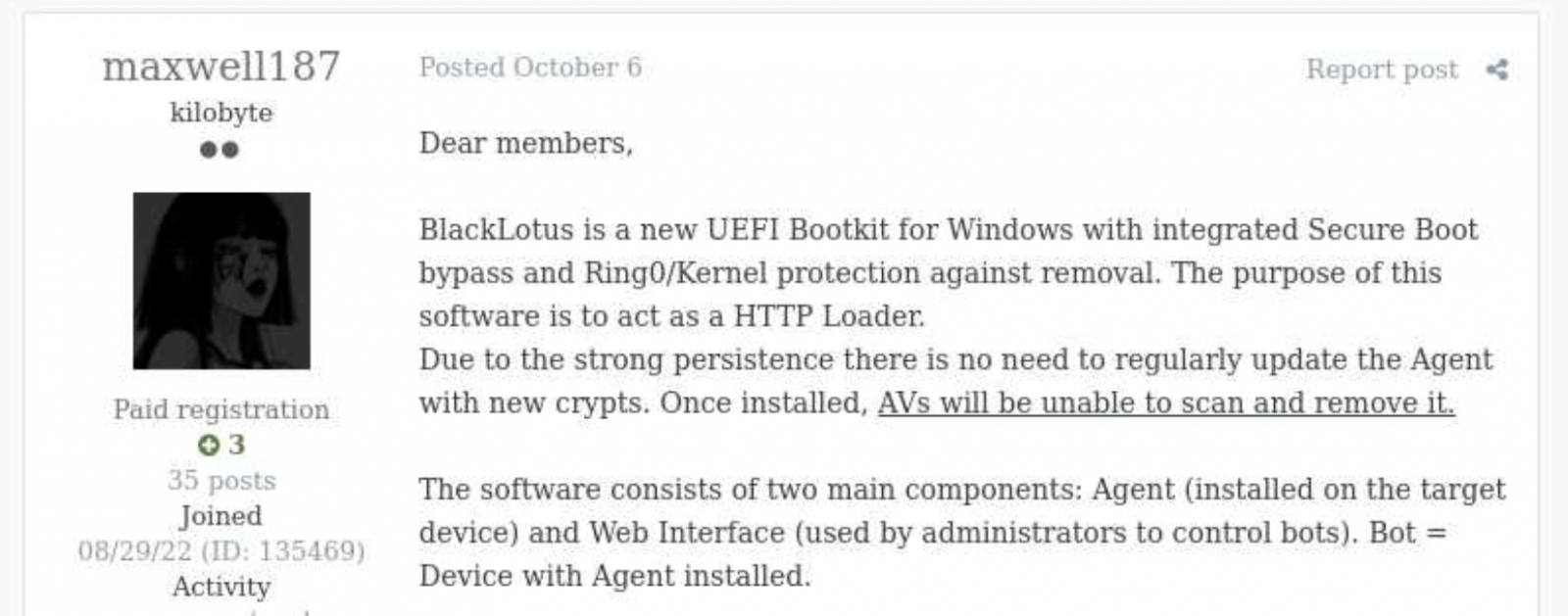
The BlackLotus UEFI malware emerged final yr promoted on hacking boards with a characteristic set that makes it just about invisible to antivirus brokers put in on the compromised host.
supply: KELA
The advertiser stated that the malware takes solely 80kb after set up and the price of a license was $5,000, though rebuilds have been accessible for simply $200.
In a report this week, safety researchers at ESET confirmed that the malware features precisely as marketed and it will probably bypass the Secure Boot mechanism by leveraging a vulnerability from final yr tracked as CVE-2022-21894.
More details about why the safety updates for CVE-2022-21894 do not block this malware is accessible beneath.
Their investigation began from an HTTP downloader that turned out to be the BlackLotus UEFI bootkit user-mode part, which communicates with the command and management (C2) server and might load different payloads (person/kernel-mode).
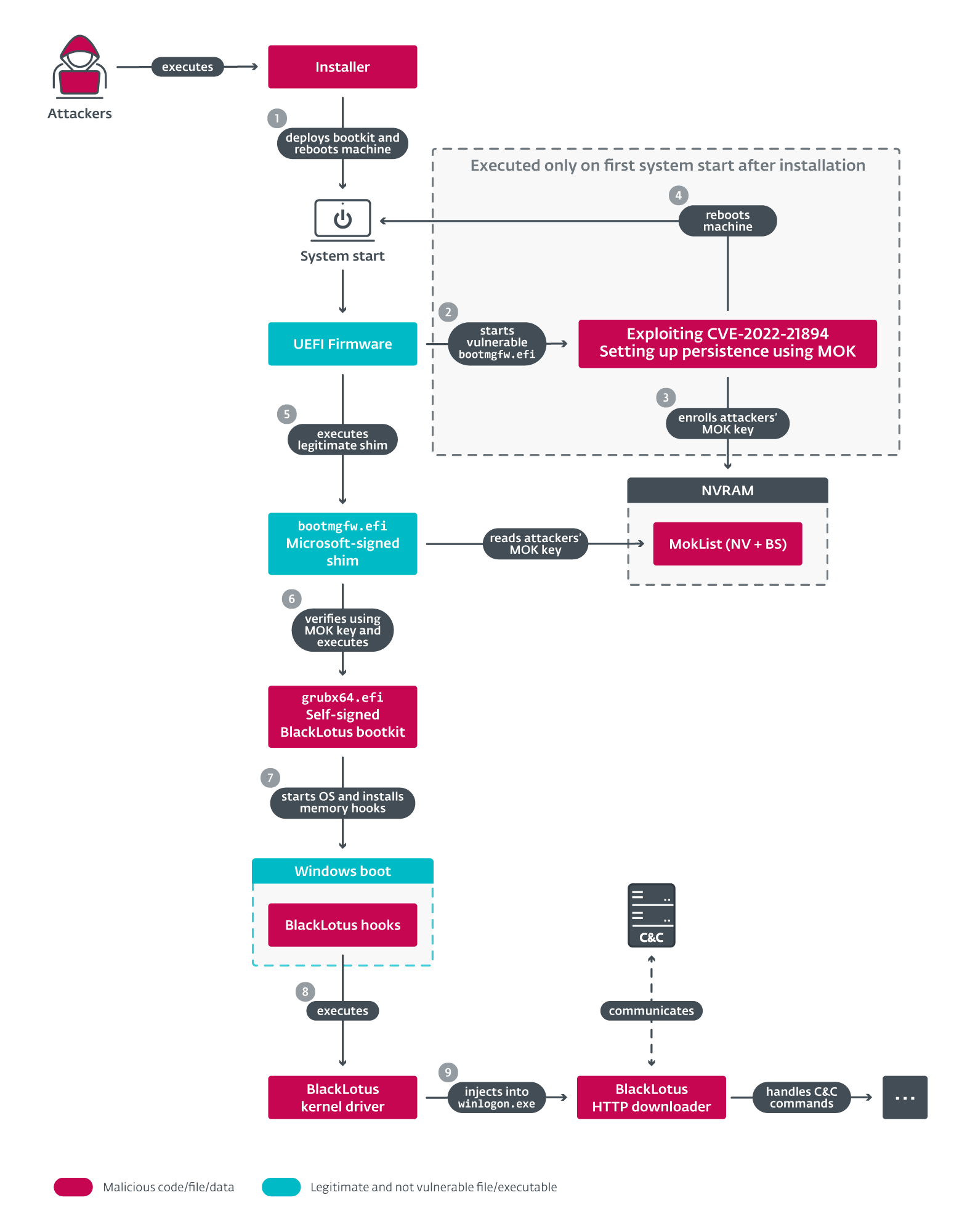
BlackLotus an infection chain
ESET malware researcher Martin Smolár notes that the assault begins with executing an installer that deploys the bootkit’s information to the EFI system partition, disables the HVCI and BitLocker protections, and reboots the host.
The attacker depends on reliable binaries weak to CVE-2022-21894 (Windows Hypervisor Loader, Windows Boot Manager, PE binaries) and their customized Boot Configuration Data (BCD).
Persistence on machines with UEFI Secure Boot enabled is achieved after the preliminary reboot by exploiting CVE-2022-21894 and enrolling the attacker’s Machine Owner Key (MOK).
The self-signed UEFI bootkit is launched after one other reboot and the malicious kernel driver and the HTTP downloader are deployed to finish the malware set up.
supply: ESET
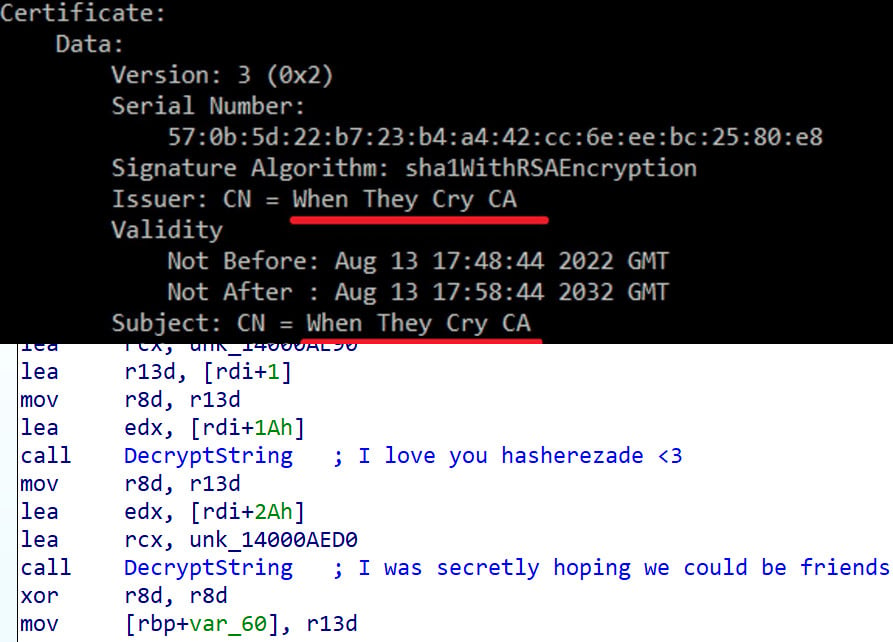
Among the artifacts found within the BlackLotus code there are references to the Higurashi When They Cry anime collection, together with the names of two elements and the issuer of the self-signed certificates for the bootkit binary.
Another reference the creator of BlackLotus left within the malware code is in unused strings that decrypt into messages to Polish malware analyst Aleksandra Doniec.
supply: ESET
Bug patched, safety threat persists
ESET says that the BlackLotus installer may be both on-line or offline, the distinction between them is that the offline variants carry the weak Windows binaries.
The on-line model of the installer downloads the Windows binaries “directly from the Microsoft symbol store.”
The researchers noticed the three information beneath being abused by the bootkit:
- https://msdl.microsoft.com/download/symbols/bootmgfw.efi/7144BCD31C0000/bootmgfw.efi
- https://msdl.microsoft.com/download/symbols/bootmgr.efi/98B063A61BC000/bootmgr.efi
- https://msdl.microsoft.com/download/symbols/hvloader.efi/559F396411D000/hvloader.Efi
Smolár explains that exploiting CVE-2022-21894 is what permits BlackLotus to bypass Secure Boot and set up persistence after disabling HVCI (to load unsigned kernel code) and BitLocker (to permit modifying the boot chain with out triggering the restoration process on programs with the Trusted Platform Module (TPM) {hardware} part):
- Exploiting CVE-2022-21894 to permit bypassing Secure Boot and putting in the bootkit. Arbitrary code can then be executed in early boot phases, the place the platform remains to be owned by firmware and UEFI Boot Services features are nonetheless accessible. This permits attackers to do many issues that they shouldn’t be capable of do on a machine with UEFI Secure Boot enabled with out having bodily entry to it, similar to modifying Boot-services-only NVRAM variables. And that is what attackers benefit from to arrange persistence for the bootkit within the subsequent step.
- Setting persistence by writing its personal MOK to the MokList, Boot-services-only NVRAM variable. By doing this, it will probably use a reliable Microsoft-signed shim for loading its self-signed (signed by the personal key belonging to the important thing written to MokList) UEFI bootkit as an alternative of exploiting the vulnerability on each boot.
To observe, proof of idea (PoC) exploit code for CVE-2022-21894 has been publicly accessible for greater than half a yr, since August 2022. However, the safety difficulty has been largely ignored.
Microsoft addressing the vulnerability in June 2022 was not sufficient to shut the safety hole as a result of the UEFI DBX (UEFI revocation record) has but to be up to date with the untrusted keys and binary hashes utilized in booting programs which have Secure Boot enabled.
“As a result, attackers can bring their own copies of vulnerable binaries to their victims’ machines to exploit this vulnerability and bypass Secure Boot on up-to-date UEFI systems” – ESET
Last yr, researchers disclosed a number of UEFI vulnerabilities [1, 2] that may be leveraged to disable Secure Boot. However, a few of them can nonetheless be exploited because of distributors not supporting affected gadgets, incorrect patching, or not patching in any respect.
Smolár says that these failures have been certain to draw the eye of a risk actor and result in the creation of a highly-capable UEFI bootkit.
UEFI malware
UEFI bootkits are on the reverse finish of run-of-the-mill malware. They are uncommon findings seen in assaults attributed to superior risk actors engaged on behalf of a nation-state.
Although proof-of-concept bootkits have existed since 2013 (e.g. DreamBoot) and malicious EFI bootloaders that prevented the machine from booting have been present in 2020, the record of full-blown bootkits utilized in real-world assaults is extremely quick:
- FinSpy – a part of the homonymous surveillance toolset (a.ok.a. FinFisher, WingBird)
- ESPecter – a patched Windows Boot Manager on the EFI (Extensible Firmware Interface) system partition
- CosmicStrand/Spy Shadow Trojan – a UEFI risk that hid within the firmware pictures of ASUS and Gigabyte motherboards to deploy a kernel-level implant each time the compromised Windows machine booted
The information for the bigger class of UEFI malware, which additionally consists of rootkits or firmware implants, isn’t a lot bigger.
In 2018 ESET uncovered the LoJax UEFI rootkit utilized by the Russian hackers within the APT28 group (Sednit/Fancy Bear/Sofacy).
Two years later, Kaskpersky printed a report in regards to the MosaicRegressor rootkit that served Chinese-speaking hackers in information theft and espionage operations in 2019.
In early 2022, one other UEFI firmware implant was disclosed. MoonBounce was attributed to the Chinese-speaking group APT41/Winnti.
However, BlackLotus is the primary ever publicly disclosed UEFI bootkit that bypasses Secure Boot and is related to the cybercriminal world.
