[ad_1]
In the first article of this collection, we mentioned communal computing gadgets and the issues they create–or, extra exactly, the issues that come up as a result of we don’t actually perceive what “communal” means. Communal gadgets are meant for use by teams of individuals in houses and places of work. Examples embody widespread residence assistants and good shows just like the Amazon Echo, Google Home, Apple HomePod, and plenty of others. If we don’t create these gadgets with communities of individuals in thoughts, we are going to proceed to construct the incorrect ones.
Ever because the idea of a “user” was invented (which was most likely later than you assume), we’ve assumed that gadgets are “owned” by a single consumer. Someone buys the machine and units up the account; it’s their machine, their account. When we’re constructing shared gadgets with a consumer mannequin, that mannequin rapidly runs into limitations. What occurs whenever you need your property assistant to play music for a cocktail party, however your preferences have been skewed by your kids’s listening habits? We, as customers, have sure expectations for what a tool ought to do. But we, as technologists, have sometimes ignored our personal expectations when designing and constructing these gadgets.
This expectation isn’t a brand new one both. The phone within the kitchen was for everybody’s use. After the discharge of the iPad in 2010 Craig Hockenberry mentioned the nice worth of communal computing but in addition the issues:
“When you pass it around, you’re giving everyone who touches it the opportunity to mess with your private life, whether intentionally or not. That makes me uneasy.”
Communal computing requires a brand new mindset that takes under consideration customers’ expectations. If the gadgets aren’t designed with these expectations in thoughts, they’re destined for the landfill. Users will finally expertise “weirdness” and “annoyance” that grows to mistrust of the machine itself. As technologists, we frequently name these weirdnesses “edge cases.” That’s exactly the place we’re incorrect: they’re not edge circumstances, however they’re on the core of how individuals need to use these gadgets.
In the primary article, we listed 5 core questions we must always ask about communal gadgets:
- Identity: Do we all know the entire people who find themselves utilizing the machine?
- Privacy: Are we exposing (or hiding) the best content material for the entire individuals with entry?
- Security: Are we permitting the entire individuals utilizing the machine to do or see what they need to and are we defending the content material from people who shouldn’t?
- Experience: What is the contextually acceptable show or subsequent motion?
- Ownership: Who owns the entire knowledge and companies connected to the machine that a number of persons are utilizing?
In this text, we’ll take a deeper take a look at these questions, to see how the issues manifest and tips on how to perceive them.
Identity
All of the issues we’ve listed begin with the concept there’s one registered and identified one who ought to use the machine. That mannequin doesn’t match actuality: the id of a communal machine isn’t a single individual, however everybody who can work together with it. This could possibly be anybody capable of faucet the display, make a voice command, use a distant, or just be sensed by it. To perceive this communal mannequin and the issues it poses, begin with the one who buys and units up the machine. It is related to that particular person’s account, like a private Amazon account with its order historical past and purchasing record. Then it will get tough. Who doesn’t, can’t, or shouldn’t have full entry to an Amazon account? Do you need everybody who comes into your home to have the ability to add one thing to your purchasing record?
If you consider the spectrum of people that could possibly be in your home, they vary from individuals whom you belief, to individuals who you don’t actually belief however who must be there, to those that you shouldn’t belief in any respect.
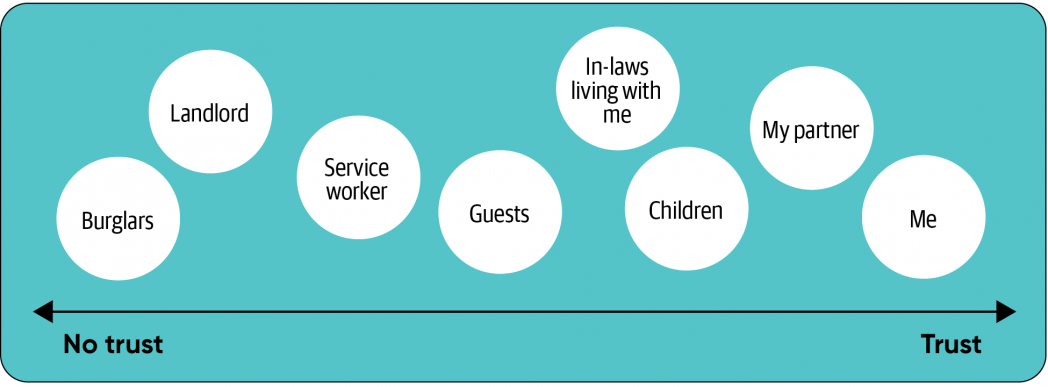
In addition to people, we have to think about the teams that every individual could possibly be a part of. These group memberships are known as “pseudo-identities”; they’re aspects of an individual’s full id. They are normally outlined by how the individual related themself with a bunch of different individuals. My life at work, residence, a highschool associates group, and as a sports activities fan present totally different components of my id. When I’m with different individuals who share the identical pseudo-identity, we are able to share data. When there are individuals from one group in entrance of a tool I’ll keep away from exhibiting content material that’s related to one other group (or one other private pseudo-identity). This can sound summary, but it surely isn’t; should you’re with associates in a sports activities bar, you most likely need notifications in regards to the groups you comply with. You most likely don’t need information about work, except it’s an emergency.
There are necessary explanation why we present a selected side of our id in a selected context. When designing an expertise, you must think about the id context and the place the expertise will happen. Most lately this has provide you with do business from home. Many individuals discuss ‘bringing your whole self to work,’ however don’t understand that “your whole self” isn’t all the time acceptable. Remote work modifications when and the place I ought to work together with work. For a wise display in my kitchen, it’s acceptable to have content material that’s associated to my residence and household. Is it acceptable to have all of my work notifications and conferences there? Could or not it’s an issue for kids to have the flexibility to affix my work calls? What does my IT group require so far as safety of labor gadgets versus private residence gadgets?
With these gadgets we might have to modify to a special pseudo-identity to get one thing executed. I’ll must be reminded of a piece assembly. When I get a notification from an in depth good friend, I have to determine whether or not it’s acceptable to reply based mostly on the opposite individuals round me.
The pandemic has damaged down the boundaries between residence and work. The pure context change from being at work and worrying about work issues after which going residence to fret about residence issues is not the case. People have to make a aware effort to “turn off work” and to alter the context. Just as a result of it’s the center of the workday doesn’t all the time imply I need to be bothered by work. I’ll need to change contexts to take a break. Such context shifts add nuance to the best way the present pseudo-identity must be thought of, and to the overarching context you must detect.
Next, we have to think about identities as teams that I belong to. I’m a part of my household, and my household would probably need to speak with different households. I stay in a home that’s on my road alongside different neighbors. I’m a part of a company that I establish as my work. These are all pseudo-identities we must always think about, based mostly on the place the machine is positioned and in relation to different equally necessary identities.
The crux of the issue with communal gadgets is the a number of identities which might be or could also be utilizing the machine. This requires better understanding of who, the place, and why persons are utilizing the machine. We want to think about the forms of teams which might be a part of the house and workplace.
Privacy
As we think about the identities of all individuals with entry to the machine, and the id of the place the machine is to be a part of, we begin to think about what privateness expectations individuals might have given the context wherein the machine is used.
Privacy is difficult to grasp. The framework I’ve discovered most useful is Contextual Integrity which was launched by Helen Nissenbaum within the ebook Privacy in Context. Contextual Integrity describes 4 key features of privateness:
- Privacy is supplied by acceptable flows of data.
- Appropriate data flows are people who conform to contextual data norms.
- Contextual informational norms refer to 5 unbiased parameters: knowledge topic, sender, recipient, data kind, and transmission precept.
- Conceptions of privateness are based mostly on moral issues that evolve over time.
What is most necessary about Contextual Integrity is that privateness just isn’t about hiding data away from the general public however giving individuals a approach to management the circulation of their very own data. The context wherein data is shared determines what is suitable.
This circulation both feels acceptable, or not, based mostly on key traits of the data (from Wikipedia):
- The knowledge topic: Who or what is that this about?
- The sender of the info: Who is sending it?
- The recipient of the info: Who will finally see or get the info?
- The data kind: What kind of data is that this (e.g. a photograph, textual content)?
- The transmission precept: In what set of norms is that this being shared (e.g. faculty, medical, private communication)?
We not often acknowledge how a delicate change in one in all these parameters could possibly be a violation of privateness. It could also be fully acceptable for my good friend to have a bizarre photograph of me, however as soon as it will get posted on an organization intranet web site it violates how I need data (a photograph) to circulation. The recipient of the info has modified to one thing I not discover acceptable. But I won’t care whether or not an entire stranger (like a burglar) sees the photograph, so long as it by no means will get again to somebody I do know.
For communal use circumstances, the sender or receiver of data is usually a bunch. There could also be a number of individuals within the room throughout a video name, not simply the individual you’re calling. People can stroll out and in. I may be proud of some individuals in my residence seeing a selected photograph, however discover it embarrassing whether it is proven to visitors at a cocktail party.
We should additionally think about what occurs when different individuals’s content material is proven to those that shouldn’t see it. This content material could possibly be photographs or notifications from individuals outdoors the communal house that could possibly be seen by anybody in entrance of the machine. Smartphones can disguise message contents whenever you aren’t close to your telephone for this actual purpose.
The companies themselves can develop the ‘receivers’ of data in ways in which create uncomfortable conditions. In Privacy in Context, Nissenbaum talks about the privateness implications of Google Street View when it locations photographs of individuals’s homes on Google Maps. When a home was solely seen to individuals who walked down the road that was one factor, however when anybody on the earth can entry an image of a home, that modifications the parameters in a method that causes concern. Most lately, IBM used Flickr photographs that have been shared underneath a Creative Commons license to coach facial recognition algorithms. While this didn’t require any change to phrases of the service it was a shock to individuals and could also be in violation of the Creative Commons license. In the tip, IBM took the dataset down.
Privacy issues for communal gadgets ought to deal with who’s having access to data and whether or not it’s acceptable based mostly on individuals’s expectations. Without utilizing a framework like contextual inquiry we will probably be caught speaking about generalized guidelines for knowledge sharing, and there’ll all the time be edge circumstances that violate somebody’s privateness.
A be aware about kids
Children make id and privateness particularly difficult. About 40% of all households have a toddler. Children shouldn’t be an afterthought. If you aren’t compliant with native legal guidelines you will get in numerous hassle. In 2019, YouTube needed to settle with the FTC for a $170 million fantastic for promoting advertisements focusing on kids. It will get difficult as a result of the ‘age of consent’ depends upon the area as effectively: COPPA within the US is for individuals underneath 13 years outdated, CCPA in California is for individuals underneath 16, and GDPR general is underneath 16 years outdated however every member state can set its personal. The second you acknowledge kids are utilizing your platforms, you must accommodate them.
For communal gadgets, there are numerous use circumstances for kids. Once they understand they’ll play no matter music they need (together with tracks of fart sounds) on a shared machine they are going to do it. Children deal with the exploration over the duty and can find yourself discovering far more in regards to the machine than mother and father may. Adjusting your practices after constructing a tool is a recipe for failure. You will discover that the paradigms you select for different events gained’t align with the expectations for kids, and modifying your software program to accommodate kids is tough or inconceivable. It’s necessary to account for kids from the start.
Security
To get to a house assistant, you normally have to move by means of a house’s outer door. There is normally a bodily limitation by the use of a lock. There could also be alarm programs. Finally, there are social norms: you don’t simply stroll into another person’s home with out knocking or being invited.
Once you’re previous all of those locks, alarms, and norms, anybody can entry the communal machine. Few issues inside a house are restricted–presumably a secure with necessary paperwork. When a communal machine requires authentication, it’s normally subverted indirectly for comfort: for instance, a password may be taped to it, or a password might by no means have been set.
The idea of Zero Trust Networks speaks to this downside. It comes right down to a key query: is the chance related to an motion better than the belief we’ve got that the individual performing the motion is who they are saying they’re?
Passwords, passcodes, or cellular machine authentication turn into nuisances; these supposed secrets and techniques are continuously shared between everybody who has entry to the machine. Passwords may be written down for individuals who can’t bear in mind them, making them seen to much less trusted individuals visiting your family. Have we not discovered something because the film War Games?
When we think about the chance related to an motion, we have to perceive its privateness implications. Would the motion expose somebody’s data with out their data? Would it enable an individual to faux to be another person? Could one other get together inform simply the machine was being utilized by an imposter?
There is a tradeoff between the belief and danger. The machine must calculate whether or not we all know who the individual is and whether or not the individual needs the data to be proven. That must be weighed towards the potential danger or hurt if an inappropriate individual is in entrance of the machine.
Just a few examples of this tradeoff:
| Feature | Risk and belief calculation | Possible points |
| Showing a photograph when the machine detects somebody within the room | Photo content material sensitivity, who’s within the room | Showing an inappropriate photograph to a whole stranger |
| Starting a video name | Person’s account getting used for the decision, the precise individual beginning the decision | When the opposite facet picks up it might not be who they thought it might be |
| Playing a private tune playlist | Personal suggestions being impacted | Incorrect future suggestions |
| Automatically ordering one thing based mostly on a voice command | Convenience of ordering, approval of the purchasing account’s proprietor | Shipping an merchandise that shouldn’t have been ordered |
This will get even trickier when individuals not within the residence can entry the gadgets remotely. There have been circumstances of harassment, intimidation, and home abuse by individuals whose entry ought to have been revoked: for instance, an ex-partner turning off the heating system. When ought to somebody be capable of entry communal gadgets remotely? When ought to their entry be controllable from the gadgets themselves? How ought to individuals be reminded to replace their entry management lists? How does fundamental safety upkeep occur inside a communal house?
See how a lot work this takes in a current account of professional bono safety work for a harassed mom and her son. Or how a YouTuber was blackmailed, surveilled, and harassed by her good residence. Apple even has a handbook for any such scenario.
At residence, the place there’s no company IT group to create insurance policies and automation to maintain issues safe, it’s subsequent to inconceivable to handle all of those safety points. Even some firms have hassle with it. We want to determine how customers will preserve and configure a communal machine over time. Configuration for gadgets within the residence and workplace might be wrought with numerous several types of wants over time.
For instance, what occurs when somebody leaves the house and is not a part of it? We might want to take away their entry and will even discover it needed to dam them from sure companies. This is highlighted with the circumstances of harassment of individuals by means of spouses that also management the communal gadgets. Ongoing upkeep of a selected machine may be triggered by a change in wants by the group. A house machine could also be used to simply play music or examine the climate at first. But when a brand new child comes residence, having the ability to do video calling with shut kinfolk might turn into the next precedence.
End customers are normally very dangerous at altering configuration after it’s set. They might not even know that they’ll configure one thing within the first place. This is why individuals have made a enterprise out of organising residence stereo and video programs. People simply don’t perceive the applied sciences they’re placing of their homes. Does that imply we’d like some kind of handy-person that does residence machine setup and administration? When extra difficult routines are required to satisfy the wants, how does somebody enable for modifications with out writing code, if they’re allowed to?
Communal gadgets want new paradigms of safety that transcend the usual login. The world inside a house is protected by a barrier like a locked door; the capabilities of communal gadgets ought to respect that. This means each eradicating friction in some circumstances and rising it in others.
A be aware about biometrics
(Source: Google Face Match video, https://youtu.be/ODy_xJHW6CI?t=26)
Biometric authentication for voice and face recognition might help us get a greater understanding of who’s utilizing a tool. Examples of biometric authentication embody FaceID for the iPhone and voice profiles for Amazon Alexa. There is a push for regulation of facial recognition applied sciences, however opt-in for authentication functions tends to be carved out.
However, biometrics aren’t with out issues. In addition to points with pores and skin tone, gender bias, and native accents, biometrics assumes that everybody is prepared to have a biometric profile on the machine–and that they might be legally allowed to (for instance, kids might not be allowed to consent to a biometric profile). It additionally assumes this know-how is safe. Google FaceMatch makes it very clear it is just a know-how for personalization, quite than authentication. I can solely guess they’ve legalese to keep away from legal responsibility when an unauthorized individual spoofs somebody’s face, say by taking a photograph off the wall and exhibiting it to the machine.
What can we imply by “personalization?” When you stroll right into a room and FaceMatch identifies your face, the Google Home Hub dings, exhibits your face icon, then exhibits your calendar (whether it is linked), and a feed of customized playing cards. Apple’s FaceID makes use of many ranges of presentation assault detection (often known as “anti-spoofing”): it verifies your eyes are open and you’re looking on the display, and it makes use of a depth sensor to ensure it isn’t “seeing” a photograph. The telephone can then present hidden notification content material or open the telephone to the house display. This measurement of belief and danger is benefited by understanding who could possibly be in entrance of the machine. We can’t overlook that the machine studying that’s doing biometrics just isn’t a deterministic calculation; there’s all the time some extent of uncertainty.
Social and data norms outline what we think about acceptable, who we belief, and the way a lot. As belief goes up, we are able to take extra dangers in the best way we deal with data. However, it’s tough to attach belief with danger with out understanding individuals’s expectations. I’ve entry to my partner’s iPhone and know the passcode. It could be a violation of a norm if I walked over and unlocked it with out being requested, and doing so will result in decreased belief between us.
As we are able to see, biometrics does provide some advantages however gained’t be the panacea for the distinctive makes use of of communal gadgets. Biometrics will enable these prepared to opt-in to the gathering of their biometric profile to realize customized entry with low friction, however it would by no means be useable for everybody with bodily entry.
Experiences
People use a communal machine for brief experiences (checking the climate), ambient experiences (listening to music or glancing at a photograph), and joint experiences (a number of individuals watching a film). The machine wants to concentrate on norms throughout the house and between the a number of individuals within the house. Social norms are guidelines by which individuals determine tips on how to act in a selected context or house. In the house, there are norms about what individuals ought to and shouldn’t do. If you’re a visitor, you attempt to see if individuals take their footwear off on the door; you don’t rearrange issues on a bookshelf; and so forth.
Most software program is constructed to work for as many individuals as doable; that is known as generalization. Norms stand in the best way of generalization. Today’s know-how isn’t adequate to adapt to each doable scenario. One technique is to simplify the software program’s performance and let the people implement norms. For instance, when a number of individuals speak to an Echo on the identical time, Alexa will both not perceive or it would take motion on the final command. Multi-turn conversations between a number of individuals are nonetheless of their infancy. This is okay when there are understood norms–for instance, between my associate and I. But it doesn’t work so effectively whenever you and a toddler are each making an attempt to shout instructions.
Norms are attention-grabbing as a result of they are typically discovered and negotiated over time, however are invisible. Experiences which might be constructed for communal use want to concentrate on these invisible norms by means of cues that may be detected from peoples’ actions and phrases. This will get particularly difficult as a result of a dialog between two individuals may embody data topic to totally different expectations (in a Contextual Integrity sense) about how that data is used. With sufficient knowledge, fashions might be created to “read between the lines” in each useful and harmful methods.
Video video games already cater to a number of individuals’s experiences. With the Nintendo Switch or another gaming system, a number of individuals can play collectively in a joint expertise. However, the principles governing these experiences are by no means utilized to, say, Netflix. The assumption is all the time that one individual holds the distant. How may these experiences be improved if software program may settle for enter from a number of sources (distant controls, voice, and so on.) to construct a choice of motion pictures that’s acceptable for everybody watching?
Communal expertise issues spotlight inequalities in households. With girls doing extra family coordination than ever, there’s a have to rebalance the duties for households. Most of the time these coordination duties are relegated to non-public gadgets, usually the spouse’s cell phone, after they contain the complete household (although there’s a digital divide outdoors the US). Without shifting these experiences into a spot that everybody can take part in, we are going to proceed these inequalities.
So far, know-how has been nice at intermediating individuals for coordination by means of programs like textual content messaging, social networks, and collaborative paperwork. We don’t construct interplay paradigms that enable for a number of individuals to interact on the identical time of their communal areas. To do that we have to deal with that the norms that dictate what is suitable conduct are invisible and pervasive within the areas these applied sciences are deployed.
Ownership
Many of those gadgets aren’t actually owned by the individuals who purchase them. As half of the present pattern in the direction of subscription-based enterprise fashions, the machine gained’t operate should you don’t subscribe to a service. Those companies have license agreements that specify what you may and can’t do (which you’ll be able to learn you probably have a few hours to spare and can perceive them).
For instance, this has been a problem for followers of Amazon’s Blink digicam. The residence automation trade is fragmented: there are numerous distributors, every with its personal utility to regulate their specific gadgets. But most individuals don’t need to use totally different apps to regulate their lighting, their tv, their safety cameras, and their locks. Therefore, individuals have began to construct controllers that span the totally different ecosystems. Doing so has brought on Blink customers to get their accounts suspended.
What’s even worse is that these license agreements can change each time the corporate needs. Licenses are continuously modified with nothing greater than a notification, after which one thing that was beforehand acceptable is now forbidden. In 2020, Wink abruptly utilized a month-to-month service cost; should you didn’t pay, the machine would cease working. Also in 2020, Sonos brought on a stir by saying they have been going to “recycle” (disable) outdated gadgets. They finally modified their coverage.
The problem isn’t simply what you are able to do together with your gadgets; it’s additionally what occurs to the info they create. Amazon’s Ring partnership with one in ten US police departments troubles many privateness teams as a result of it creates an enormous surveillance program. What should you don’t need to be part of the police state? Make certain you examine the best field and skim your phrases of service. If you’re designing a tool, you must require customers to decide in to knowledge sharing (particularly as areas adapt GDPR and CCPA-like regulation).
While strategies like federated studying are on the horizon, to keep away from latency points and mass knowledge assortment, it stays to be seen whether or not these strategies are passable for corporations that gather knowledge. Is there a profit to each organizations and their clients to restrict or obfuscate the transmission of information away from the machine?
Ownership is especially difficult for communal gadgets. This is a collision between the expectations of shoppers who put one thing of their residence; these expectations run immediately towards the best way rent-to-use companies are pitched. Until we acknowledge that {hardware} put in a house is totally different from a cloud service, we are going to by no means get it proper.
Lots of issues, now what?
Now that we’ve got dived into the assorted issues that rear their head with communal gadgets, what can we do about it? In the subsequent article we focus on a approach to think about the map of the communal house. This helps construct a greater understanding of how the communal machine suits within the context of the house and companies that exist already.
We may also present an inventory of dos and don’ts for leaders, builders, and designers to think about when constructing a communal machine.

