[ad_1]
The RIG exploit package (EK) touched an all-time excessive profitable exploitation charge of practically 30% in 2022, new findings reveal.
“RIG EK is a financially-motivated program that has been energetic since 2014,” Swiss cybersecurity firm PRODAFT mentioned in an exhaustive report shared with The Hacker News.
“Although it has but to considerably change its exploits in its more moderen exercise, the sort and model of the malware they distribute continuously change. The frequency of updating samples ranges from weekly to every day updates.”
Exploit kits are packages used to distribute malware to giant numbers of victims by benefiting from recognized safety flaws in commonly-used software program akin to net browsers.
The indisputable fact that RIG EK runs as a service mannequin means risk actors can financially compensate the RIG EK administrator for putting in malware of their alternative on sufferer machines. The RIG EK operators primarily make use of malvertising to make sure a excessive an infection charge and large-scale protection.
As a end result, guests utilizing a weak model of a browser to entry an actor-controlled net web page or a compromised-but-legitimate web site are redirected utilizing malicious JavaScript code to a proxy server, which, in flip, communicates with an exploit server to ship the suitable browser exploit.
The exploit server, for its half, detects the person’s browser by parsing the User-Agent string and returns the exploit that “matches the pre-defined weak browser variations.”
“The suave design of the Exploit Kit permits it to contaminate units with little to no interplay from the top person,” the researchers mentioned. “Meanwhile, its use of proxy servers makes infections more durable to detect.”
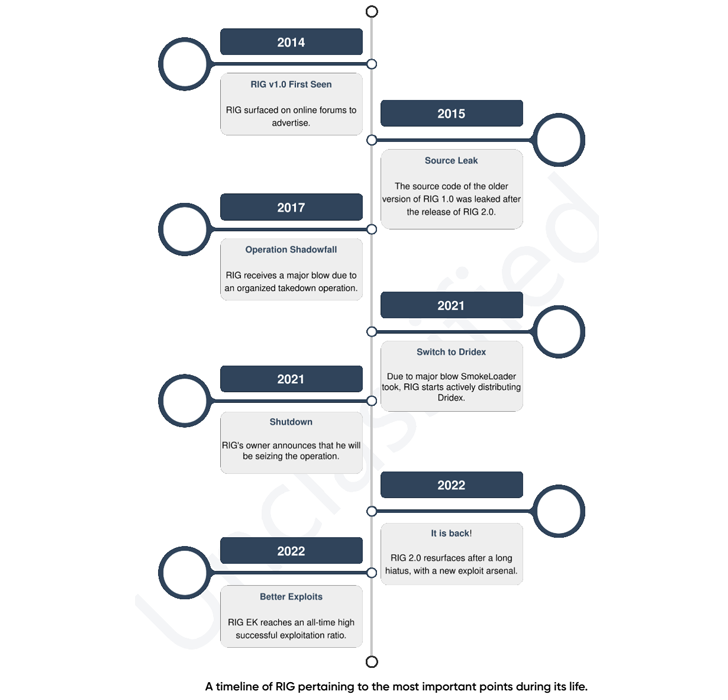
Since arriving on the scene in 2014, RIG EK has been noticed delivering a variety of economic trojans, stealers, and ransomware akin to AZORult, CryptoBit, Dridex, Raccoon Stealer, and WastedLoader. The operation was dealt an enormous blow in 2017 following a coordinated motion that dismantled its infrastructure.
Recent RIG EK campaigns have focused a reminiscence corruption vulnerability impacting Internet Explorer (CVE-2021-26411, CVSS rating: 8.8) to deploy RedLine Stealer.
Other browser flaws weaponized by the malware embody CVE-2013-2551, CVE-2014-6332, CVE-2015-0313, CVE-2015-2419, CVE-2016-0189, CVE-2018-8174, CVE-2019-0752, and CVE-2020-0674.
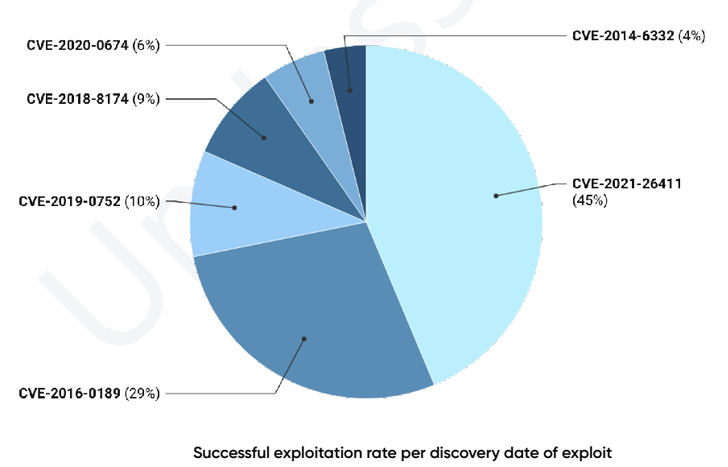
According to knowledge collected by PRODAFT, 45% of the profitable infections in 2022 leveraged CVE-2021-26411, adopted by CVE-2016-0189 (29%), CVE-2019-0752 (10%), CVE-2018-8174 (9%), and CVE-2020-0674 (6%).
Is Your Business Prepared for the Top SaaS 🛡️ Security Challenges of 2023? Learn How to Tackle Them – Join Our Webinar Now!
Besides Dridex, Raccoon, and RedLine Stealer, a number of the notable malware households distributed utilizing RIG EK are SmokeLoader, PureCrypter, IcedID, ZLoader, TrueBot, Ursnif, and Royal ransomware.
Furthermore, the exploit package is claimed to have attracted visitors from 207 nations, reporting a 22% success charge over the previous two months alone. The most variety of compromises are positioned in Russia, Egypt, Mexico, Brazil, Saudi Arabia, Turkey, and several other nations throughout Europe.
“Interestingly sufficient, the exploit strive charges have been the best on Tuesday, Wednesday and Thursday – with profitable infections happening on the identical days of the week,” the researchers defined.
PRODAFT, which additionally managed to achieve visibility into the package’s management panel, mentioned there are about six totally different customers, two of whom (admin and vipr) have admin privileges. A person profile with the alias “pit” or “pitty” has subadmin permissions, and three others (lyr, ump, and test1) have person privileges.
“admin” can also be a dummy person primarily reserved for creating different customers. The administration panel, which works with a subscription, is managed utilizing the “pitty” person.
However, an operational safety blunder that uncovered the git server led PRODAFT to de-anonymize two of the risk actors: a 31-year-old Uzbekistan nationwide named Oleg Lukyanov and a Russian who goes by the identify Vladimir Nikonov.
It additionally assessed with excessive confidence that the developer of the Dridex malware has a “shut relationship” with the RIG EK’s directors, owing to the extra handbook
configuration steps taken to “be sure that the malware was distributed easily.”
“Overall, RIG EK runs a really fruitful enterprise of exploit-as-a-service, with victims throughout the globe, a extremely efficient exploit arsenal and quite a few clients with continuously updating malware,” the researchers mentioned.