[ad_1]

Digital forensics is rising whereas being extra tied with incident response, in keeping with the most recent State of Enterprise Digital Forensics and Incident Response survey from Magnet Forensics. However, some digital forensics professionals are burned out and want extra automation and management within the DFIR subject, the place hiring is troublesome.
This survey from Magnet Forensics, which develops digital investigation options, was performed between October and November 2022.
Jump to:
Digital forensics more and more concerned with incident response
Digital forensics, generally known as pc forensics, has been an experience area that was principally deployed on single computer systems for a few years. The typical use circumstances had been to seek out information on an worker’s pc who was suspected of committing an offense, or investigating authorized or malware points comparable to data stealers.
Over time, assaults have grown in complexity and dimension and goal a number of computer systems or servers from firms, typically on the identical time. Digital forensics, which was all about analyzing full exhausting drive copies in an offline mode, noticed a twist when it turned vital to investigate working methods.
As a outcome, digital forensics discovered new methods to combine that complexity with incident response groups. It allowed extra deep-dive evaluation on methods whereas not shutting them down, and now digital forensics and incident response are often collectively within the SecOps workforce inside the Security Operations Center.
Targeted assaults are usually the case the place digital forensics works ideally with incident response. While incident response works on containing, resolving and recovering from an incident, digital forensics could be one of the best answer to seek out the foundation explanation for an incident.
The learnings from each incident response and digital forensics actions assist firms discover the weak spots of their defenses and implement new safeguards and processes.
Most frequent DFIR incidents
According to Magnet Forensics, information exfiltration or IP theft represents 35% of the general exercise and is the commonest DFIR incident, adopted intently by enterprise e mail compromise (Figure A). Fourteen % of the survey respondents indicated that their group encounters BEC scams very incessantly. Other frequent incidents are worker misconduct, misuse of property or coverage violations, inner fraud and ransomware-infected endpoints.
Figure A
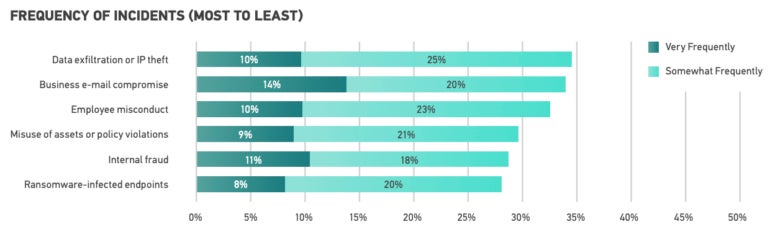
Data exfiltration, IP theft and ransomware have a big impact on organizations. DFIR professionals have a tough time engaged on it, as a result of expertise and gear are essential to quickly examine ransomware and information breach incidents, whereas cybercriminals attempt to render these investigations as troublesome as attainable.
The challenges of evolving cyberattack methods
Attacks are evolving in dimension and complexity, with risk actors utilizing extra methods to make detection tougher; because of this, 42% of DFIR professionals point out evolving cyberattack methods current both an excessive or giant drawback of their group.
Staying updated about such cyberattacks is a problem, with firms relying extra on R&D specialists specializing in equipping the group with new and ever-evolving ways, methods and procedures. Great sources of knowledge relating to evolving threats embrace MITRE, CISA, and LinkedIn or Twitter accounts of cybersecurity researchers.
More automation for DFIR is required
A number of repetitive duties must be finished in DFIR, and instruments automating these duties are sometimes wanted.
SOCs already make use of automation as a lot as attainable, as they should cope with telemetry, however automation for digital forensics is completely different, because it principally wants information processing by orchestrating, performing and monitoring forensic workflows.
Half of DFIR professionals point out that investments in automation could be vastly precious for a spread of DFIR capabilities, as workflows nonetheless rely an excessive amount of upon the guide execution of many repetitive duties.
More than 20% of the survey respondents indicated automation could be principally precious for the distant acquisition of goal endpoints, the triage of goal endpoints, and processing of digital proof, in addition to documenting, summarizing and reporting on incidents.
The survey respondents indicated that the rising quantity of investigations and information is both an excessive (13%) or giant (32%) drawback (Figure B).
Figure B
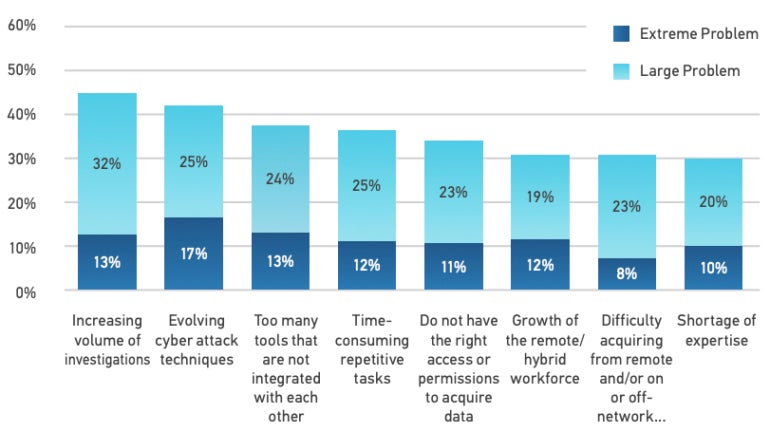
DFIR personnel challenges
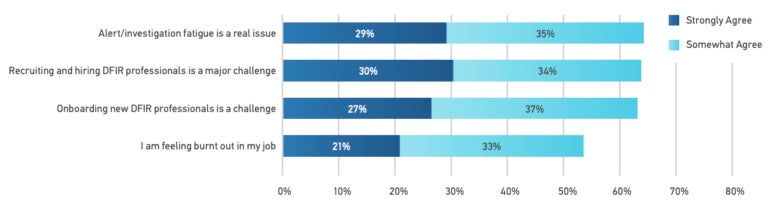
Nearly 30% of company DFIR practitioners agree that investigation fatigue is an actual difficulty, whereas 21% strongly agree that they really feel burnt out of their jobs. The quantity of investigations and information, and the stress attributable to the need of working incident responses quick, makes it troublesome for these professionals to loosen up. Automation may assist save these professionals time and allow quicker evaluation.
Recruitment is indicated as a serious problem by 30% of the survey respondents, whereas onboarding new DFIR professionals will also be troublesome as a result of the job may fluctuate rather a lot based mostly on the corporate; as an illustration, this might impression the instruments used (Figure C).
Figure C
More DFIR management is required to assist with information and laws
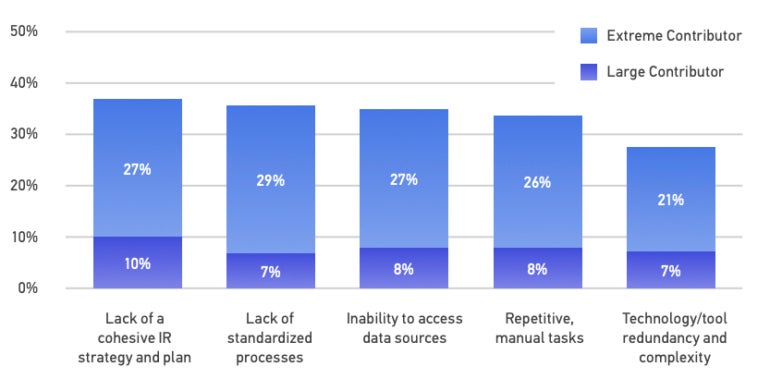
A subject beneath such fast evolution wants knowledgeable and decisive management to set methods and direct sources in an environment friendly manner. Leaders affect the best way DFIR professionals can effectively entry information sources they want, which is commonly troublesome, as greater than a 3rd of the survey respondents indicated.
The greatest contributions to wasted sources are the dearth of a cohesive incident response technique and plan and the dearth of standardized processes (Figure D).
Figure D
Regulations are one other problem for DFIR professionals. For occasion, 67% of DFIR professionals indicated that their position has been impacted by new reporting laws, and 46% of the respondents reported not having sufficient time to completely perceive new and altering laws. Leaders want to know laws and determine the best way to deal with them, maybe by releasing up DFIR groups’ time to review the laws or consulting with the corporate’s authorized division.
Outsourcing with DFIR investigations is frequent
Most firms typically outsource elements of their DFIR investigations, principally as a result of there’s a lack of these abilities internally. Almost half of the respondents (47%) point out the lack of know-how because the prior cause for utilizing service suppliers, whereas the second cause (38%) cited just isn’t having the required toolset, which could be extraordinarily costly in some circumstances.
DFIR suggestions for companies
Companies ought to spend money on DFIR options that prioritize pace, accuracy and completeness. More delays means extra danger in relation to analyzing incidents.
Automation needs to be strongly enforced to assist DFIR professionals cut back burnout and cut back investigation delays.
An incident response plan is crucial. The plan will make clear roles and tasks and element how forensics and incident response must be finished. It also needs to assist accessing information with clear directives and indications as to who gives what within the firm. Critical positions to offer entry to information needs to be reachable 24/7.
Regulations and legislations must be totally understood by DFIR groups. More typically, all the things that may very well be finished upfront to arrange for future incidents needs to be rigorously considered and finished when not engaged on an incident.
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
Read subsequent: Security Incident Response Policy (TechRepublic Premium)
