[ad_1]
Canada’s second-largest telecom, TELUS is investigating a possible knowledge breach after a risk actor shared samples on-line of what seems to be worker knowledge. The risk actor subsequently posted screenshots that apparently present personal supply code repositories and payroll data held by the corporate.
TELUS has up to now not discovered proof of company or retail buyer knowledge being stolen and continues to watch the potential incident.
Private supply code and worker knowledge up on the market
On February 17, a risk actor put up what they declare to be TELUS’ worker checklist (comprising names and e-mail addresses) on the market on an information breach discussion board.
“TELUS employes [sic] from a really latest breach. We have over 76K distinctive emails and on high of this, we’ve inner data related to every worker scraped from Telus’ API,” states the discussion board submit.
While BleepingComputer has been unable to verify the veracity of risk actor’s claims simply but, the small pattern set posted by the vendor does have legitimate names and e-mail addresses similar to present-day TELUS workers, notably software program builders and technical workers.
By Tuesday, February 21, the identical risk actor had created one other discussion board submit—this time providing to promote TELUS’ personal GitHub repositories, supply code, in addition to the corporate’s payroll data.
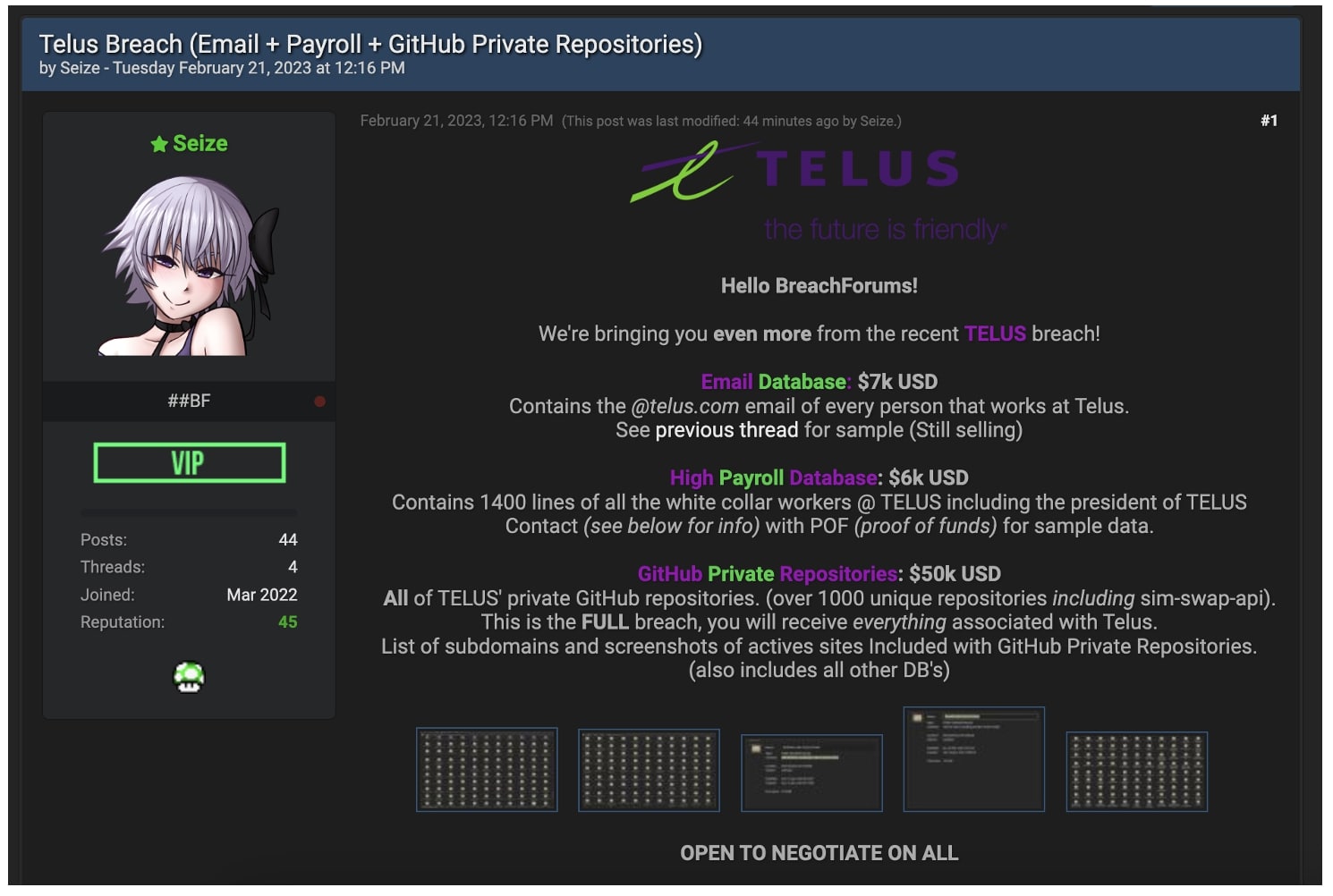
“In the repositories are the backend, frontend, middleware [information,] AWS keys, Google auth keys, Source Code, Testing Apps, Staging/Prod/testing and extra!” states the vendor’s newest submit.
The vendor additional boasts that the stolen supply code comprises the corporate’s “sim-swap-api” that can purportedly allow adversaries to hold out SIM swap assaults.
Although the risk actor has labeled this a “FULL breach” and guarantees to promote “all the things related to Telus,” it’s too early to conclude that an incident certainly occurred at TELUS or to rule out a third-party vendor breach.
“We are investigating claims {that a} small quantity of knowledge associated to inner TELUS supply code and choose TELUS crew members’ data has appeared on the darkish net,” a TELUS spokesperson advised BleepingComputer.
“We can verify that up to now our investigation, which we launched as quickly as we have been made conscious of the incident, has not recognized any company or retail buyer knowledge.”
BleepingComputer continues to watch the event and give you updates on the state of affairs.
TELUS workers and prospects, within the meantime, ought to look out for any phishing or rip-off messaging concentrating on them and chorus from entertaining such e-mail, textual content, or phone communications.
h/t Dominic Alvieri
