[ad_1]
Telecommunication service suppliers within the Middle East are being focused by a beforehand undocumented menace actor as a part of a suspected intelligence gathering mission.
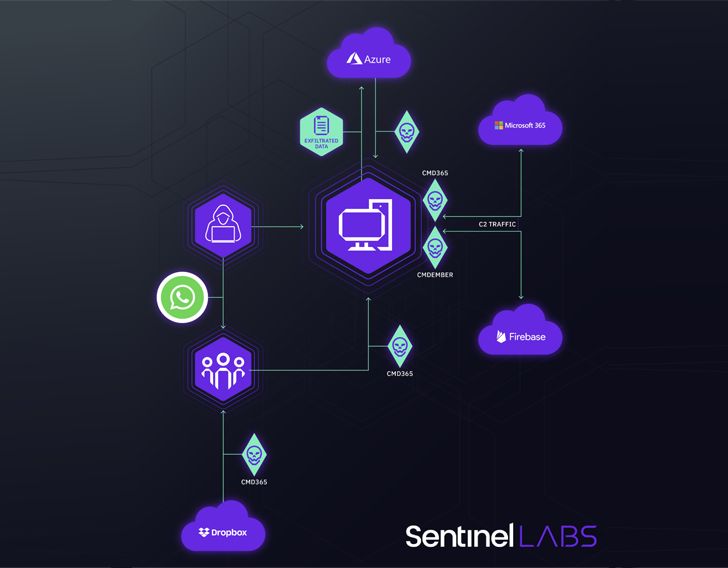
Cybersecurity corporations SentinelOne and QGroup are monitoring the exercise cluster beneath the previous’s work-in-progress moniker WIP26.
“WIP26 depends closely on public cloud infrastructure in an try and evade detection by making malicious site visitors look legit,” researchers Aleksandar Milenkoski, Collin Farr, and Joey Chen stated in a report shared with The Hacker News.
This contains the misuse of Microsoft 365 Mail, Azure, Google Firebase, and Dropbox for malware supply, information exfiltration, and command-and-control (C2) functions.
The preliminary intrusion vector used within the assaults entails “precision concentrating on” of workers by way of WhatsApp messages that comprise hyperlinks to Dropbox hyperlinks to supposedly benign archive recordsdata.
The recordsdata, in actuality, harbor a malware loader whose core function is to deploy customized .NET-based backdoors akin to CMD365 or CMDEmber that leverage Microsoft 365 Mail and Google Firebase for C2.
“The principal performance of CMD365 and CMDEmber is to execute attacker-provided system instructions utilizing the Windows command interpreter,” the researchers stated. “This functionality was used to conduct quite a lot of actions, akin to reconnaissance, privilege escalation, staging of further malware, and information exfiltration.”
CMD365, for its half, works by scanning the inbox folder for particular emails that start with the topic line “enter” to extract the C2 instructions for execution on the contaminated hosts. CMDEmber, alternatively, sends and receives information from the C2 server by issuing HTTP requests.
Transmitting the info – which contains customers’ personal internet browser data and particulars about high-value hosts within the sufferer’s community – to actor-controlled Azure cases is orchestrated by way of PowerShell instructions.
The abuse of cloud companies for nefarious ends just isn’t extraordinary, and the most recent marketing campaign from WIP26 signifies continued makes an attempt on the a part of menace actors to evade detection.
This just isn’t the primary time telecom suppliers within the Middle East have come beneath the radar of espionage teams. In December 2022, Bitdefender disclosed particulars of an operation dubbed BackdoorDiplomacy aimed toward a telecom firm within the area to siphon helpful information.