[ad_1]
Authored by SangRyol Ryu
Cybercriminals are at all times after unlawful promoting income. As we now have beforehand reported, we now have seen many cell malwares masquerading as a great tool or utility, and routinely crawling adverts within the background. Recently the McAfee Mobile Research Team has recognized new Clicker malware that sneaked into Google Play. In complete 16 functions that have been beforehand on Google Play have been confirmed to have the malicious payload with an assumed 20 million installations.
McAfee safety researchers notified Google and the entire recognized apps are now not obtainable on Google Play. Users are additionally protected by Google Play Protect, which blocks these apps on Android. McAfee Mobile Security merchandise detect this risk as Android/Clicker and shield you from malware. For extra info, to get totally protected, go to McAfee Mobile Security.
The malicious code was discovered on helpful utility functions like Flashlight (Torch), QR readers, Camara, Unit converters, and Task managers:

Once the appliance is opened, it downloads its distant configuration by executing an HTTP request. After the configuration is downloaded, it registers the FCM (Firebase Cloud Messaging) listener to obtain push messages. At first look, it looks as if well-made android software program. However, it’s hiding advert fraud options behind, armed with distant configuration and FCM strategies.
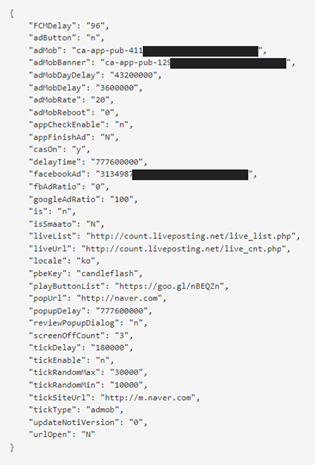
| Attribute title | Known which means of the worth |
| FCMDelay | Initial begin hours after first set up |
| adButton | Visivility of a button of Advertisement |
| adMob | AdMob unit ID |
| adMobBanner | AdMob unit ID |
| casOn | Whether CAS library works or not |
| fbAd | FaceBook Ad ID |
| fbAdRatio | Ratio of FB AD |
| googleAdRatio | Ratio of AdMob |
| is | Decide BootService to run or not |
| urlOpen | to open popup or not when begins PowerService |
| popUrl | URL for PowerService |
| popUpDelay | Delay time for PowerService |
| liveUrl | URL for livecheck service |
| pbeKey | Key for making distinctive string |
| playButtonList | URL for different service |
| reviewPopupDialog | ‘y’ it reveals evaluation dialog |
| tickDelay | Delay time for TickService |
| tickEnable | Value of TickService enabled |
| tickRandomMax | Value of TickService random delay |
| tickRandomMin | Value of TickService random delay |
| tickType | Set the kind of TickService |
| updateNotiVersion | Value for displaying replace exercise |
The FCM message has varied kinds of info and that features which operate to name and its parameters. The image beneath reveals a few of FCM message historical past:
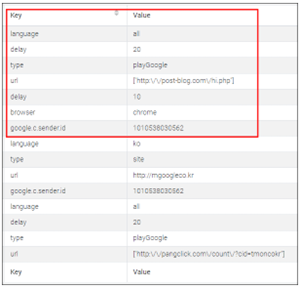
When an FCM message receives and meets some situation, the latent operate begins working. Mainly, it’s visiting web sites that are delivered by FCM message and searching them successively within the background whereas mimicking consumer’s habits. This might trigger heavy community site visitors and devour energy with out consumer consciousness throughout the time it generates revenue for the risk actor behind this malware. In the image beneath there’s an instance of the community site visitors generated to get the data required to generate pretend clicks and the web sites visited with out consumer’s consent or interplay:
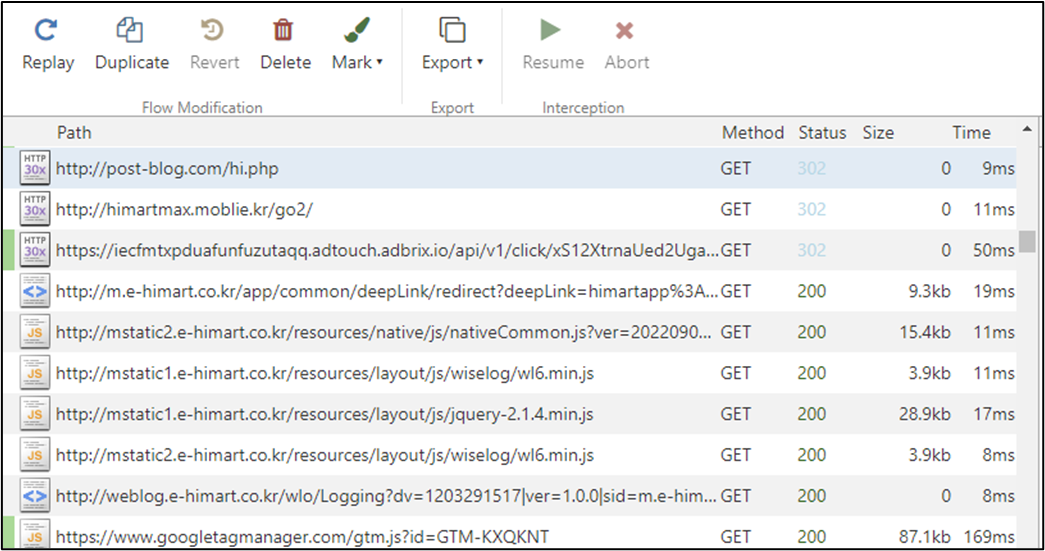
So far, we now have recognized two items of code associated to this risk. One is “com.click.cas” library which focuses on the automated clicking performance whereas “com.liveposting” library works as an agent and runs hidden adware companies:
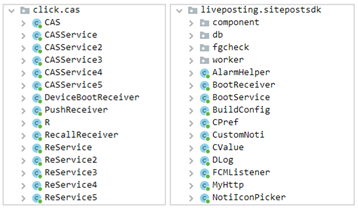
Depending on the model of the functions, some have each libraries working collectively whereas different functions solely have “com.liveposting” library. The malware is utilizing set up time, random delay and consumer presence to keep away from the customers from noticing these malicious acts. The malicious habits received’t begin if the set up time is inside an hour and throughout the time the consumer is utilizing the system, in all probability to remain beneath the radar and keep away from being detected instantly:
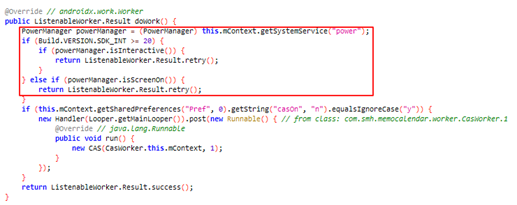
Clicker malware targets illicit promoting income and may disrupt the cell promoting ecosystem. Malicious habits is cleverly hidden from detection. Malicious actions reminiscent of retrieving crawl URL info by way of FCM messages begin within the background after a sure time period and will not be seen to the consumer.
McAfee Mobile Security detects and removes malicious functions like this one which will run within the background with out consumer’s data. Also, we suggest having a safety software program put in and activated so you’ll be notified of any cell threats current in your system in a well timed method. Once you take away this and different malicious functions, you possibly can count on an prolonged battery time and you’ll discover diminished cell knowledge utilization whereas making certain that your delicate and private knowledge is protected against this and different kinds of threats.
liveposting[.]web
sideup[.]co[.]kr
msideup[.]co[.]kr
post-blog[.]com
pangclick[.]com
modooalba[.]web
| SHA256 | Package title | Name | Downloaded |
| a84d51b9d7ae675c38e260b293498db071b1dfb08400b4f65ae51bcda94b253e | com.hantor.CozyCamera | High-Speed Camera | 10,000,000+ |
| 00c0164d787db2ad6ff4eeebbc0752fcd773e7bf016ea74886da3eeceaefcf76 | com.james.SmartTaskManager | Smart Task Manager | 5,000,000+ |
| b675404c7e835febe7c6c703b238fb23d67e9bd0df1af0d6d2ff5ddf35923fb3 | kr.caramel.flash_plus | Flashlight+ | 1,000,000+ |
| 65794d45aa5c486029593a2d12580746582b47f0725f2f002f0f9c4fd1faf92c | com.smh.memocalendar | 달력메모장 | 1,000,000+ |
| 82723816760f762b18179f3c500c70f210bbad712b0a6dfbfba8d0d77753db8d | com.joysoft.wordBook | Ok-Dictionary | 1,000,000+ |
| b252f742b8b7ba2fa7a7aa78206271747bcf046817a553e82bd999dc580beabb | com.kmshack.BusanBus | BusanBus | 1,000,000+ |
| a2447364d1338b73a6272ba8028e2524a8f54897ad5495521e4fab9c0fd4df6d | com.candlencom.candleprotest | Flashlight+ | 500,000+ |
| a3f484c7aad0c49e50f52d24d3456298e01cd51595c693e0545a7c6c42e460a6 | com.movinapp.quicknote | Quick Note | 500,000+ |
| a8a744c6aa9443bd5e00f81a504efad3b76841bbb33c40933c2d72423d5da19c | com.smartwho.SmartCurrencyConverter | Currency Converter | 500,000+ |
| 809752e24aa08f74fce52368c05b082fe2198a291b4c765669b2266105a33c94 | com.joysoft.barcode | Joycode | 100,000+ |
| 262ad45c077902d603d88d3f6a44fced9905df501e529adc8f57a1358b454040 | com.joysoft.ezdica | EzDica | 100,000+ |
| 1caf0f6ca01dd36ba44c9e53879238cb46ebb525cb91f7e6c34275c4490b86d7 | com.schedulezero.instapp | Instagram Profile Downloader | 100,000+ |
| 78351c605cfd02e1e5066834755d5a57505ce69ca7d5a1995db5f7d5e47c9da1 | com.meek.tingboard | Ez Notes | 100,000+ |
| 4dd39479dd98124fd126d5abac9d0a751bd942b541b4df40cb70088c3f3d49f8 | com.candlencom.flashlite | 손전등 | 1,000+ |
| 309db11c2977988a1961f8a8dbfc892cf668d7a4c2b52d45d77862adbb1fd3eb | com.doubleline.calcul | 계산기 | 100+ |
| bf1d8ce2deda2e598ee808ded71c3b804704ab6262ab8e2f2e20e6c89c1b3143 | com.dev.imagevault | Flashlight+ | 100+ |
