[ad_1]
A brand new Linux model of Royal ransomware is concentrating on VMware ESXi digital machines. Learn extra about this safety risk and find out how to defend from it.
Royal ransomware is malware that first appeared round September 2022. The folks behind this ransomware are in all probability a subgroup of the notorious Conti risk actor. This subgroup, which is named Conti Team 1, launched the Zion ransomware earlier than rebranding it as Royal ransomware.
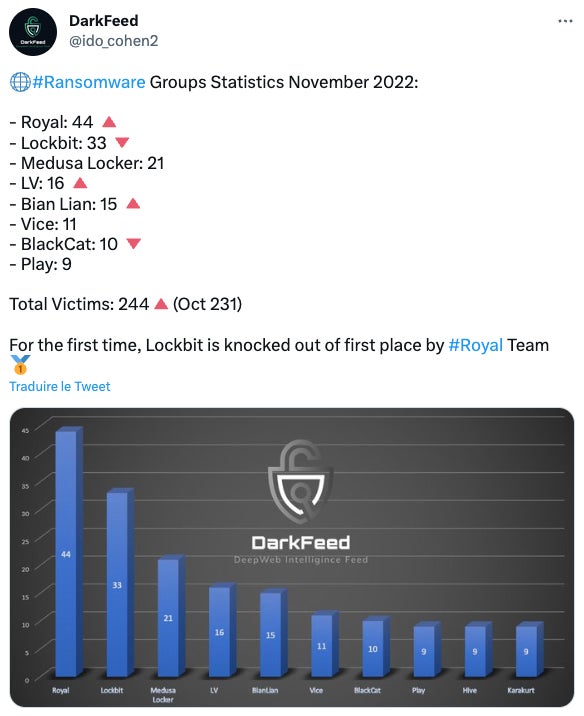
Royal unfold so quick as a result of it grew to become the ransomware making the largest variety of victims in November 2022 (Figure A), taking the lead in entrance of the LockBit ransomware.
Figure A
Jump to:
Royal ransomware’s supply methods
The Royal ransomware is unfold through a number of methods with the most typical method being phishing, in accordance with Cyble Research & Intelligence Labs.
The malware was reported in November 2022 by insurance coverage firm At-Bay as being doubtless the primary ransomware to efficiently exploit a Citrix vulnerability, CVE-2022-27510, and achieve entry to gadgets with Citrix ADC or Citrix Gateway to function ransomware assaults. The risk actor used the Citrix vulnerability earlier than any public exploit, displaying that the ransomware group is amongst essentially the most subtle ransomware risk actors.
Royal ransomware additionally is likely to be unfold by malware downloaders, akin to QBot or BATLOADER.
Contact kinds from corporations had been additionally used to distribute the ransomware. The risk actor first initiates a dialog on the goal’s contact type, and as soon as a reply is supplied by electronic mail, an electronic mail containing a hyperlink to BATLOADER is shipped to the goal with the intention to function Royal ransomware ultimately.
Royal ransomware has additionally been distributed through Google Ads or through the set up of faux software program pretending to be reputable akin to Microsoft Teams or Zoom, hosted on pretend web sites trying reputable. Microsoft reported a few pretend TeamViewer web site that delivered a BATLOADER executable that deployed Royal ransomware (Figure B).
Figure B

Uncommon file codecs akin to Virtual Hard Disk impersonating reputable software program have additionally been used as first stage downloaders for Royal ransomware.
Royal ransomware’s targets
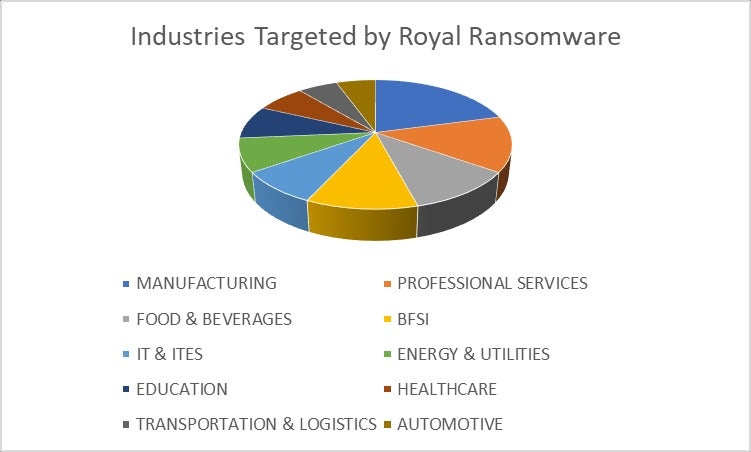
The most impacted industries focused by Royal ransomware are manufacturing, skilled companies, and meals and drinks (Figure C).
Figure C
As for the situation of these industries, Royal ransomware principally targets the U.S., adopted by Canada and Germany (Figure D).
Figure D

The monetary vary for the ransoms requested by the group varies relying on the goal from $250,000 USD to over $2 million USD.
A brand new Linux risk concentrating on VMware ESXi
The new Royal ransomware pattern reported by Cyble is a 64-bit Linux executable compiled utilizing GNU Compiler Collection. The malware first performs an encryption check that terminates the malware if it fails; it consists of merely encrypting the phrase “test” and checking the outcome.
SEE: Massive ransomware operation targets VMware ESXi (TechRepublic)
The malicious code then collects details about working VMware ESXi digital machines through the esxcli command-line instrument and saves the output in a file earlier than terminating the entire digital machines by utilizing as soon as once more the esxcli instrument.
Multi-threading is then deployed by the ransomware to encrypt recordsdata, excluding a couple of recordsdata akin to its personal recordsdata: readme and royal_log_* recordsdata and recordsdata with .royal_u and .royal_w file extensions. It additionally excludes .sf, .v00 and .b00 extensions. A mix of RSA and AES encryption algorithms is used for the encryption.
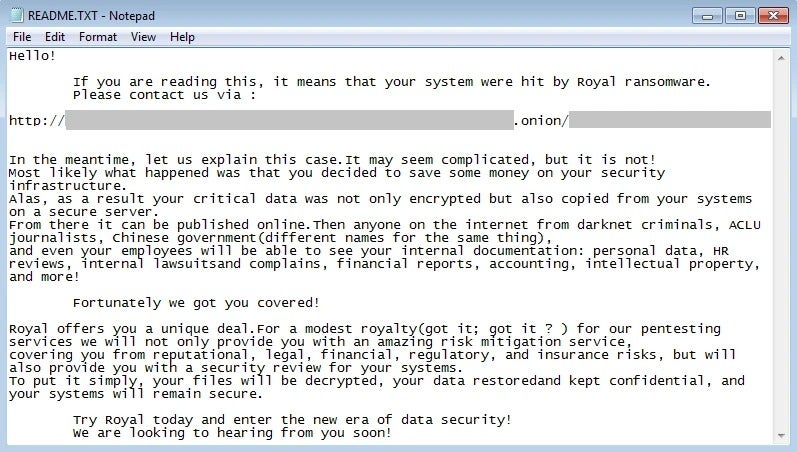
As the malware encrypts knowledge, it creates the ransom notes in a parallel course of (Figure E).
Figure E
How to guard from this Royal ransomware risk
Since the risk actor makes use of a wide range of methods to breach corporations and deploy the Royal ransomware, a number of vectors of an infection should be secured. Further, the risk actor has already proved it was in a position to set off private exploits on software program, so all working programs and software program should be all the time updated and patched.
Emails are essentially the most generally used approach for breaching corporations, and that is true for the Royal ransomware gang. Therefore, safety options should be deployed on the net servers, and admins ought to verify all hooked up recordsdata and hyperlinks contained inside emails for any malicious content material. The verify mustn’t solely be an automatic static evaluation but in addition a dynamic one through sandboxes.
Browsers’ content material must be analyzed, and shopping to unknown or low-reputation web sites must be blocked, because the Royal ransomware gang typically makes use of new pretend web sites to unfold their malware.
Data backup processes must be established, with backups being repeatedly achieved however stored offline.
Finally, workers must be made conscious of this ransomware risk, significantly those that manipulate emails from unknown sources, akin to press relations or human sources.
Read subsequent: Security Awareness and Training Policy (TechRepublic Premium)
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
