[ad_1]

Exploit code has been launched for an actively exploited zero-day vulnerability affecting Internet-exposed GoAnywhere MFT administrator consoles.
GoAnywhere MFT is a web-based and managed file switch device designed to assist organizations to switch recordsdata securely with companions and hold audit logs of who accessed the shared recordsdata.
Its developer is Fortra (previously often called HelpSystems), the outfit behind the broadly abused Cobalt Strike menace emulation device.
On Monday, safety researcher Florian Hauser of IT safety consulting agency Code White launched technical particulars and proof-of-concept exploit code that performs unauthenticated distant code execution on susceptible GoAnywhere MFT servers.
“I may present a working PoC (examine hash and time of my tweet) to my teammates inside hours on the identical day to guard our purchasers first,” Hauser stated.
Fortra says that “the assault vector of this exploit requires entry to the executive console of the applying, which typically is accessible solely from inside a personal firm community, by VPN, or by allow-listed IP addresses (when working in cloud environments, reminiscent of Azure or AWS).”
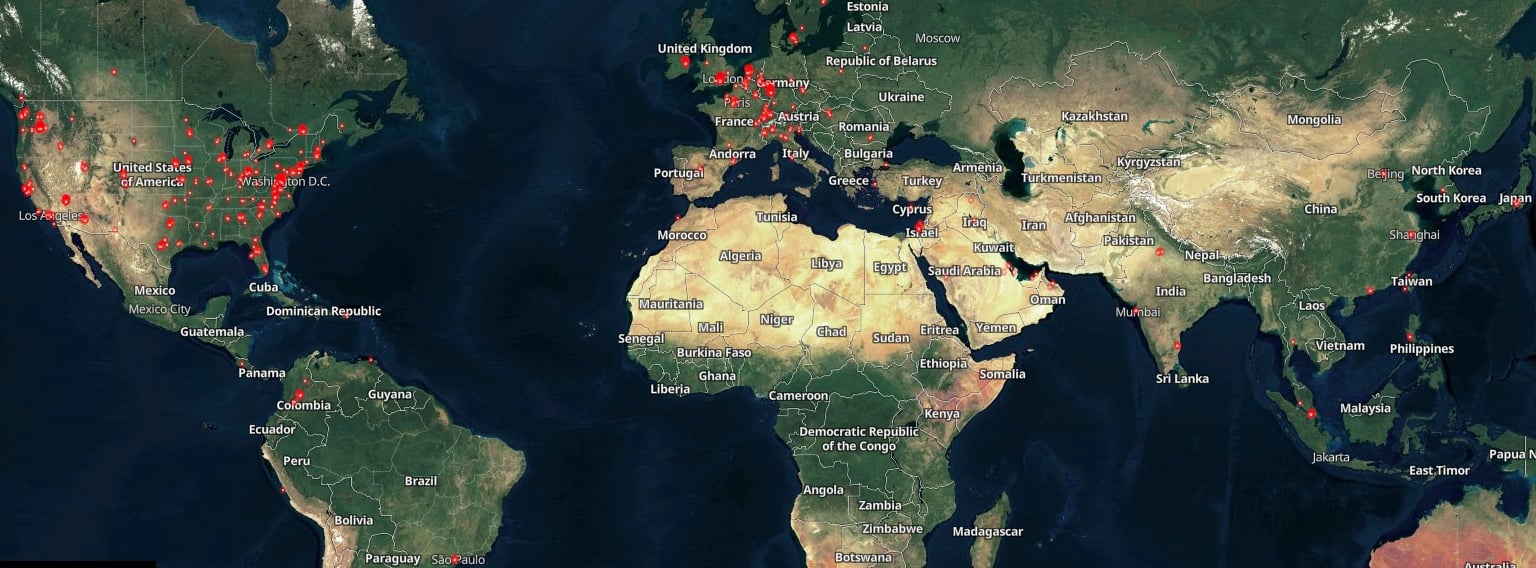
However, a Shodan scan exhibits that virtually 1,000 GoAnywhere situations are uncovered on the Internet, though simply over 140 are on ports 8000 and 8001 (those utilized by the susceptible admin console).
Mitigation accessible
The firm is but to publicly acknowledge this distant pre-authentication RCE safety flaw exploited in assaults (to learn the advisory, you want to create a free account first) and hasn’t launched safety updates to deal with the vulnerability, thus leaving all uncovered installations susceptible to assaults.
However, the non-public advisory offers indicators of compromise, together with a particular stacktrace that exhibits up within the logs on compromised programs.
“If this stacktrace is within the logs, it is extremely probably this technique has been the goal of assault,” Fortra says.
It additionally accommodates mitigation recommendation that features implementing entry controls to permit entry to the GoAnywhere MFT administrative interface solely from trusted sources or disabling the licensing service.
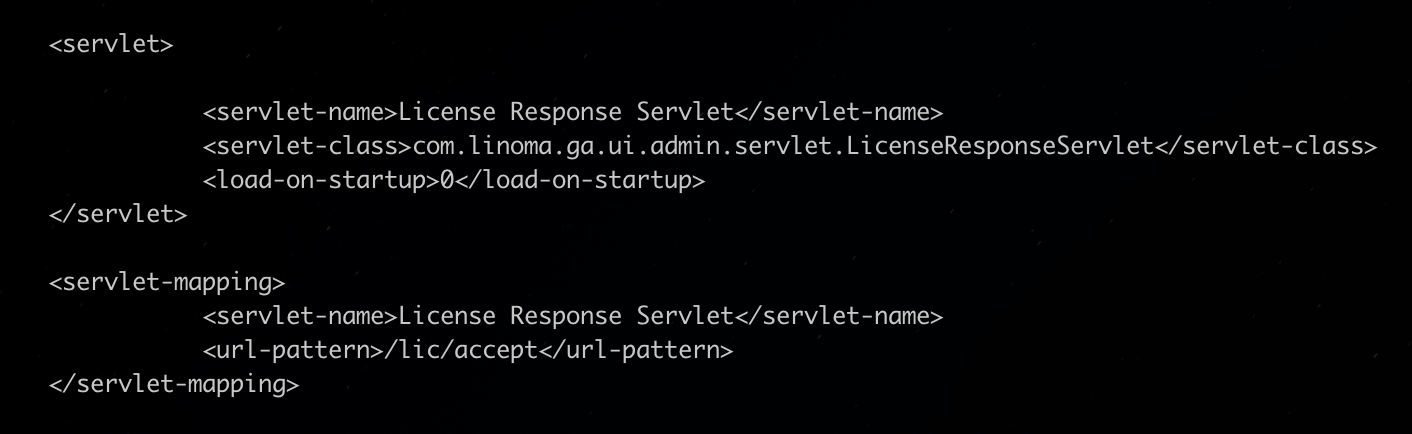
To disable the licensing server, admins need to remark out or delete the servlet and servlet-mapping configuration for the License Response Servlet within the internet.xml file to disable the susceptible endpoint. A restart is required to use the brand new configuration.
“Due to the truth that information in your surroundings may have been accessed or exported, it’s best to decide whether or not you’ve gotten saved credentials for different programs within the surroundings and ensure these credentials have been revoked,” Fortra added in an replace issued on Saturday.
“This contains passwords and keys used to entry any exterior programs with which GoAnywhere is built-in.
“Ensure that each one credentials have been revoked from these exterior programs and assessment related entry logs associated to these programs. This additionally contains passwords and keys used to encrypt recordsdata inside the system.”
Fortra additionally recommends taking the next measures after mitigation in environments with suspicion or proof of an assault:
- Rotate your Master Encryption Key.
- Reset credentials – keys and/or passwords – for all exterior buying and selling companions/programs.
- Review audit logs and delete any suspicious admin and/or internet person accounts
- Contact assist by way of the portal https://my.goanywhere.com/, electronic mail goanywhere.assist@helpsystems.com, or telephone 402-944-4242 for additional help.