[ad_1]
The Iranian nation-state hacking group generally known as OilRig has continued to focus on authorities organizations within the Middle East as a part of a cyber espionage marketing campaign that leverages a brand new backdoor to exfiltrate knowledge.
“The marketing campaign abuses respectable however compromised e mail accounts to ship stolen knowledge to exterior mail accounts managed by the attackers,” Trend Micro researchers Mohamed Fahmy, Sherif Magdy, and Mahmoud Zohdy mentioned.
While the method in itself will not be exceptional, the event marks the primary time OilRig has adopted it in its playbook, indicating the continued evolution of its strategies to bypass safety protections.
The superior persistent menace (APT) group, additionally known as APT34, Cobalt Gypsy, Europium, and Helix Kitten, has been documented for its focused phishing assaults within the Middle East since not less than 2014.
Linked to Iran’s Ministry of Intelligence and Security (MOIS), the group is thought to make use of a various toolset in its operations, with current assaults in 2021 and 2022 using backdoors resembling Karkoff, Shark, Marlin, and Saitama for info theft.
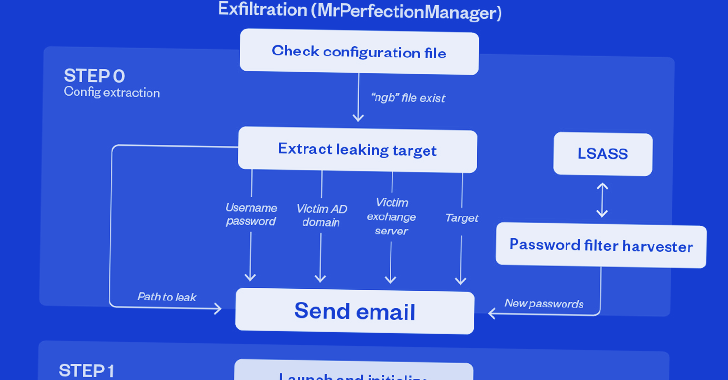
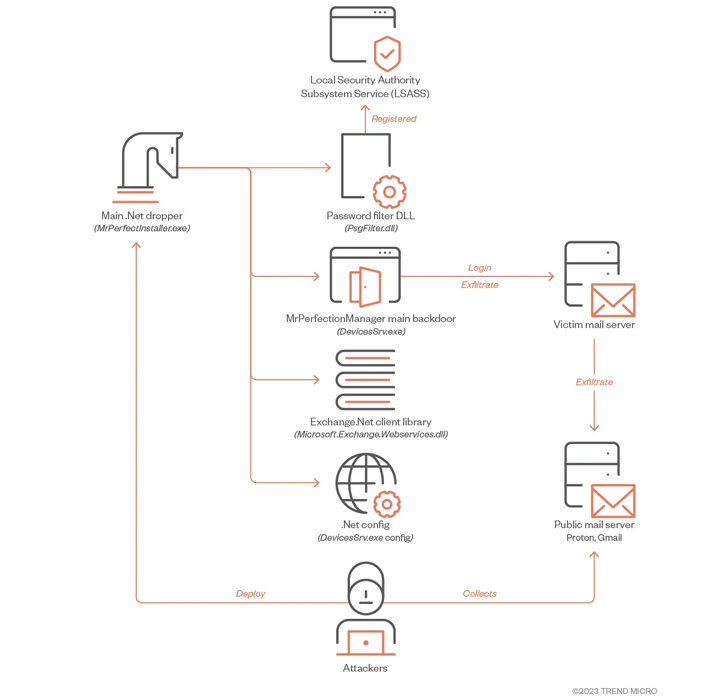
The start line of the most recent exercise is a .NET-based dropper that is tasked with delivering 4 completely different information, together with the principle implant (“DevicesSrv.exe”) accountable for exfiltrating particular information of curiosity.
Also put to make use of within the second stage is a dynamic-link library (DLL) file that is able to harvesting credentials from area customers and native accounts.
The most notable facet of the .NET backdoor is its exfiltration routine, which entails utilizing the stolen credentials to ship digital missives to actor-controlled e mail Gmail and Proton Mail addresses.
“The menace actors relay these emails by way of authorities Exchange Servers utilizing vaild accounts with stolen passwords,” the researchers mentioned.
The marketing campaign’s connections to APT34 stems from similarities in between the first-stage dropper and Saitama, the victimology patterns, and using internet-facing alternate servers as a communication technique, as noticed within the case of Karkoff.
If something, the rising variety of malicious instruments related to OilRig signifies the menace actor’s “flexibility” to give you new malware primarily based on the focused environments and the privileges possessed at a given stage of the assault.
“Despite the routine’s simplicity, the novelty of the second and final levels additionally point out that this complete routine can simply be a small a part of an even bigger marketing campaign concentrating on governments,” the researchers mentioned.