[ad_1]
Financial provide chain compromises, a subcategory of BECs, seem like ascendant and extremely efficient. Abnormal Security has recognized one pernicious menace actor that it has dubbed Firebrick Ostrich, which is utilizing a subtype of those gambits to trick targets into making funds.
The agency beforehand recognized 4 varieties of monetary provide chain compromise, which dispense with impersonation of inside executives on the goal firm and as an alternative put on the garb of one of many firm’s distributors. Abnormal Security says Firebrick Ostrich has used one in every of most of these monetary provide chain compromises — third-party reconnaissance assaults — to commit 346 BEC campaigns courting again to April 2021, impersonating 151 organizations and utilizing 212 maliciously registered domains, practically all within the U.S.
Crane Hassold, director of menace intelligence at Abnormal Security, stated the sum of money that may be gotten from exterior, third-party impersonation is 3 times larger than conventional BEC exploits, and that their success stems from consciousness deficit, as firms and their staff are educated to search for emails impersonating an inside government, not a vendor.
“Also, when you look at third-party reconnaissance and other financial supply chain attacks, the effectiveness of the lure is in the amount of information they are able to put in emails — information that makes them look a lot more realistic than other forms of BEC,” he stated.
SEE: Mobile machine safety coverage (TechRepublic Premium)
Hassold famous that tens of billions of {dollars} have been misplaced because of BECs in any given 12 months, and that BECs are a number one trigger of monetary loss at enterprises going again to 2016.
“BECs really exploded and peaked in the first six months last year, driven by attackers impersonating external entities, a big change because, since its inception, BECs have primarily involved impersonating internal entities,” he stated. “BEC actors have identified third parties — including vendors — as a weak link in the chain.”
Jump to:
Big positive aspects from low-tech impersonation
From the angle of cybercrime as a enterprise, the overhead wanted to launch third-party reconnaissance assaults is low, based on Hassold; it requires primary reconnaissance and knowledge gathering, with out underlying infrastructure or builders to keep up and improve malware. “It’s just sending out emails, so from the overhead perspective it’s fantastically lucrative,” he stated.
Third-party impersonation exploits, most of which originate from West Africa, per Abnormal, use a three-step course of (Figure A).
Figure A
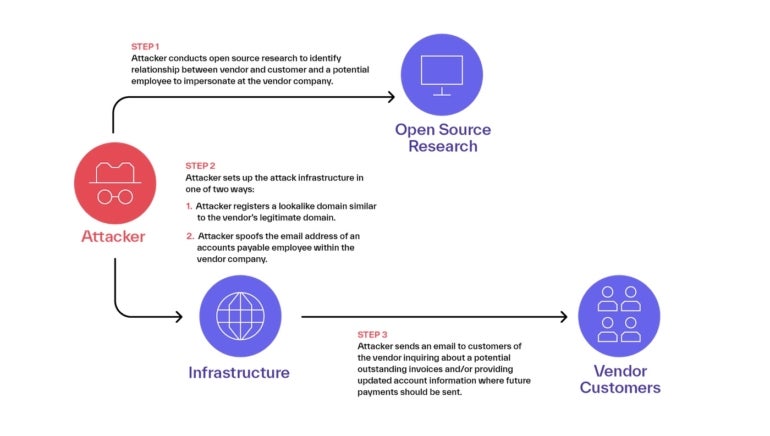
- Open-source analysis on vendor buyer relationships, which may come from state and native governments that supply detailed details about present and former contracts, or a vendor’s web site the place the corporate has displayed the names or logos of their prospects, and even googling firm names to see attainable connections.
- Attack infrastructure: The group registers a site, utilizing Namecheap or Google as registrar that impersonates the seller area, and spoofs the e-mail addresses of accounts payable staff inside the vendor firm.
- Targeted e mail to prospects: The attacker sends an e mail to prospects of the seller inquiring about potential excellent invoices or offering up to date account info the place future funds must be despatched.
Attacking inside every week of registering the area identify
According to Abnormal Security, Firebrick Ostrich’s use of newly-registered domains highlights how younger domains, along with different behavioral indicators, can be utilized as an efficient sign to determine threats. Abnormal Security reported that 60% of the domains registered by Firebrick Ostrich had been registered on the identical day because the execution of the BEC marketing campaign through which they’re deployed; roughly three quarters of their domains had been obtained inside 48 hours of an assault, and 89% of their domains had been registered inside every week of a marketing campaign.
SEE: Here’s how IT budgets ought to fill cybersecurity moats in 2023 (TechRepublic)
Using the newly-registered domains, Firebrick Ostrich creates e mail addresses impersonating precise vendor accounts employees that they then use to facilitate their assault, with the first account speaking with a goal by mimicking a vendor’s precise accounts receivable specialist. The supplemental e mail accounts, which might embrace monetary executives on the vendor, add a layer of authenticity to their assaults, per the agency.
“Reasonable” requests and a long-game tactic
Abnormal Security’s report stated the preliminary e mail in a Firebrick Ostrich assault sometimes begins with a greeting like the seller “greatly appreciates you as a valued customer and we want to thank you for your continued business,” adopted by two attainable requests:
- The first request signifies the seller want to replace the checking account on file with the shopper. The e mail makes some extent to say that the seller is unable to obtain funds by way of examine, so ACH and wire switch funds are the one choices accessible.
- The second request inquires about any excellent funds which can be owed to the seller. The e mail states that the seller has misplaced monitor of open invoices on their finish as a result of their accounting workforce is unable to overview accounts. In one e mail, Firebrick Ostrich offered extra particulars, stating that the account workforce is “not able to get onto the server or into Oracle to review accounts or post payments that may have been received.”
“The manufactured pretext of a technical issue is a common excuse used in many of the third-party reconnaissance attacks we see to explain why a vendor isn’t able to access their own inventory of invoices, but the flattery shown here seems to be unique to this BEC group,” stated Hassold.
Another tactic is especially stealthy as a result of it doesn’t request cost for a present bill, however merely asks {that a} vendor’s saved checking account particulars be up to date so any future funds get redirected to the brand new account. This sidesteps pink flags that accounts payable specialists might have been educated to note, based on Abnormal Security. The longer recreation is that the menace actors will receives a commission with the following bill, as an alternative of the particular vendor.
What makes this group pretty distinctive is that they’ve seen huge success even with out the necessity to compromise accounts or do in-depth analysis on the vendor-customer relationship. By utilizing pretty apparent social engineering ways, they will uncover every thing they want so as to run a profitable BEC marketing campaign — with out investing any important time or assets into the preliminary analysis, per Abnormal Security.
The finest protection is holistic screening
Hassold stated that email-flagging applied sciences that determine static indicators received’t be enough to defend in opposition to BEC assaults; he advisable a extra holistic protection utilizing such strategies as behavioral evaluation to grasp the connection between the sender and recipients. This holistic technique would additionally incorporate details about the goal firm’s third-party vendor ecosystem and monitor each for particular impersonation assaults spoofing these distributors and suspicious language and artifacts.
“Understanding what trends are being seen in the overall cyberthreat landscape and making sure employees are aware of these are critical,” he stated. “That means when they see a Firebrick Ostrich-type attack with requests for an account change or messages about technical difficulties, there’s already an internal policy in place to validate those requests offline with the vendor well before changes are actually made. We think of cyberattacks as very sophisticated things, but at the end of the day a vast majority are nothing more than social engineering, trying to manipulate human behavior — getting someone to do something they wouldn’t otherwise do.”
With cybersecurity assaults prone to rise this 12 months, and menace actors changing into extra subtle of their strategies, this additionally may be a great time to placed on the white hat. Learn the ropes for $30 with these 9 moral hacking programs provided by means of TechRepublic Academy.
