[ad_1]

Security researchers with Horizon3’s Attack Team will launch an exploit focusing on a vulnerability chain subsequent week for gaining distant code execution on unpatched VMware vRealize Log Insight home equipment.
Now often known as VMware Aria Operations for Logs, vRealize Log Insight makes it simpler for VMware admins to research and handle terabytes of infrastructure and utility logs.
On Tuesday, VMware patched 4 safety vulnerabilities on this log evaluation software, two of that are vital and permit attackers to execute code remotely with out authentication.
Both are tagged as vital severity with CVSS base scores of 9.8/10 and may be exploited by risk actors in low-complexity assaults that do not require authentication.
One of them (CVE-2022-31706) is a listing traversal vulnerability that may be abused to inject information into the working system of impacted home equipment, and the second (tracked as CVE-2022-31704) is a damaged entry management flaw that can be exploited by injecting maliciously crafted information in RCE assaults.
VMware additionally addressed a deserialization vulnerability (CVE-2022-31710) that triggers denial of service states and an info disclosure bug (CVE-2022-31711) exploitable to entry delicate session and utility data.
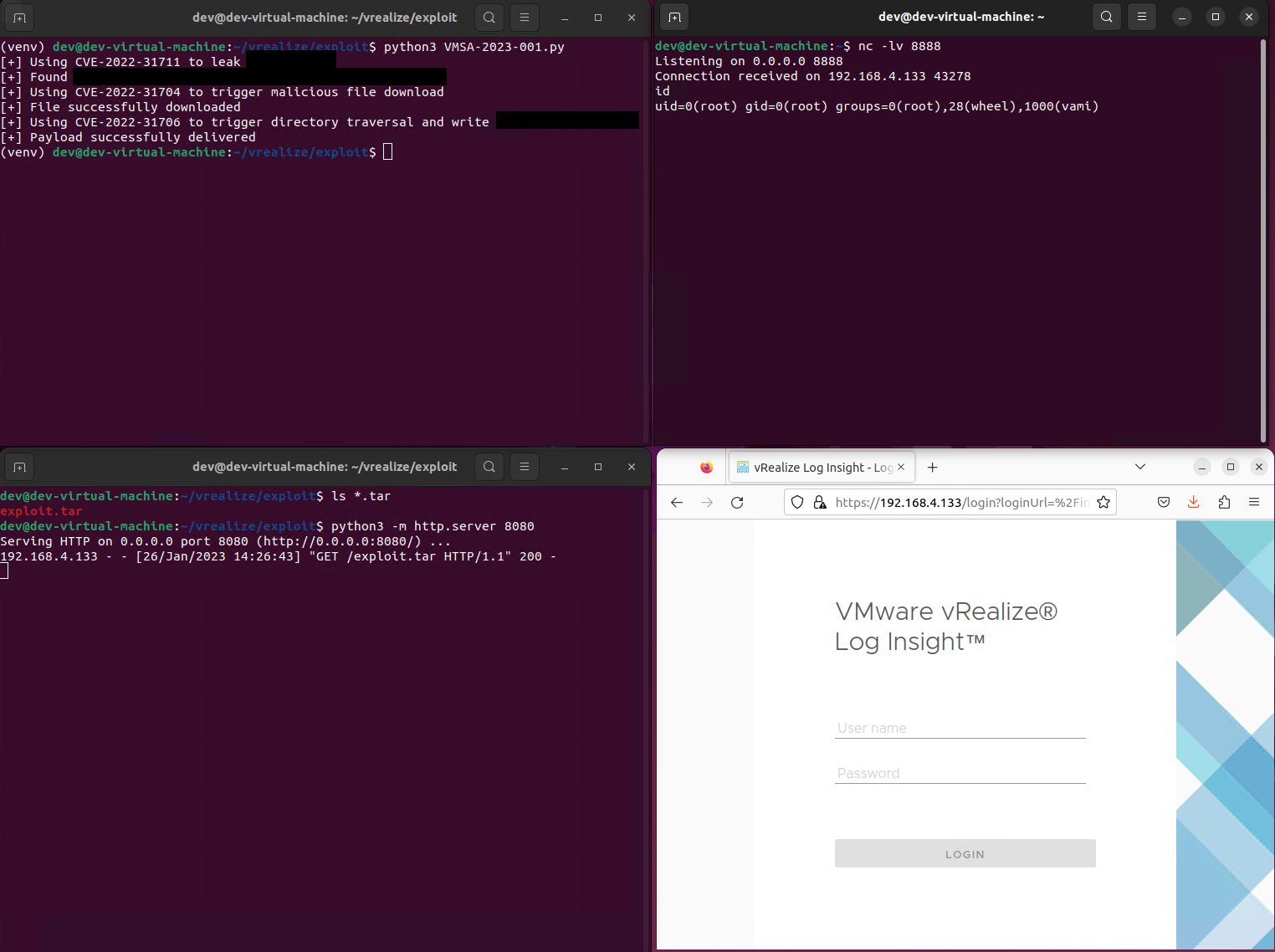
On Thursday, Horizon3’s Attack Team warned VMware admins that they have been capable of create an exploit that chains three of the 4 flaws patched by VMware this week to execute code remotely as root.
All vulnerabilities are exploitable within the default configuration of VMware vRealize Log Insight home equipment. The exploit can be utilized to realize preliminary entry to organizations’ networks (by way of Internet-exposed home equipment) and for lateral motion with saved credentials.
One day later, the safety researchers printed a weblog submit containing further info, together with a listing of indicators of compromise (IOCs) that defenders might use to detect indicators of exploitation inside their networks.
Attackers can acquire delicate info from logs on Log Insight hosts, together with API keys and session tokens that can assist breach further programs and additional compromise the surroundings.
”This vulnerability is simple to take advantage of nonetheless, it requires the attacker to have some infrastructure setup to serve malicious payloads,” the researchers stated.
“Additionally, since this product is unlikely to be uncovered to the web, the attacker doubtless has already established a foothold elsewhere on the community.
“This vulnerability permits for distant code execution as root, basically giving an attacker full management over the system.”
As Horizon3 vulnerability researcher James Horseman additional revealed, there are solely 45 situations publicly uncovered on the web, in keeping with Shodan information.
This is to be anticipated since VMware vRealize Log Insight home equipment are designed to be accessed inside a company’s community.
However, it isn’t unusual for risk actors to abuse vulnerabilities in already breached networks to unfold laterally to different gadgets, making these worthwhile inner targets.
In May 2022, Horizon3 launched one other exploit for CVE-2022-22972, a vital authentication bypass vulnerability affecting a number of VMware merchandise and permitting risk actors to realize admin privileges.