[ad_1]
Cybersecurity researchers have uncovered a PlugX pattern that employs sneaky strategies to contaminate hooked up detachable USB media gadgets as a way to propagate the malware to further techniques.
“This PlugX variant is wormable and infects USB gadgets in such a approach that it conceals itself from the Windows working file system,” Palo Alto Networks Unit 42 researchers Mike Harbison and Jen Miller-Osborn stated. “A consumer wouldn’t know their USB system is contaminated or presumably used to exfiltrate information out of their networks.”
The cybersecurity firm stated it uncovered the artifact throughout an incident response effort following a Black Basta ransomware assault towards an unnamed sufferer. Among different instruments found within the compromised surroundings embrace the Gootkit malware loader and the Brute Ratel C4 crimson group framework.
The use of Brute Ratel by the Black Basta group was beforehand highlighted by Trend Micro in October 2022, with the software program delivered as a second-stage payload by the use of a Qakbot phishing marketing campaign. The assault chain has since been used towards a big, regional power outfit based mostly within the southeastern U.S., in accordance with Quadrant Security.
However, there is no such thing as a proof that ties PlugX, a backdoor extensively shared throughout a number of Chinese nation-state teams, or Gootkit to the Black Basta ransomware gang, suggesting that it might have been deployed by different actors.
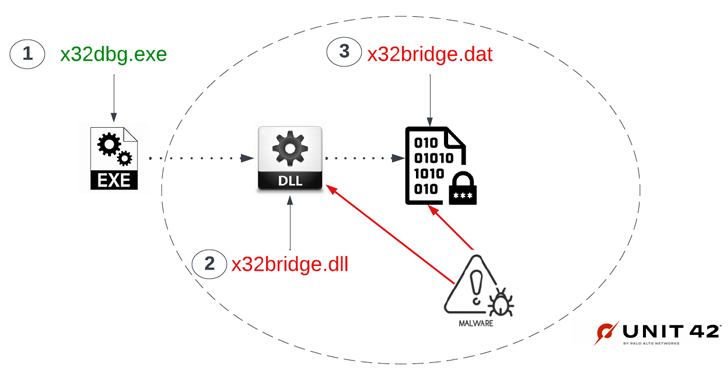
The USB variant of PlugX is notable for the truth that it makes use of a selected Unicode character referred to as non-breaking area (U+00A0) to cover recordsdata in a USB system plugged right into a workstation.
“The whitespace character prevents the Windows working system from rendering the listing identify, concealing it reasonably than leaving a anonymous folder in Explorer,” the researchers stated, explaining the novel approach.
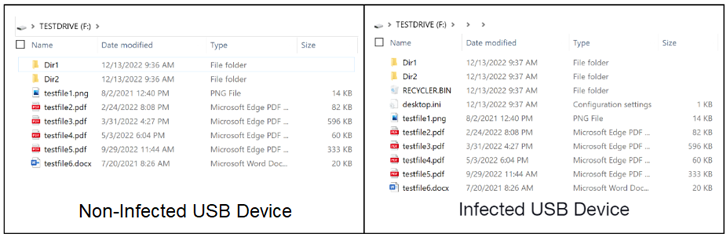
Ultimately, a Windows shortcut (.LNK) file created within the root folder of the flash drive is used to execute the malware from the hidden listing. The PlugX pattern will not be solely tasked with implanting the malware on the host, but additionally copying it on any detachable system which may be related to it by camouflaging it inside a recycle bin folder.
The shortcut file, for its half, carries the identical identify as that of the USB system and seems as a drive icon, with the prevailing recordsdata or directories on the basis of the detachable system moved to a hidden folder created contained in the “shortcut” folder.
“Whenever the shortcut file from the contaminated USB system is clicked, the PlugX malware launches Windows Explorer and passes the listing path as a parameter,” Unit 42 stated. “This then shows the recordsdata on the USB system from inside the hidden directories and in addition infects the host with the PlugX malware.”
The approach banks on the truth that Windows File Explorer (beforehand Windows Explorer) by default doesn’t present hidden objects. But the intelligent twist right here is that the malicious recordsdata inside the so-called recycle bin don’t get displayed when with the setting enabled.
This successfully signifies that the rogue recordsdata can solely be seen on a Unix-like working system like Ubuntu or by mounting the USB system in a forensic instrument.
“Once a USB system is found and contaminated, any new recordsdata written to the USB system root folder post-infection are moved to the hidden folder inside the USB system,” the researchers stated. “Since the Windows shortcut file resembles that of a USB system and the malware shows the sufferer’s recordsdata, they unwittingly proceed to unfold the PlugX malware.”
Unit 42 stated it additionally found a second variant of PlugX that, along with infecting USB gadgets, additional copies all Adobe PDF and Microsoft Word recordsdata from the host to a different hidden folder on the USB system created by the malware.
The use of USB drives as a method to exfiltrate particular recordsdata of curiosity from its targets signifies an try on a part of the menace actors to leap over air-gapped networks.
With the newest improvement, PlugX joins the ranks of different malware households resembling ANDROMEDA and Raspberry Robin which have added the potential to unfold through contaminated USB drives.
“The discovery of those samples signifies PlugX improvement continues to be alive and nicely amongst a minimum of some technically expert attackers, and it stays an lively menace,” the researchers concluded.