[ad_1]
Microsoft is a major goal for risk actors, who scour Microsoft functions for weaknesses. Our safety analysis workforce at Adaptive Shield lately found a brand new assault vector attributable to a vulnerability inside Microsoft’s OAuth utility registration that enables attackers to leverage Exchange’s legacy API to create hidden forwarding guidelines in Microsoft 365 mailboxes.
To perceive this new assault vector, you have to perceive the important thing elements therein. These embrace hidden forwarding guidelines and SaaS-to-SaaS app entry, all of which quantity to a malicious SaaS rootkit that may infiltrate customers’ accounts and management their mailboxes — with out the customers’ information.
Learn extra concerning the prime use circumstances to safe your total SaaS stack.
Hidden Forwarding Rules
Inbox guidelines are actions that happen primarily based on preset circumstances inside a Microsoft mailbox. Users or admins can use forwarding guidelines to set off protocols primarily based on totally different attributes of the person’s inbox.
Hidden forwarding guidelines (Figure 1) had been first found by Compass Security’s Damian Pflammater in 2018. He lined the invention and Microsoft’s response in a weblog submit titled “Hidden Inbox Rules in Microsoft Exchange.” These guidelines are totally purposeful and could be seen on the again finish. However, they don’t seem to be seen frequent interfaces reminiscent of e mail purchasers, an admin dashboard, or an API (Figure 2).
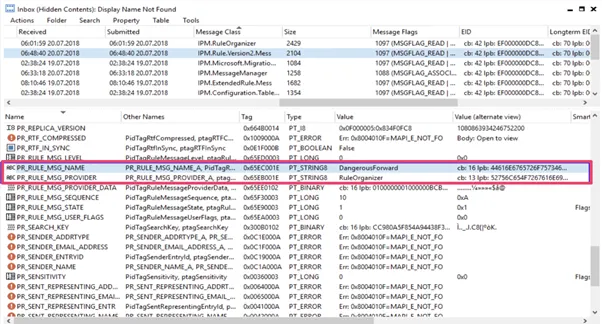
SaaS-to-SaaS Access Through OAuth 2.0
SaaS-to-SaaS app entry, additionally known as third-party app entry, describes the circumstances underneath which one app can join to a different app and, in doing so, achieve entry and permission to totally different data and settings. The OAuth 2.0 mechanism simplifies the method of authentication and authorization between shoppers and repair suppliers by a seamless course of that enables customers to shortly confirm their identities and grant permissions to the app. The app is then allowed to execute code and carry out logic inside its surroundings behind the scenes.
In many situations, these apps are utterly innocent and sometimes function a helpful enterprise device. In different situations, these apps can act as malware, much like an executable file.
The Next Evolution: An Attack Method Through SaaS
With this SaaS rootkit, risk actors can create malware that lives as a SaaS app and might infiltrate and preserve entry to a person’s account whereas going unnoticed.
While dangerous actors cannot discover Exchange Legacy scopes that may used so as to add programmatically on-line hidden forwarding within the Microsoft UI, they will add them by a terminal script.
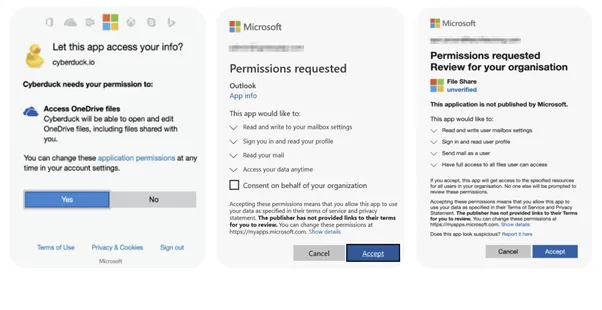
The attacker’s job is easy: Create an app that appears credible, add the legacy scope protocols faraway from the UI to the app (exploiting the vulnerability that the Adaptive Shield workforce uncovered), and ship a suggestion to customers to connect with it. The person will see an OAuth app dialogue field on the official Microsoft website, and plenty of will probably settle for it (Figure 4).

Once a person accepts, the dangerous actor receives a token that grants permission to create forwarding guidelines and hides them from the person interface like a rootkit.
An assault by these hidden forwarding guidelines shouldn’t be mistaken for a one-off assault however, moderately, the beginning of a brand new assault methodology by SaaS apps.
Microsoft Response
In 2022, Adaptive Shield contacted Microsoft concerning the concern, Microsoft in response mentioned that the problem has been flagged for future assessment by the product workforce as a chance to enhance the safety of the affected product.
How to Best Mitigate a SaaS Rootkit Attack
There’s no bulletproof solution to get rid of SaaS rootkit assaults however there are just a few greatest practices that may assist preserve organizations extra protected.
- Monitor third-party app entry and their permissions to make sure that apps are authentic and given solely the entry they require.
- Track actions and be looking out for brand new inbox guidelines to determine any new connections from untrusted domains.
- Disable third-party app registrations the place attainable to scale back danger.
Conclusion
Hidden forwarding guidelines are nonetheless a risk, much more so after they seem by the trusted Microsoft web site. The conventional controls that had been created to cease malware have struggled to maintain up with the evolution of malware and the brand new assault vector that may exploit any SaaS app, from M365 to Salesforce to G-Workspace, and many others. Organizations ought to make the most of native safety configurations to regulate the OAuth utility installations throughout SaaS apps to guard customers from malicious assaults like these.
Get Forrester’s SSPM Report, “Embrace aParadigm Shift In SaaS Protection: SaaS Security Posture Management.”
About the Author

A former cybersecurity intelligence officer within the IDF, Maor Bin has over 16 years in cybersecurity management. In his profession, he led SaaS Threat Detection Research at Proofpoint and gained the operational excellence award throughout his IDI service. Maor obtained his B.Sc. in laptop science and is CEO and co-founder of Adaptive Shield.
