[ad_1]
Unidentified menace actors have deployed a brand new backdoor that borrows its options from the U.S. Central Intelligence Agency (CIA)’s Hive multi-platform malware suite, the supply code of which was launched by WikiLeaks in November 2017.
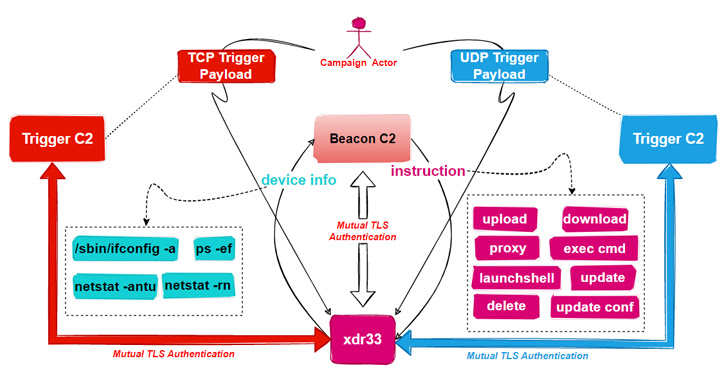
“This is the primary time we caught a variant of the CIA Hive assault equipment within the wild, and we named it xdr33 based mostly on its embedded Bot-side certificates CN=xdr33,” Qihoo Netlab 360’s Alex Turing and Hui Wang stated in a technical write-up printed final week.
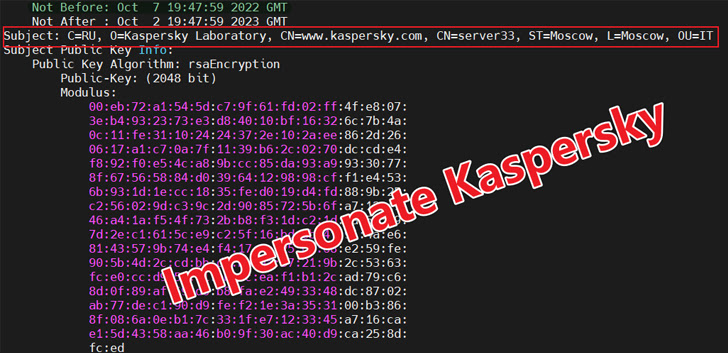
xdr33 is alleged to be propagated by exploiting an unspecified N-day safety vulnerability in F5 home equipment. It communicates with a command-and-control (C2) server utilizing SSL with solid Kaspersky certificates.
The intent of the backdoor, per the Chinese cybersecurity agency, is to reap delicate data and act as a launchpad for subsequent intrusions. It improves upon Hive by including new C2 directions and functionalities, amongst different implementation adjustments.
The ELF pattern additional operates as a Beacon by periodically exfiltrating system metadata to the distant server and executing instructions issued by the C2.
This contains the flexibility to obtain and add arbitrary information, run instructions utilizing cmd, and launch shell, along with updating and erasing traces of itself from the compromised host.
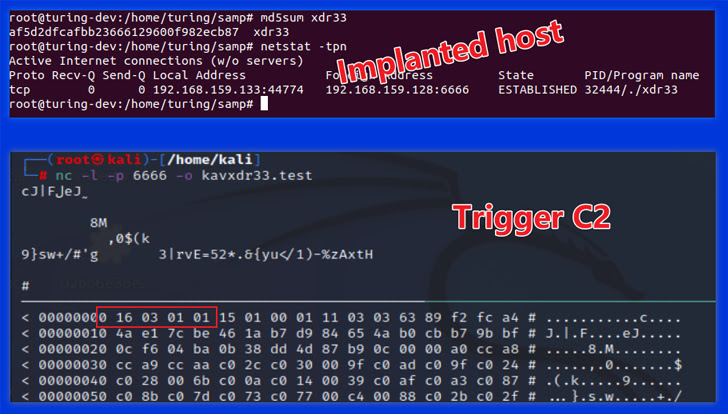
The malware additionally incorporates a Trigger module that is designed to snoop on community site visitors for a selected “set off” packet with a view to extract the C2 server talked about within the IP packet’s payload, set up connection, and await the execution of instructions despatched by the C2.
“It is value noting that Trigger C2 differs from Beacon C2 within the particulars of communication; after establishing an SSL tunnel, [the] bot and Trigger C2 use a Diffie-Helllman key change to ascertain a shared key, which is used within the AES algorithm to create a second layer of encryption,” the researchers defined.