[ad_1]
Threat actors related to the Roaming Mantis assault marketing campaign have been noticed delivering an up to date variant of their patent cell malware referred to as Wroba to infiltrate Wi-Fi routers and undertake Domain Name System (DNS) hijacking.
Kaspersky, which carried out an evaluation of the malicious artifact, stated the function is designed to focus on particular Wi-Fi routers positioned in South Korea.
Roaming Mantis, often known as Shaoye, is a long-running financially motivated operation that targets Android smartphone customers with malware able to stealing checking account credentials in addition to harvesting different kinds of delicate info.
Although primarily concentrating on the Asian area since 2018, the hacking crew was detected increasing its sufferer vary to incorporate France and Germany for the primary time in early 2022 by camouflaging the malware because the Google Chrome net browser utility.
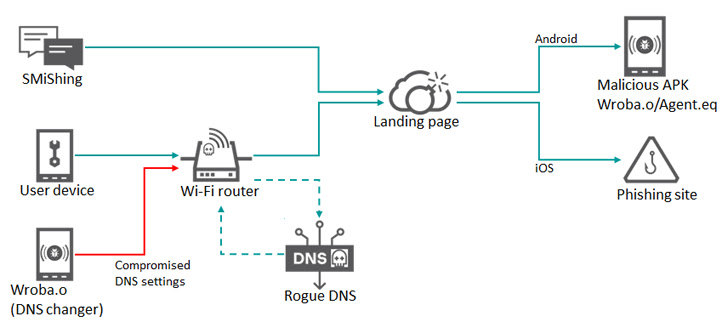
The assaults leverage smishing messages because the preliminary intrusion vector of option to ship a booby-trapped URL that both provides a malicious APK or redirects the sufferer to phishing pages based mostly on the working system put in within the cell gadgets.
Alternatively, some compromises have additionally leveraged Wi-Fi routers as a way to take unsuspecting customers to a faux touchdown web page through the use of a way referred to as DNS hijacking, through which DNS queries are manipulated to be able to redirect targets to bogus websites.
Regardless of the strategy used, the intrusions pave the best way for the deployment of a malware dubbed Wroba (aka MoqHao and XLoader) that is able to finishing up a slew of nefarious actions.
The newest replace to Wroba, per the Russian cybersecurity firm, includes a DNS changer perform that is engineered to detect sure routers based mostly on their mannequin numbers and poison their DNS settings.
“The new DNS changer performance can handle all machine communications utilizing the compromised Wi-Fi router, reminiscent of redirecting to malicious hosts and disabling updates of safety merchandise,” Kaspersky researcher Suguru Ishimaru stated.
The underlying concept is to trigger gadgets linked to the breached Wi-Fi router to be redirected to net pages managed by the risk actor for additional exploitation. Given that a few of these pages ship the Wroba malware, the assault chain successfully creates a gentle stream of “bots” that may be weaponized to interrupt into wholesome Wi-Fi routers.
It’s notable that the DNS changer program is completely utilized in South Korea. However, the Wroba malware in itself has been noticed concentrating on victims in Austria, France, Germany, India, Japan, Malaysia, Taiwan, Turkey, and the U.S. through smishing.
“Users with contaminated Android gadgets that connect with free or public Wi-Fi networks might unfold the malware to different gadgets on the community if the Wi-Fi community they’re linked to is susceptible,” the researcher stated.