[ad_1]
New analysis has discovered that it’s doable for risk actors to abuse a professional function in GitHub Codespaces to ship malware to sufferer programs.
GitHub Codespaces is a cloud-based configurable growth surroundings that permits customers to debug, keep, and commit adjustments to a given codebase from an internet browser or by way of an integration in Visual Studio Code.
It additionally comes with a port forwarding function that makes it doable to entry an internet software that is operating on a selected port inside the codespace straight from the browser on a neighborhood machine for testing and debugging functions.
“You also can ahead a port manually, label forwarded ports, share forwarded ports with members of your group, share forwarded ports publicly, and add forwarded ports to the codespace configuration,” GitHub explains in its documentation.
It’s essential to notice right here that any forwarded port that is made public will even allow any occasion with data of the URL and port quantity to view the operating software sans any authentication.
GitHub Codespaces makes use of HTTP for port forwarding. Should the publicly seen port be up to date to make use of HTTPS or eliminated and re-added, the port’s visibility is robotically modified to personal.
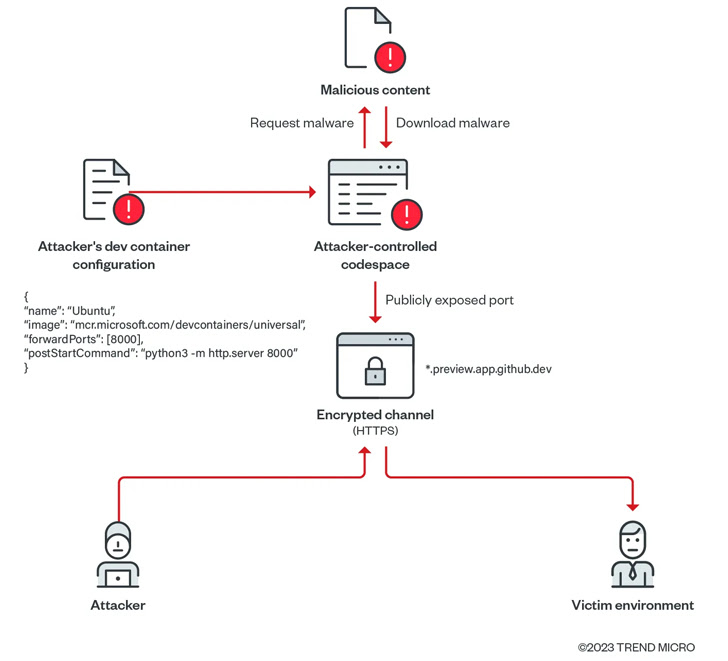
Cybersecurity agency Trend Micro discovered that such publicly-shared forwarded ports might be exploited to create a malicious file server utilizing a GitHub account.
“In the method, these abused environments is not going to be flagged as malicious or suspicious even because it serves malicious content material (resembling scripts, malware, and ransomware, amongst others), and organizations could take into account these occasions as benign or false positives,” researchers Nitesh Surana and Magno Logan mentioned.
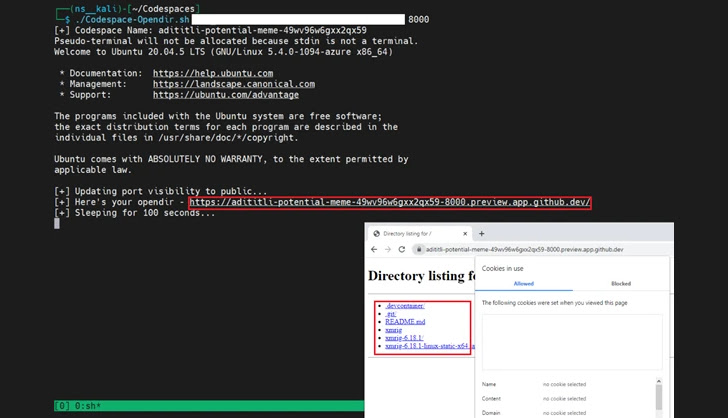
In a proof-of-concept (PoC) exploit demonstrated by Trend Micro, a risk actor may create a codespace and obtain malware from an attacker-controlled area to the surroundings, and set the visibility of the forwarded port to public, primarily remodeling the appliance to behave as an internet server internet hosting rogue payloads.
Even extra troublingly, the adversary can increase this methodology to deploy malware and compromise a sufferer’s surroundings since every codespace area related to the uncovered port is exclusive and unlikely to be flagged by safety instruments as a malicious area.
“Using such scripts, attackers can simply abuse GitHub Codespaces in serving malicious content material at a fast fee by exposing ports publicly on their codespace environments,” the researchers defined.
While the approach is but to be noticed within the wild, the findings are a reminder as to how risk actors may weaponize cloud platforms to their profit and perform an array of illicit actions.
“Cloud providers provide benefits to professional customers and attackers alike,” the researchers concluded. “The options provided to professional subscribers additionally change into out there to risk actors as they reap the benefits of the sources offered by the [cloud service provider].”