[ad_1]
The infamous information-stealer generally known as Vidar is continuous to leverage common social media providers akin to TikTok, Telegram, Steam, and Mastodon as an intermediate command-and-control (C2) server.
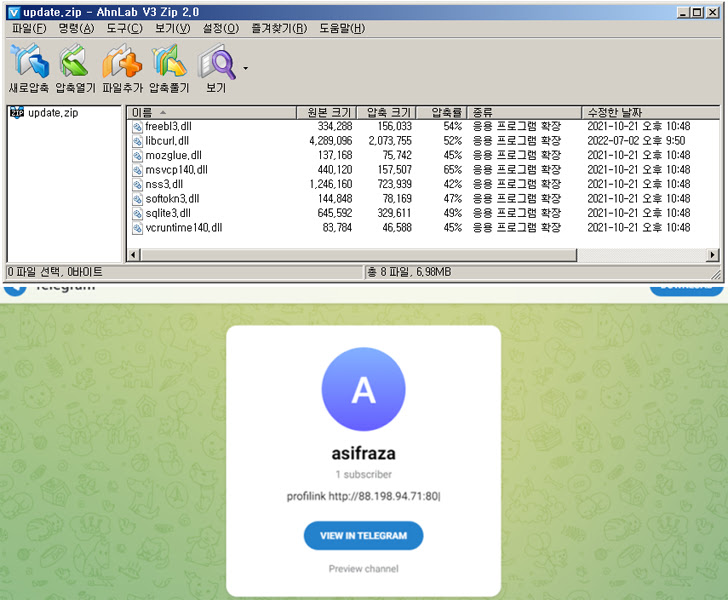
“When a consumer creates an account on a web based platform, a novel account web page that may be accessed by anybody is generated,” AhnLab Security Emergency Response Center (ASEC) disclosed in a technical evaluation printed late final month. “Threat actors write figuring out characters and the C2 handle in elements of this web page.”
In different phrases, the method depends on actor-controlled throwaway accounts created on social media to retrieve the C2 handle.
An benefit to this strategy is that ought to the C2 server be taken down or blocked, the adversary can trivially get across the restrictions by organising a brand new server and enhancing the account pages to permit the beforehand distributed malware to speak with the server.
Vidar, first recognized in 2018, is a industrial off-the-shelf malware that is able to harvesting a variety of knowledge from compromised hosts. It sometimes depends on supply mechanisms like phishing emails and cracked software program for propagation.
“After info assortment is full, the extorted info is compressed right into a ZIP file, encoded in Base64, and transmitted to the C2 server,” ASEC researchers stated.
What’s new within the newest model of the malware (model 56.1) is that the gathered knowledge is encoded previous to exfiltration, a change from the earlier variants which have been recognized to ship the compressed file knowledge in plaintext format.
“As Vidar makes use of well-known platforms because the middleman C2, it has a protracted lifespan,” the researchers stated. “A menace actor’s account created six months in the past remains to be being maintained and constantly up to date.”
The improvement comes amid latest findings that the malware is being distributed utilizing a wide range of strategies, together with malicious Google Ads and a malware loader dubbed Bumblebee, the latter of which is attributed to a menace actor tracked as Exotic Lily and Projector Libra.
Risk consulting agency Kroll, in an evaluation printed final month, stated it found an advert for the GIMP open supply picture editor that, when clicked from the Google search consequence, redirected the sufferer to a typosquatted area internet hosting the Vidar malware.
If something, the evolution of malware supply strategies within the menace panorama is partly a response to Microsoft’s determination to dam macros by default in Office information downloaded from the web since July 2022.
This has led to a rise within the abuse of various file codecs like ISO, VHD, SVG, and XLL in e mail attachments to bypass Mark of the Web (MotW) protections and evade anti-malware scanning measures.
“Disk picture information can bypass the MotW function as a result of when the information inside them are extracted or mounted, MotW shouldn’t be inherited to the information,” ASEC researchers stated, detailing a Qakbot marketing campaign that leverages a mixture of HTML smuggling and VHD file to launch the malware.
[ad_2]