[ad_1]
A variant of the notorious Dridex banking malware has set its sights on Apple’s macOS working system utilizing a beforehand undocumented an infection methodology, in accordance with newest analysis.
It has “adopted a brand new method to ship paperwork embedded with malicious macros to customers with out having to faux to be invoices or different business-related information,” Trend Micro researcher Armando Nathaniel Pedragoza stated in a technical report.
Dridex, additionally known as Bugat and Cridex, is an info stealer that is recognized to reap delicate information from contaminated machines and ship and execute malicious modules. It’s attributed to an e-crime group often known as Evil Corp (aka Indrik Spider).
The malware can be thought-about to be a successor of Gameover Zeus, itself a follow-up to a different banking trojan known as Zeus. Previous Dridex campaigns focusing on Windows have leveraged macro-enabled Microsoft Excel paperwork despatched through phishing emails to deploy the payload.
Trend Micro’s evaluation of the Dridex samples entails a Mach-O executable file, the earliest of which was submitted to VirusTotal in April 2019. Since then, 67 extra artifacts have been detected within the wild, some as latest as December 2022.
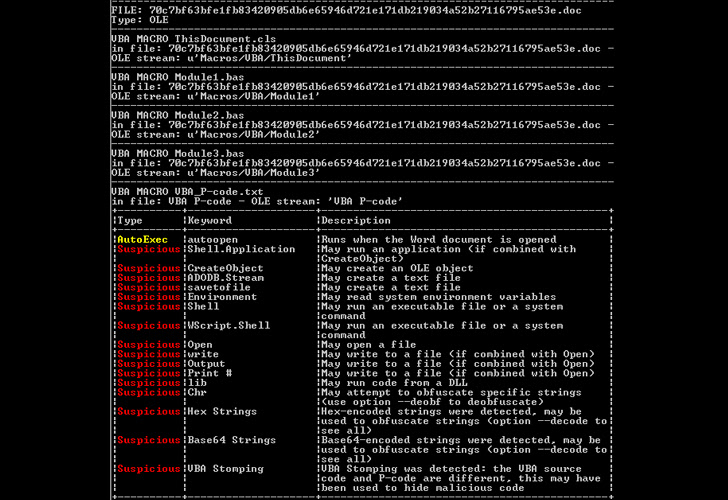
The artifact, for its half, comprises a malicious embedded doc – first detected method again in 2015 – that comes with an Auto-Open macro that is routinely run upon opening a Word doc.
Furthermore, the Mach-O executable is designed to go looking and overwrite all “.doc” information within the present person listing (~/User/{person identify}) with the malicious macro code copied from the embedded doc within the type of a hexadecimal dump.
“While the macro characteristic in Microsoft Word is disabled by default, the malware will overwrite all of the doc information for the present person, together with the clear information,” Pedragoza defined. “This makes it harder for the person to find out whether or not the file is malicious because it would not come from an exterior supply.”
The macros included within the overwritten doc are engineered to contact a distant server to retrieve further information, which features a Windows executable file that won’t run in macOS, indicating that the assault chain may be a piece in progress. The binary, in flip, makes an attempt to obtain the Dridex loader onto the compromised machine.
While paperwork containing booby-trapped macros are usually delivered through social engineering assaults, the findings as soon as once more present that Microsoft’s resolution to dam macros by default has prompted risk actors to refine their techniques and discover extra environment friendly strategies of entry.
“Currently, the impression on macOS customers for this Dridex variant is minimized because the payload is an .EXE file (and due to this fact not suitable with macOS environments),” Trend Micro stated. “However, it nonetheless overwrites doc information which at the moment are the carriers of Dridex’s malicious macros.”