[ad_1]
A South Africa-based risk actor often known as Automated Libra has been noticed using CAPTCHA bypass methods to create GitHub accounts in a programmatic style as a part of a freejacking marketing campaign dubbed PURPLEURCHIN.
The group “primarily targets cloud platforms providing limited-time trials of cloud sources in an effort to carry out their crypto mining operations,” Palo Alto Networks Unit 42 researchers William Gamazo and Nathaniel Quist mentioned.
PURPLEURCHIN first got here to mild in October 2022 when Sysdig disclosed that the adversary created as many as 30 GitHub accounts, 2,000 Heroku accounts, and 900 Buddy accounts to scale its operation.
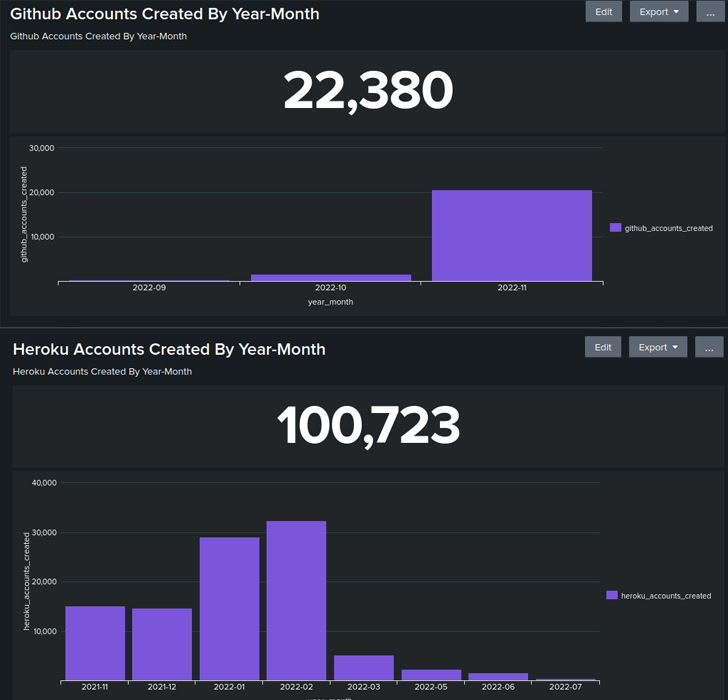
Now in accordance with Unit 42, the cloud risk actor group created three to 5 GitHub accounts each minute on the peak of its exercise in November 2022, completely organising over 130,000 bogus accounts throughout Heroku, Togglebox, and GitHub.
More than 22,000 GitHub accounts are estimated to have been created between September and November 2022, three in September, 1,652 in October, and 20,725 in November. A complete of 100,723 distinctive Heroku accounts have additionally been recognized.
The cybersecurity firm additionally termed the abuse of cloud sources as a “play and run” tactic designed to keep away from paying the platform vendor’s invoice by making use of falsified or stolen bank cards to create premium accounts.
Its evaluation of 250GB of information places the earliest signal of the crypto marketing campaign not less than almost 3.5 years in the past in August 2019, figuring out using greater than 40 wallets and 7 completely different cryptocurrencies.
The core concept that undergirds PURPLEURCHIN is the exploitation of computational sources allotted to free and premium accounts on cloud providers in an effort to reap financial earnings on an enormous scale earlier than shedding entry for non-payment of dues.
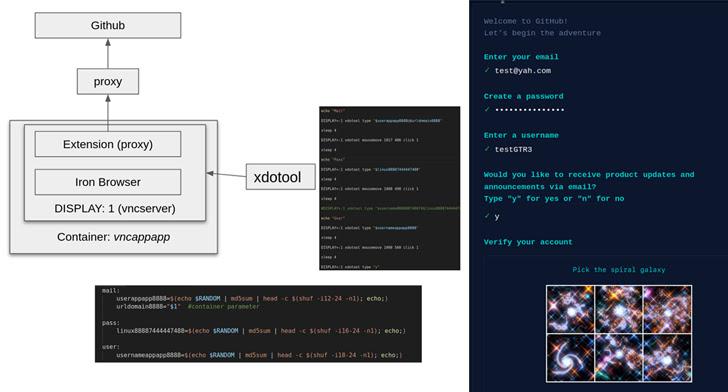
Besides automating the account creation course of by leveraging reliable instruments like xdotool and ImageMagick, the risk actor has additionally been discovered to reap the benefits of weak spot inside the CAPTCHA verify on GitHub to additional its illicit goals.
This is achieved by utilizing ImageMagick’s convert command to remodel the CAPTCHA photos to their RGB enhances, adopted by utilizing the determine command to extract the skewness of the purple channel and deciding on the smallest worth.
Once the account creation is profitable, Automated Libra proceeds to create a GitHub repository and deploys workflows that make it potential to launch exterior Bash scripts and containers for initiating the crypto mining capabilities.
The findings illustrate how the freejacking marketing campaign might be weaponized to maximise returns by rising the variety of accounts that may be created per minute on these platforms.
“It is essential to notice that Automated Libra designs their infrastructure to take advantage of use out of CD/CI instruments,” the researchers concluded.
“This is getting simpler to attain over time, as the standard VSPs are diversifying their service portfolios to incorporate cloud-related providers. The availability of those cloud-related providers makes it simpler for risk actors, as a result of they do not have to keep up infrastructure to deploy their functions.”
[ad_2]