[ad_1]
Financial and insurance coverage sectors in Europe have been focused by the Raspberry Robin worm, because the malware continues to evolve its post-exploitation capabilities whereas remaining below the radar.
“What is exclusive in regards to the malware is that it’s closely obfuscated and extremely advanced to statically disassemble,” Security Joes mentioned in a brand new report revealed Monday.
The intrusions, noticed towards Spanish and Portuguese-speaking organizations, are notable for amassing extra sufferer machine knowledge than beforehand documented, with the malware now exhibiting refined methods to withstand evaluation.
Raspberry Robin, additionally referred to as QNAP worm, is getting used by a number of risk actors as a method to achieve a foothold into goal networks. Spread through contaminated USB drives and different strategies, the framework has been not too long ago put to make use of in assaults geared toward telecom and authorities sectors.
Microsoft is monitoring the operators of Raspberry Robin below the moniker DEV-0856.
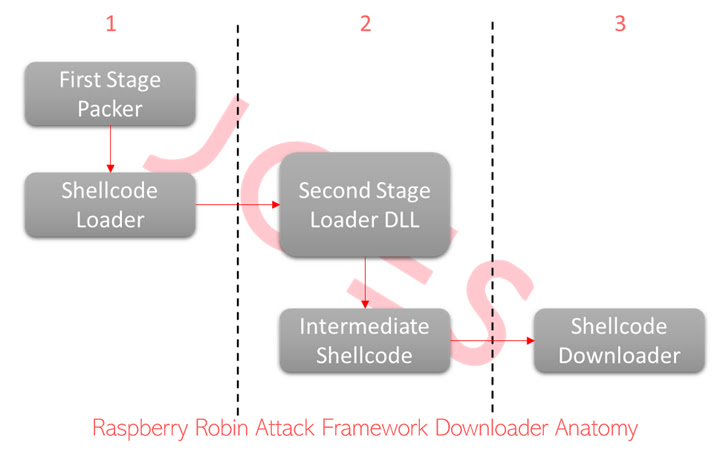
Security Joes’ forensic investigation into one such assault has revealed the usage of a 7-Zip file, which is downloaded from the sufferer’s browser through social engineering and accommodates an MSI installer file designed to drop a number of modules.
In one other occasion, a ZIP file is claimed to have been downloaded by the sufferer by way of a fraudulent advert hosted on a site that is identified to distribute adware.
The archive file, saved in a Discord server, accommodates encoded JavaScript code that, upon execution, drops a downloader that is protected with quite a few layers of obfuscation and encryption to evade detection.
The shellcode downloader is primarily engineered to fetch extra executables, nevertheless it has additionally seen vital upgrades that permits it to profile its victims to ship acceptable payloads, in some circumstances even resorting to a type of trickery by serving faux malware.
This includes amassing the host’s Universally Unique Identifier (UUID), processor identify, hooked up show gadgets, and the variety of minutes which have elapsed since system startup, together with the hostname and username data that was gathered by older variations of the malware.
The reconnaissance knowledge is then encrypted utilizing a hard-coded key and transmitted to a command-and-control (C2) server, which responds again with a Windows binary that is then executed on the machine.
“Not solely did we uncover a model of the malware that’s a number of instances extra advanced, however we additionally discovered that the C2 beaconing, which used to have a URL with a plaintext username and hostname, now has a sturdy RC4 encrypted payload,” risk researcher Felipe Duarte mentioned.
[ad_2]