[ad_1]
The Computer Emergency Response Team of Ukraine (CERT-UA) this week disclosed that customers of the Delta situational consciousness program acquired phishing emails from a compromised electronic mail account belonging to the Ministry of Defense.
The assaults, which have been attributed to a risk cluster dubbed UAC-0142, aimed to contaminate methods with two items of data-stealing malware known as FateGrab and StealDeal.
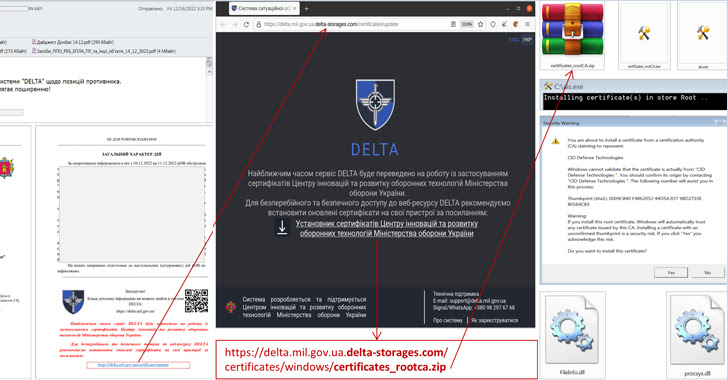
Delta is a cloud-based operational state of affairs show system developed by Aerorozvidka that permits real-time monitoring of troops on the battlefield, making it a profitable goal for risk actors.
The lure messages, which include pretend warnings to replace root certificates within the Delta software program, carry PDF paperwork containing hyperlinks to archive information hosted on a fraudulent Delta area, in the end dropping the malware on compromised methods.
While FateGrab is principally designed to exfiltrate information with particular extensions by means of File Transfer Protocol (FTP), StealDeal singles out net browsers to siphon passwords and different info.
The assault comes days after Ukraine offered the Delta system to the NATO Consultation, Command, and Control Organization (NC3O). It additionally follows revelations that the Russia-linked Gamaredon group tried to unsuccessfully infiltrate a big petroleum refining firm inside a NATO member state in late August 2022.
The Russo-Ukrainian conflict has prompted Moscow to accentuate cyberattacks in opposition to Ukraine, counting on a wide selection of wiper malware to disrupt essential infrastructure.
Ukrainian organizations, in latest months, have additionally been focused with RomCom RAT and Vidar stealer, the latter of which has been discovered to behave as a conduit to drop a ransomware pressure referred to as Somnia.
Earlier this month, CERT-UA famous that state-owned organizations have been focused with phishing emails purporting to be from the State Emergency Service of Ukraine and containing weaponzied RAR archives which are engineered to deploy a Delphi-based backdoor named DolphinCape.