[ad_1]
The Vice Society ransomware actors have switched to one more {custom} ransomware payload of their latest assaults geared toward a wide range of sectors.
“This ransomware variant, dubbed ‘PolyVice,’ implements a sturdy encryption scheme, utilizing NTRUEncrypt and ChaCha20-Poly1305 algorithms,” SentinelOne researcher Antonio Cocomazzi stated in an evaluation.
Vice Society, which is tracked by Microsoft underneath the moniker DEV-0832, is an intrusion, exfiltration, and extortion hacking group that first appeared on the menace panorama in May 2021.
Unlike different ransomware gangs, the cybercrime actor doesn’t use file-encrypting malware developed in-house. Instead, it is identified to deploy third-party lockers reminiscent of Hello Kitty, Zeppelin, and RedAlert ransomware of their assaults.
Per SentinelOne, indications are that the menace actor behind the custom-branded ransomware can be promoting related payloads to different hacking crews primarily based on PolyVice’s in depth similarities to ransomware strains Chily and SunnyDay.
This implies a “Locker-as-a-Service” that is provided by an unknown menace actor within the type of a builder that enables its consumers to customise their payloads, together with the encrypted file extension, ransom notice file title, ransom notice content material, and the wallpaper textual content, amongst others.
The shift from Zeppelin is prone to have been spurred by the discovery of weaknesses in its encryption algorithm that enabled researchers at cybersecurity firm Unit221b to plan a decryptor in February 2020.
Besides implementing a hybrid encryption scheme that mixes uneven and symmetric encryption to securely encrypt information, PolyVice additionally makes use of partial encryption and multi-threading to hurry up the method.
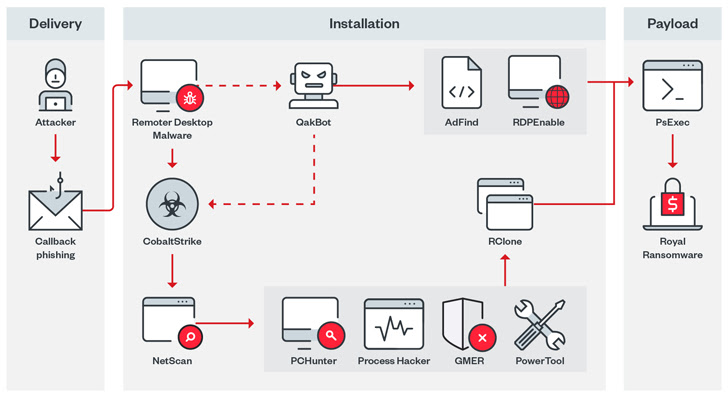
It’s price mentioning that the just lately found Royal ransomware employs related techniques in a bid to evade anti-malware defenses, Cybereason disclosed final week.
Royal, which has its roots within the now-defunct Conti ransomware operation, has additionally been noticed to make the most of name again phishing (or telephone-oriented assault supply) to trick victims into putting in distant desktop software program for preliminary entry.
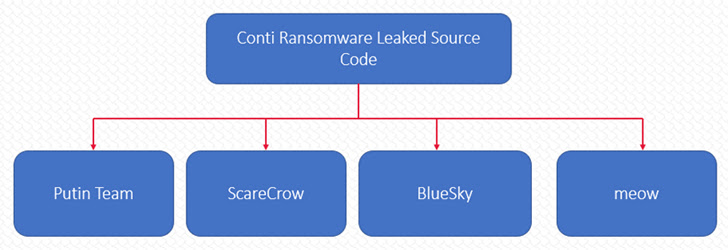
In the in the meantime, the leak of Conti supply code earlier this yr has spawned quite a few new ransomware strains reminiscent of Putin Team, ScareCrow, BlueSky, and Meow, Cyble disclosed, highlighting how such leaks are making it simpler for menace actors to launch completely different offshoots with minimal funding.
“The ransomware ecosystem is consistently evolving, with the pattern of hyperspecialization and outsourcing repeatedly rising,” Cocomazzi stated, including it “presents a major menace to organizations because it allows the proliferation of refined ransomware assaults.”