[ad_1]

Microsoft Office recordsdata, significantly Excel and Word recordsdata, have been focused by some cybercriminals for a very long time. Through completely different methods, attackers have used embedded Visual Basic for Applications macros to contaminate computer systems with completely different sorts of malware for cybercrime and cyberespionage.
In most circumstances, customers nonetheless wanted to click on their settlement when executing code inside these purposes, however some social engineering methods have enticed unsuspecting victims to click on and permit the execution of the malicious macros themselves. Direct exploitation of vulnerabilities with none consumer interplay can also be doable to launch malware.
SEE: Mobile system safety coverage (TechRepublic Premium)
Jump to:
.XLL malicious exploitation within the wild
As uncovered in new analysis from Cisco Talos, menace actors would possibly leverage occasion dealing with capabilities in Excel recordsdata with a purpose to routinely launch .XLL recordsdata. The most typical technique to attain that is to execute the malicious code when the Excel Add-In supervisor calls the xlAutoOpen or xlAutoClose capabilities.
Cisco Talos researchers have leveraged particular queries in VirusTotal to seek out malicious .XLL recordsdata and supply YARA guidelines to hunt for such recordsdata. They separated native .XLL samples constructed with the same old Microsoft .XLL SDK and samples generated utilizing the ExcelDNA framework, as it’s free and tends to be the one most utilized by menace actors (Figure A).
Figure A

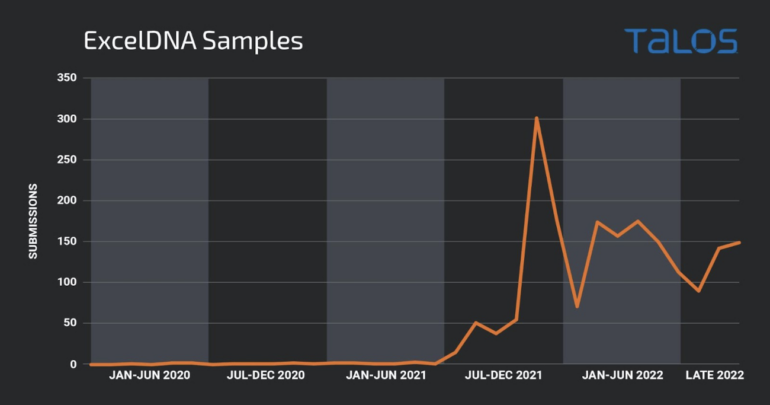
The charts above reveal that menace actors have been exploiting .XLL file vulnerabilities lengthy earlier than Microsoft began blocking paperwork containing VBA macros.
The Cisco Talos researchers established that no probably malicious samples have been submitted till July 2017. The first .XLL payload discovered on the VirusTotal platform launched calc.exe, which is a common testing technique for penetration testers and cybercriminals. The second pattern, submitted in the identical month, launched a Meterpreter reverse shell, which can be used for penetration testing or malicious intent.
After that exercise, .XLL recordsdata appeared sporadically, however it didn’t enhance till the top of 2021 when notorious malware households comparable to Dridex and FormBook started utilizing it.
Which menace actors exploit .XLL recordsdata?
Several menace actors are actually utilizing .XLL recordsdata to contaminate computer systems.
APT10, often known as Red Apollo, menuPass, Stone Panda or Potassium, is a cyberespionage menace actor that has been working since 2006 and is related to the Chinese Ministry of State Security, in keeping with the Department of Justice.
A file leveraging .XLL to inject a malware unique to APT10 dubbed Anel was present in December 2017 by the researchers.
TA410 is one other menace actor who targets U.S. utilities and diplomatic organizations and is loosely linked to APT10. They make use of a toolkit that additionally contains an .XLL stage found in 2020.
The DoNot staff concentrating on Kashmiri nonprofit organizations and Pakistani authorities officers additionally appeared to make use of this technique: An .XLL file containing two exports, the primary one referred to as pdteong and the second xlAutoOpen, make it a totally useful .XLL payload. The pdteong export title has been used solely by the DoNot staff.
FIN7 is a cybercrime menace actor working from Russia. In 2022, the menace actor began utilizing .XLL recordsdata despatched as attachment recordsdata in malicious electronic mail campaigns. When these recordsdata are executed, they act as downloaders for the following an infection stage.
The main spike within the .XLL detections in VirusTotal, nevertheless, comes primarily from Dridex malware campaigns. These .XLL recordsdata are used as downloaders for the following an infection stage, which is chosen from a big listing of doable payloads accessible through the Discord software program utility.
The second most typical payload is FormBook, an data stealer out there as a service for an inexpensive value on-line. It makes use of electronic mail campaigns to unfold the .XLL downloader, which fetches the following an infection stage — the FormBook malware itself.
A current AgentTesla and Lokibot marketing campaign concentrating on Hungary exploited .XLL recordsdata through electronic mail. The electronic mail pretended to come back from Hungarian police departments (Figure B).
Figure B
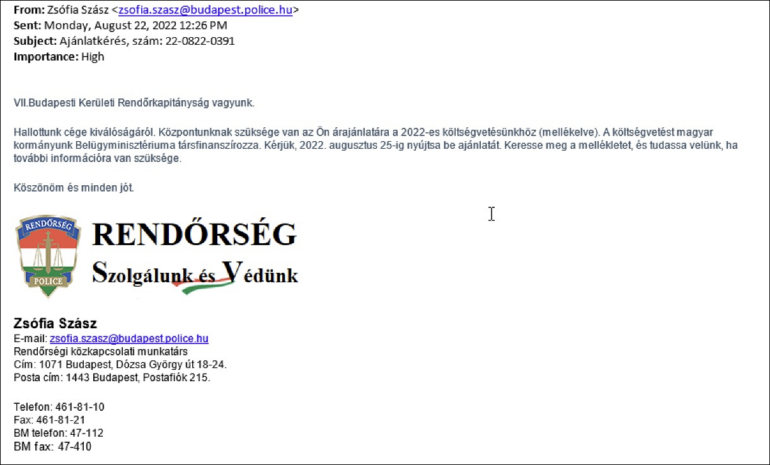
The textual content has been translated by Cisco Talos:
“We are the VII Budapest District Police Department.
We have heard in regards to the excellence of your organization. Our middle wants your quote for our 2022 funds (hooked up). The funds is co-financed by the Ministry of the Interior of our Hungarian authorities. Please submit your provide by Aug. 25, 2022. Please discover the attachment and tell us in the event you want extra data.”
In addition, the Ducktail malware, an data stealer malware run by a Vietnam-operating menace actor, makes use of .XLL. The menace actor used a file named “Details of Project Marketing Plan and Facebook Google Ads Results Report.xll” to contaminate its targets with the Ducktail malware.
Default Microsoft Office conduct modifications for the great
To assist combat infections through using VBA macros, Microsoft determined to vary the default conduct of its Office merchandise to dam macros in recordsdata downloaded from the web.
Office Add-Ins are items of executable code that may be added to Office purposes to enhance functionalities or improve the appliance’s look. Office Add-Ins would possibly include VBA code or modules embedding compiled functionalities in .NET bytecode. This may very well be within the type of COM servers or a Dynamic Link Library renamed with a selected file extension.
Add-Ins for the Microsoft Word utility must be in a location specified by a registry worth, relying on the Office model. A file put in that folder with a file extension .WLL will probably be loaded into the Word course of house.
For Microsoft Excel, any file with the .XLL extension that’s clicked by the consumer will routinely try and run Excel because the opener for the .XLL file. In any case, the Excel software program will set off a show message about potential malware or safety issues, however that is ineffective with basic customers, who are likely to disregard such warnings.
.XLL add-ins are usually developed within the C/C++ programming language utilizing the Microsoft Excel .XLL Software Development Kit, however some frameworks comparable to Add-In Express and Excel-DNA enable using .NET languages like C# or VB.NET.
How to guard towards the .XLL safety menace
The use of .XLL recordsdata is just not widespread in company environments; companies that don’t want it ought to block any try and execute .XLL recordsdata of their atmosphere. If your organization does enable using .XLL recordsdata, cautious monitoring have to be run at endpoints and servers with a purpose to detect any suspicious exercise and examine it.
Email gateways shouldn’t settle for .XLL recordsdata by default, and lift consciousness for company customers. If they see a warning message from Excel about operating Add-Ins and have no idea why it occurs, they need to not enable the execution and name their IT/safety division.
This safety consciousness and coaching coverage and IT electronic mail safety alert templates from TechRepublic Premium are nice assets to assist forestall a cybersecurity catastrophe from hanging.
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
