[ad_1]
The risk actors behind the Windows banking malware often known as Casbaneiro has been attributed as behind a novel Android trojan known as BrasDex that has been noticed concentrating on Brazilian customers as a part of an ongoing multi-platform marketing campaign.
BrasDex incorporates a “advanced keylogging system designed to abuse Accessibility Services to extract credentials particularly from a set of Brazilian focused apps, in addition to a extremely succesful Automated Transfer System (ATS) engine,” ThreatFabric stated in a report revealed final week.
The Dutch safety agency stated that the command-and-control (C2) infrastructure used together with BrasDex can be getting used to regulate Casbaneiro, which is understood to strike banks and cryptocurrency providers in Brazil and Mexico.
The hybrid Android and Windows malware marketing campaign is estimated to have resulted in hundreds of infections to this point.
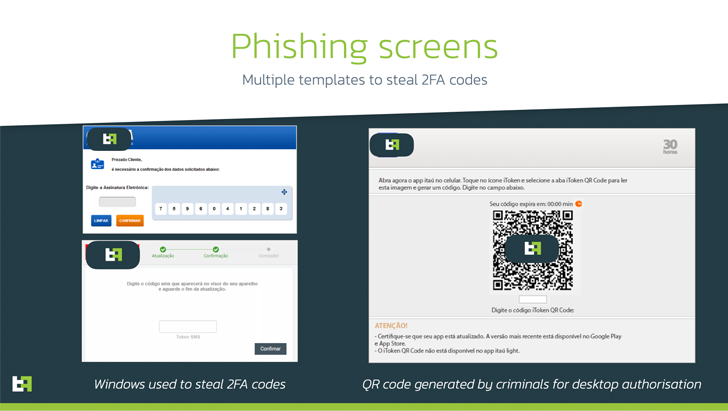
BrasDex, which masquerades as a banking app for Banco Santander, can be emblematic of a brand new pattern that includes abusing Android’s Accessibility APIs to log keystrokes entered by the victims, shifting away from the normal methodology of overlay assaults to steal credentials and different private knowledge.
It’s additionally engineered to seize account steadiness data, subsequently utilizing it to take over contaminated units and provoke fraudulent transactions in a programmatic method.
Another notable facet of BrasDex is its singular concentrate on the PIX funds platform, which permits banking prospects in Brazil to become profitable transfers merely utilizing their e-mail addresses or cellphone numbers.
The ATS system in BrasDex is explicitly designed to abuse PIX expertise to make fraudulent transfers.
This isn’t the primary time the moment fee ecosystem has been focused by dangerous actors. In September 2021, Check Point detailed two Android malware households named PixStealer and MalRhino that tricked customers into transferring their whole account balances to an actor-controlled one.
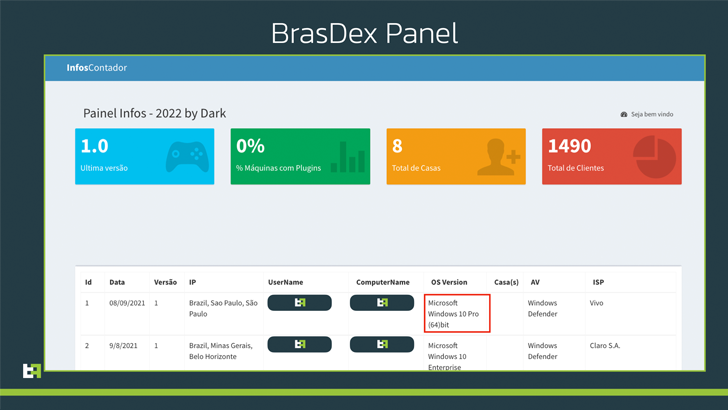
ThreatFabric’s investigation into BrasDex additionally allowed it to achieve entry to the C2 panel utilized by the felony operators to maintain monitor of the contaminated units and retrieve knowledge logs exfiltrated from the Android telephones.
The C2 panel, because it occurs, can be being utilized to maintain tabs on a unique malware marketing campaign which compromises Windows machines to deploy Casbaneiro, a Delphi-based monetary trojan.
This assault chain employs package deal delivery-themed phishing lures purporting to be from Correios, a state-owned postal service, to dupe recipients into executing the malware following a multi-staged course of.
Casbaneiro’s options run the standard backdoor gamut that enables it to grab management of banking accounts, take screenshots, carry out keylogging, hijack clipboard knowledge, and even operate as a clipper malware to hijack crypto transactions.
“Being impartial and full-fledged malware households, BrasDex and Casbaneiro type a really harmful pair, permitting the actor behind them to focus on each Android and Windows customers on a big scale,” ThreatFabric stated.
“The BrasDex case exhibits the need of fraud detection and prevention mechanisms in place on prospects units: Fraudulent funds made routinely with the assistance of ATS engines seem reliable to financial institution backends and fraud scoring engines, as they’re made by way of the identical system that’s normally utilized by prospects.”