[ad_1]
TA435 is now using extra aggressive techniques, together with the usage of actual e mail accounts, malware and confrontational lures to realize entry to key accounts. The risk actor targets high-profile and high-security accounts for cyberespionage functions.
Jump to:
Who is TA453?
TA453 is a state-sponsored Iranian cyberespionage risk actor. TA453 has been identified for nearly all the time concentrating on teachers, researchers, diplomats, dissidents, journalists and human proper staff, all with experience within the Middle-East, in accordance with Proofpoint.
TA453 overlaps with cyberespionage teams Charming Kitten, Phosphorus and APT42.
Their favourite methodology to method and assault their targets consists of utilizing net beacons in emails earlier than finally making an attempt to reap the goal’s credentials. They additionally leverage multi-persona impersonation, which is a social engineering trick utilizing two impersonated accounts managed by the attackers to speak in a single e mail thread with the sufferer. The a number of personas try and persuade the goal of the legitimacy of the operation.
Proofpoint presently tracks six subgroups of TA453, that are categorised by victimology, infrastructure and techniques, methods and procedures.
The researchers assess that TA453 usually operates for the Iranian Islamic Revolutionary Guard Corps, Intelligence Operation, as based mostly on analysis from PwC and the Justice Department in a 2018 indictment along with an evaluation of TA453 concentrating on in comparison with reported IRGC-IO actions.
“The more aggressive activity could represent collaboration with another branch of the Iranian state, including the IRGC Quds Force,” Proofpoint mentioned.
A shift in TA453’s strategies
Email accounts used to achieve the targets
The use of e mail accounts created by the attacker is usually dropped by risk actors in favor of utilizing actual compromised accounts. This has the impact of constructing their content material look extra professional, because it comes from a identified e mail handle relatively than an unknown one.
SEE: Password breach: Why popular culture and passwords don’t combine (free PDF) (TechRepublic)
This methodology is utilized by a subgroup of the TA453 risk actor and mixed with the usage of uncommon URL shorteners like bnt2[.]stay or nco2[.]stay. Proofpoint signifies that in 2021, a U.S. press secretary was reached by TA453 utilizing the e-mail handle of an area reporter.
Use of malware
The GhostEcho malware, a light-weight PowerShell backdoor underneath growth that’s in a position to execute further modules and talk with an attacker-controlled C2 server, was used to focus on quite a lot of diplomatic missions throughout Tehran in 2021 to focus on ladies’s rights advocates within the nation. The payload was not out there to the researchers when found.
Confrontational lures
Samantha Wolf is a persona created by TA453 utilized in confrontational social engineering lures. The objective is to lift the goal’s worry and uncertainty in order that they reply to the emails despatched by the attackers.
Samantha Wolf used normal complaints and automobile accidents amongst different themes, concentrating on U.S. and European politicians and governmental entities (Figure A).
Figure A
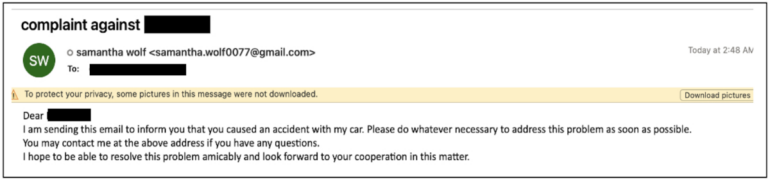
Documents despatched by Samantha Wolf contained distant template injection to obtain malicious recordsdata, leading to a GhostEcho an infection. The methodology utilized by the attackers consisted of changing the consumer’s earlier default Microsoft Word template.
Even extra aggressive exercise
In May 2022, Proofpoint found an assault concentrating on a high-ranking army official with a number of compromised e mail accounts. The focused particular person was a former member of the Israeli army. As talked about earlier, the usage of a number of compromised e mail accounts for such an assault is uncommon for TA453.
The aggressive message was written in Hebrew (Figure B) and used the primary title of the particular person within the filename.
Figure B

The textual content roughly interprets: “I’m sure you remember when I told you every email you get from your friends may be me and not the person it claims to be. We follow you like your shadow — in Tel Aviv, in [redacted university], in Dubai, in Bahrain. Take care of yourself.”
According to Proofpoint, this intimidation tactic additionally signifies a collaboration between TA453 and hostile Iranian state-aligned operations.
An overlap within the infrastructure linking this case and one other one additionally provides legitimacy to the analysis’s conclusion. In May 2022, an Israeli researcher acquired an e mail coming from a spoofed e mail handle of a reputed tutorial to ask the goal to a convention as a way to kidnap them.
TA453s outlier operations have proven a relentless state of evolution in its TTP, with attainable help for hostile and even kinetic operations.
TA435’s beforehand identified modus operandi
TA453 usually approaches its targets with e mail accounts they create and begins establishing contact with their targets by way of benign dialog, though a few of its subgroups could straight hit the goal with a credential harvesting hyperlink. No matter the size of the alternate, the objective is all the time to get entry to the e-mail of the goal by way of a phishing hyperlink.
SEE: Mobile machine safety coverage (TechRepublic Premium)
This approach means that the attacker’s major curiosity resides in studying the e-mail content material of the goal, relatively than attempting to contaminate their pc with malware to get entry to recordsdata and folders. This can also be stealthier, because it doesn’t usually elevate alarms from safety productions — the phishing pages hosted on the infrastructure are by no means extensively unfold and subsequently hardly reported.
How to guard your self from this risk
Users have to be cautious when opening e mail content material, even when it comes from a verified and trusted e mail handle, which is perhaps compromised.
The content material of the e-mail ought to elevate alarm for the reader: Watch out for kinds not beforehand utilized by the author, spelling errors, adjustments in language or diction, and different indications that the e-mail is faux. When doubtful, customers ought to confirm the legitimacy of the e-mail by reaching out to the sender by way of one other channel.
Users also needs to all the time double-check invites to conferences and attain out on to the organizers by way of their official web site. Users ought to by no means click on on any suspicious hyperlinks. Instead, report the hyperlink to the IT division or CERT/SOC groups for investigation, as it might be a phishing try.
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
