[ad_1]
As the SolarWinds and Log4j hacks present, vulnerabilities in open supply software program utilized in utility growth can open doorways for attackers with huge penalties. A brand new research appears to be like on the open supply neighborhood’s efforts to “credit-rate” the danger.

It was virtually precisely one yr in the past that specialists discovered the notorious Log4Shell error message vulnerability within the open supply Java library Apache Log4j 2. The weak spot was only one current instance of a backdoor in open supply software program for attackers to sneak malicious code onto developer and end-user techniques. Since then, there have been tens of thousands and thousands of makes an attempt to compromise the Log4jShell flaw.
SEE: Iranian state-aligned menace actor targets new victims in cyberespionage and kinetic campaigns (TechRepublic)
If specialists establish the software program provide as a key safety problem for 2023, the Log4j phenomenon — to not point out the much-better recognized SolarWinds incursion in 2019 — make clear how defending the method could possibly be troublesome: An enormous quantity of economic software program just isn’t written in-house. It is derived from the wild west of free and open supply software program packages like Log4j on GitHub and elsewhere.
Open supply software program dependencies have dependencies
Like a gardener making an attempt to seize only one ivy plant, an utility developer who imports code from the FOSS ecosystem usually will get greater than the code they bargained for as a result of these extramural packages from repositories like GitHub usually deliver alongside transitive dependencies. These are the secondary and tertiary relationships {that a} FOSS package deal has with different open supply code, constituting a “hidden” root-like system of software program of unknown provenance, invisible to builders, intrinsically untrusted and probably harmful.
SEE: Improper use of password managers leaves folks susceptible to identification theft (TechRepublic)
A brand new research titled “The State of Dependency Management” by Endor Lab’s Station 9 revealed that 95% of all vulnerabilities are present in these open supply code packages that aren’t chosen by builders however not directly pulled into tasks.
“By some measures, for every one dependency a developer brings into a software project, there are, on average, 77 to 78 transitive dependencies,” stated Varun Badhwar, co-founder and CEO of Endor Labs. “Additionally, 95% of vulnerabilities found are in those transitive dependencies, the things that came with the things you brought. We need to track all of this in our environment and understand which apps these packages are being used in.”
Henrik Plate, safety researcher at Endor Labs, famous that writing software program is now like placing collectively a BMW.
“You are taking diverse components from somewhere else and assembling them,” Plate stated.
Badhwar stated 80% to 90% of code in a typical fashionable utility is “code we don’t write, it’s code we borrow, and we really don’t know who we are borrowing it from. Attackers have figured this out; open source software is going to be foundational for the software supply chain security, so we need to better educate the market on the issues.”
He identified that the Software Bill of Materials framework, although designed to offer correct dependency data, not often does. It particularly doesn’t accomplish that for transitive dependencies, given their so-so accuracy at one dependency degree.
SEE: How Microsoft will publish data to adjust to govt order on software program invoice of supplies (TechRepublic)
Acknowledging the urgency of the FOSS safety challenge, Congress launched the Securing Open Source Software Act in September 2022. The invoice urged CISA to “publicly publish a framework, incorporating government, industry, and open source software community frameworks and best practices, for assessing the risk of open source software components.” No progress has been made on the invoice since its introduction.
Which open supply software program is crucial?
The Log4j investigators tried to get a deal with on whether or not there may be consensus on essentially the most crucial FOSS packages for enterprise software program. These are the packages which might be the most-used by essentially the most builders and downstream customers, have the broadest performance and the best potential publicity by means of dependencies.
To do that, they explored criticality scores from the 2 hottest neighborhood initiatives to establish crucial tasks: the Linux Foundation-supported “Census II of Free and Open Source Software — Application Libraries” and the Open Source Security Foundation’s Criticality Score venture.
“We wanted to know whether those approaches converge; thus, whether they agree on what is critical and what is not,” Plate stated.
There wasn’t a lot overlap within the Census II and OpenSSF Criticality Scores venture units. The research famous that quite a few Census II packages got here from the identical venture and that 264 Java-based packages in Census II’s group come from solely 169 distinct tasks (Figure A).
Figure A
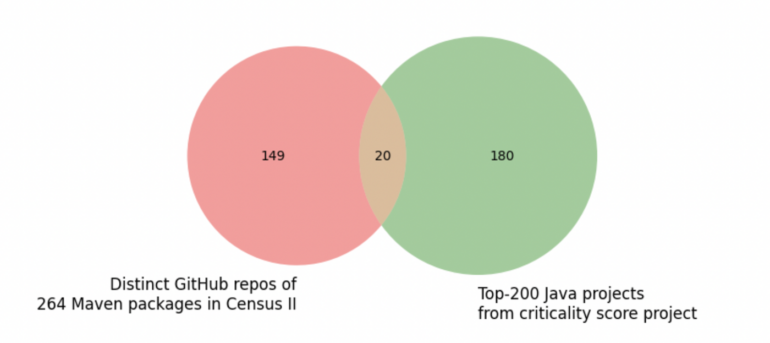
This wasn’t stunning to Professor Justin Cappos at NYU Tandon’s School of Engineering, a safety knowledgeable who has been working within the software program provide chain safety house for greater than a decade.
“We actually did our own analysis of which open source projects are critical and decided not to release the data, because we couldn’t come up with a solid enough metric to measure criticality,” Cappos stated. “It’s a hard problem.”
The Endor staff additionally discovered that:
- Half of essentially the most generally used open supply packages weren’t up to date this yr, and 30% had their final launch earlier than 2018.
- There is a 32% likelihood the most recent model of an open supply software program package deal has vulnerabilities.
- When upgrading to the most recent model of a package deal, there’s nonetheless a 32% likelihood it’s going to have recognized vulnerabilities.
- 75% of the packages in Census II have a Criticality Score of lower than 0.64 — that’s on a scale from zero to 1, with zero being least crucial.
- Using safety metrics alone when making prioritizations solely reduces the probability of a vulnerability by 20%.
Open supply: Caveat emptor
Badhwar famous that finally will probably be as much as organizations to take possession of the FOSS vetting course of, as a result of it’s their accountability to weed out the defective software program as soon as it has suffused itself into their infrastructure.
“It took something in the neighborhood of 33,000 hours for the DHS to figure out where Log4j had gone and then remediate it,” he stated. “Every organization and software vendor should track every component and dependence in their environment, and that starts with tracking to generate a software-level inventory of what developers are bringing from the internet.”
Plate stated criticality varies and that dedication can’t be outsourced.
“Every user has their own security requirements,” he stated. “Ultimately, the development organizations remain accountable for the commercial software services and products they sell, so those are other reasons this cannot just be outsourced to the open source community.”
[ad_2]
