[ad_1]
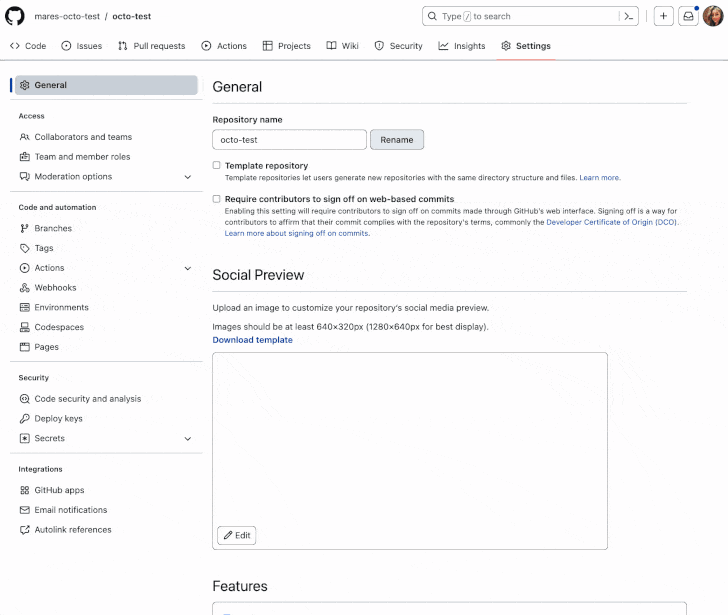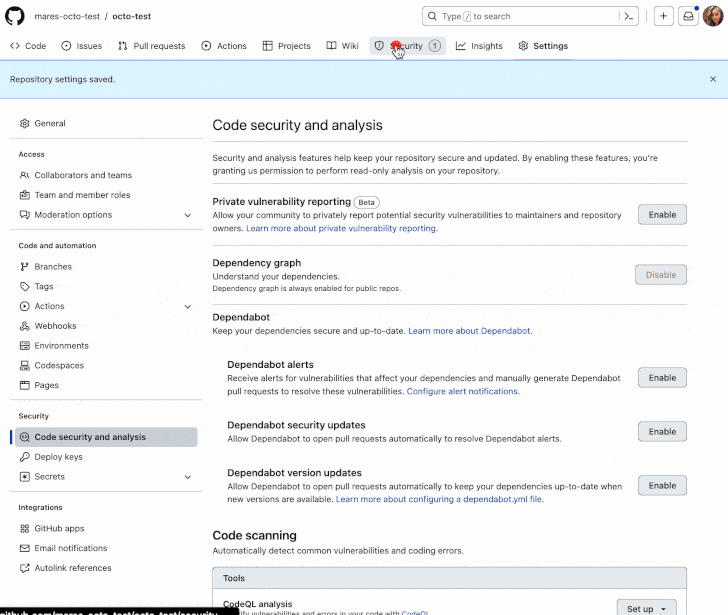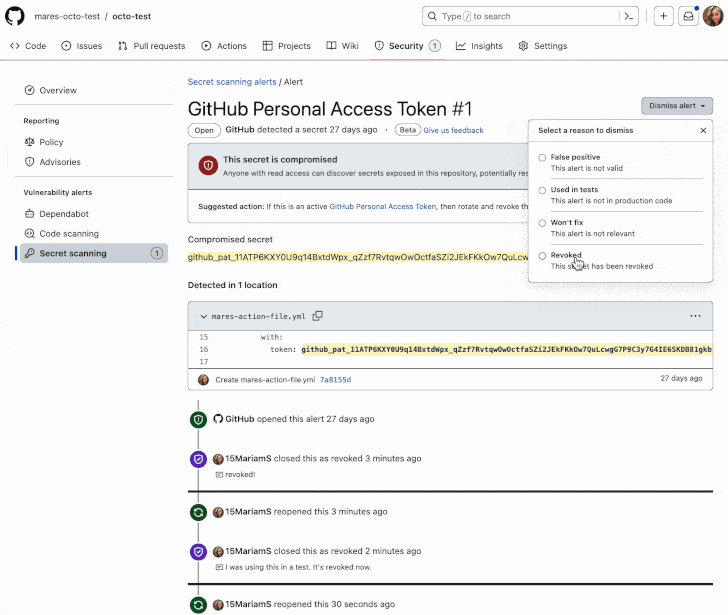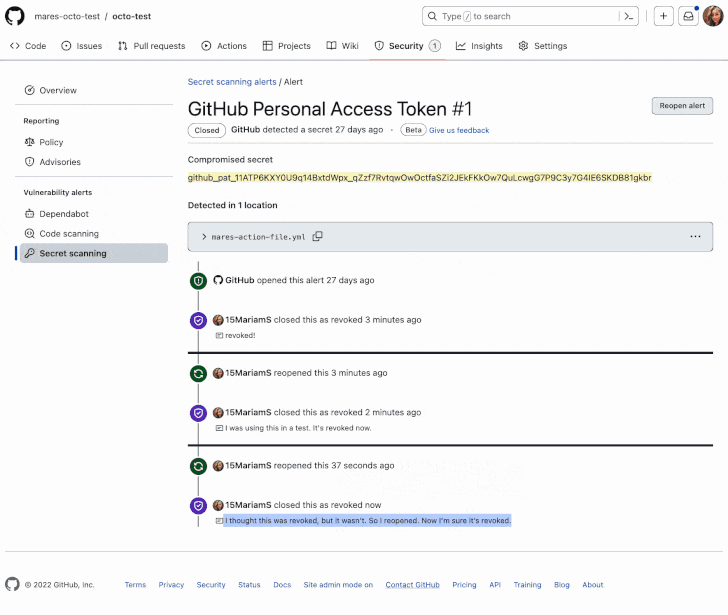
GitHub on Thursday mentioned it’s making accessible its secret scanning service to all public repositories on the code internet hosting platform without spending a dime.
“Secret scanning alerts notify you instantly about leaked secrets and techniques in your code,” the corporate mentioned, including it is anticipated to finish the rollout by the top of January 2023.
Secret scanning is designed to look at repositories for entry tokens, personal keys, credentials, API keys, and different secrets and techniques in over 200 codecs which will have been by accident dedicated, and generate alerts to stop their misuse.
The safety choice was beforehand restricted to repositories owned by organizations that use GitHub Enterprise Cloud and have a GitHub Advanced Security license.
For clients of GitHub Advanced Security, the protections go a step additional by performing the scans for uncovered secrets and techniques, together with customized patterns, throughout code pushes.
The Microsoft subsidiary additionally mentioned it is planning to activate two-factor authentication necessities for “distinct teams of customers” beginning March 2023 with the objective of increasing it to all GitHub customers by the top of subsequent yr.
The customers are more likely to comprise those that have revealed GitHub or OAuth apps, created a launch, contributed code to vital open supply repositories, and are Enterprise and Organization directors.
The firm additional acknowledged it is “exhausting at work” to combine passkey assist for stronger phishing-resistant authentication.