[ad_1]
An Internet Explorer zero-day vulnerability was actively exploited by a North Korean risk actor to focus on South Korean customers by capitalizing on the latest Itaewon Halloween crowd crush to trick customers into downloading malware.
The discovery, reported by Google Threat Analysis Group researchers Benoît Sevens and Clément Lecigne, is the most recent set of assaults perpetrated by ScarCruft, which can be known as APT37, InkySquid, Reaper, and Ricochet Chollima.
“The group has traditionally targeted their concentrating on on South Korean customers, North Korean defectors, coverage makers, journalists, and human rights activists,” TAG mentioned in a Thursday evaluation.
The new findings illustrate the risk actor’s continued abuse of Internet Explorer flaws similar to CVE-2020-1380 and CVE-2021-26411 to drop backdoors like BLUELIGHT and Dolphin, the latter of which was disclosed by Slovak cybersecurity agency ESET late final month.
Another key instrument in its arsenal is RokRat, a Windows-based distant entry trojan that comes with a variety of features that enable it to seize screenshots, log keystrokes, and even harvest Bluetooth machine info.
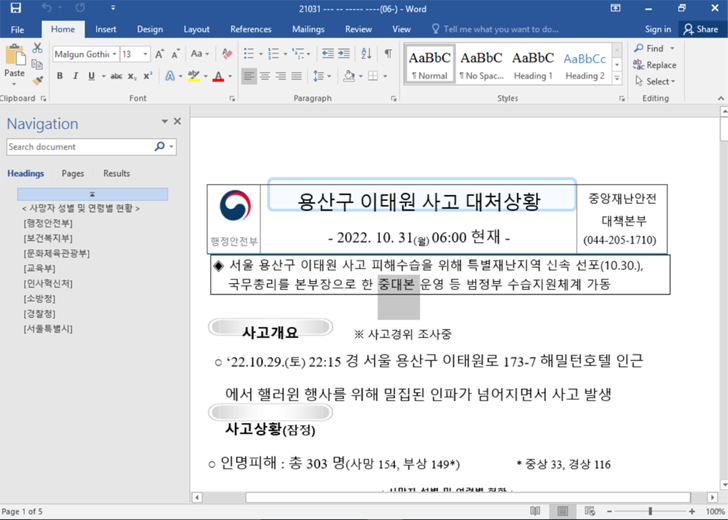
The assault chain noticed by Google TAG entails the usage of a malicious Microsoft Word doc that was uploaded to VirusTotal on October 31, 2022. It abuses yet one more Internet Explorer zero-day flaw within the JScript9 JavaScript engine, CVE-2022-41128, that was patched by Microsoft final month.
The file references the October 29 incident that came about within the Itaewon neighborhood of Seoul and exploits public curiosity within the tragedy to retrieve an exploit for the vulnerability upon opening it. The assault is enabled by the truth that Office renders HTML content material utilizing Internet Explorer.
As the MalwareHunterTeam factors out, the identical Word file was beforehand shared by the Shadow Chaser Group on October 31, 2022, describing it as an “attention-grabbing DOCX injection template pattern” that originated from Korea.
Successful exploitation is adopted by the supply of a shellcode that wipes all traces by clearing the Internet Explorer cache and historical past in addition to downloading the following stage payload.
Google TAG mentioned it couldn’t recuperate the follow-on malware used within the marketing campaign, though it is suspected to have concerned the deployment of RokRat, BLUELIGHT, or Dolphin.
“It isn’t a surprise that they proceed to focus on South Korean customers,” ESET malware analyst Filip Jurčacko informed The Hacker News. “We have not seen ScarCruft use zero-day exploits for a while. Previously, they have been repurposing public PoCs of n-day exploits.”
“Given the rarity/shortage of zero-day exploits, we anticipate ScarCruft would use it together with a few of their extra refined backdoors similar to Dolphin. Moreover, the workplace theme of [command-and-control] domains matches earlier campaigns.”