[ad_1]
A beforehand undocumented Go-based malware is concentrating on Redis servers with the purpose of taking management of the contaminated techniques and certain constructing a botnet community.
The assaults contain profiting from a important safety vulnerability within the open supply, in-memory, key-value retailer that was disclosed earlier this yr to deploy Redigo, based on cloud safety agency Aqua.
Tracked as CVE-2022-0543 (CVSS rating: 10.0), the weak spot pertains to a case of sandbox escape within the Lua scripting engine that could possibly be leveraged to realize distant code execution.
This shouldn’t be the primary time the flaw has come beneath energetic exploitation, what with Juniper Threat Labs uncovering assaults perpetrated by the Muhstik botnet in March 2022 to execute arbitrary instructions.
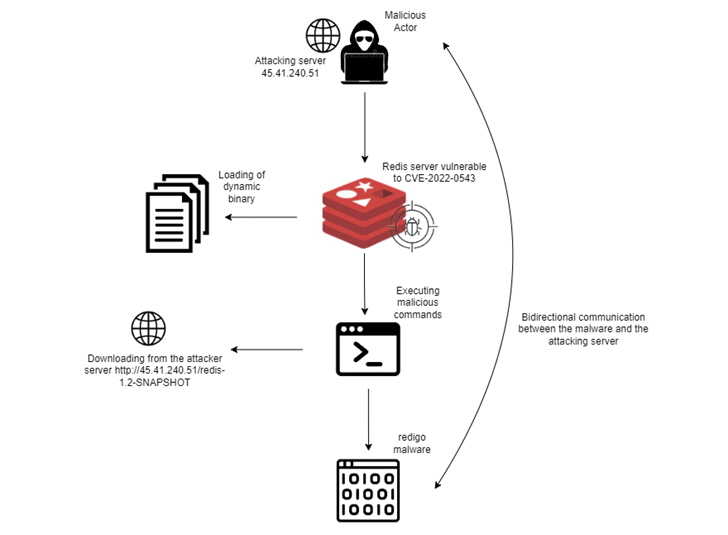
The Redigo an infection chain is comparable in that the adversaries scan for uncovered Redis servers on port 6379 to determine preliminary entry, following it up by downloading a shared library “exp_lin.so” from a distant server.
This library file comes with an exploit for CVE-2022-0543 to execute a command with a view to retrieve Redigo from the identical server, along with taking steps to masks its exercise by simulating professional Redis cluster communication over port 6379.
“The dropped malware mimics the Redis server communication which allowed the adversaries to cover communications between the focused host and the C2 server,” Aqua researcher Nitzan Yaakov defined.
It’s not recognized what the top purpose of the assaults are, however it’s suspected that the compromised hosts could possibly be co-opted right into a botnet to facilitate DDoS assaults or used to steal delicate info from the database server to additional lengthen their attain.
[ad_2]