[ad_1]
IBM has fastened a high-severity safety vulnerability affecting its Cloud Databases (ICD) for PostgreSQL product that might be doubtlessly exploited to tamper with inside repositories and run unauthorized code.
The privilege escalation flaw (CVSS rating: 8.8), dubbed “Hell’s Keychain” by cloud safety agency Wiz, has been described as a “first-of-its-kind supply-chain assault vector impacting a cloud supplier’s infrastructure.”
Successful exploitation of the bug may allow a malicious actor to remotely execute code in prospects’ environments and even learn or modify information saved within the PostgreSQL database.
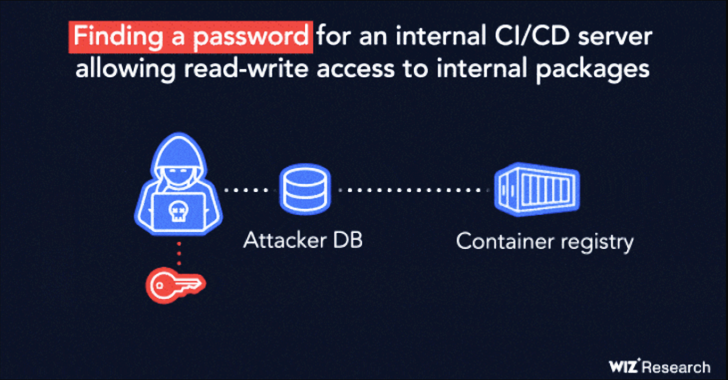
“The vulnerability consists of a series of three uncovered secrets and techniques (Kubernetes service account token, personal container registry password, CI/CD server credentials) coupled with overly permissive community entry to inside construct servers,” Wiz researchers Ronen Shustin and Shir Tamari stated.
Hell’s Keychain commences with an SQL injection flaw in ICD that grants an attacker superuser (aka “ibm”) privileges, which is then used to execute arbitrary instructions on the underlying digital machine internet hosting the database occasion.
This functionality is weaponized to entry a Kubernetes API token file, permitting for broader post-exploitation efforts that contain pulling container photographs from IBM’s personal container registry, which shops photographs associated to ICD for PostgreSQL, and scanning these photographs for extra secrets and techniques.
“Container photographs sometimes maintain proprietary supply code and binary artifacts which might be the corporate’s mental property,” the researchers defined. “They can even include data that an attacker may leverage to seek out further vulnerabilities and carry out lateral motion inside the service’s inside setting.”
Wiz stated it was capable of extract inside artifact repository and FTP credentials from the picture manifest recordsdata, successfully allowing unfettered read-write entry to trusted repositories and IBM construct servers.
An assault of this type may have extreme ramifications, because it allows the adversary to overwrite arbitrary recordsdata which might be used within the construct strategy of the PostgreSQL picture, which might then be put in on each database occasion.
The American expertise large, in an impartial advisory, stated that each one IBM Cloud Databases for PostgreSQL cases have been doubtlessly impacted by the bug, however famous that it discovered no proof of malicious exercise.
It additional said that the fixes have been routinely utilized to buyer cases and that no additional motion is required. The mitigations have been rolled out on August 22 and September 3, 2022.
“These vulnerabilities may have been exploited by a malicious actor as a part of an intensive exploit chain culminating in a supply-chain assault on the platform,” the researchers stated.
To mitigate such threats, it is advisable that organizations monitor their cloud environments for scattered credentials, implement community controls to forestall entry to manufacturing servers, and safeguard towards container registry scraping.
[ad_2]