[ad_1]
A menace actor with a suspected China nexus has been linked to a set of espionage assaults within the Philippines that primarily depends on USB gadgets as an preliminary an infection vector.
Mandiant, which is a part of Google Cloud, is monitoring the cluster beneath its uncategorized moniker UNC4191. An evaluation of the artifacts used within the intrusions signifies that the marketing campaign dates way back to September 2021.
“UNC4191 operations have affected a variety of private and non-private sector entities primarily in Southeast Asia and increasing to the U.S., Europe, and APJ,” researchers Ryan Tomcik, John Wolfram, Tommy Dacanay, and Geoff Ackerman mentioned.
“However, even when focused organizations had been primarily based in different areas, the particular methods focused by UNC4191 had been additionally discovered to be bodily positioned within the Philippines.”
The reliance on contaminated USB drives to propagate the malware is uncommon if not new. The Raspberry Robin worm, which has developed into an preliminary entry service for follow-on assaults, is thought to make use of USB drives as an entry level.
The menace intelligence and incident response agency mentioned that the assaults led to the deployment of three new malware households dubbed MISTCLOAK, DARKDEW, BLUEHAZE, and Ncat, the latter of which is a command-line networking utility that is used to create a reverse shell on the sufferer system.
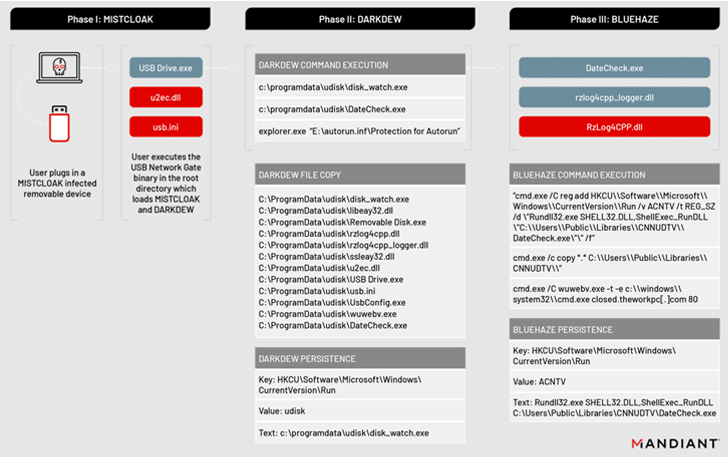
MISTCLOAK, for its half, will get activated when a person plugs in a compromised detachable system to a system, performing as a launchpad for an encrypted payload referred to as DARKDEW that is able to infecting detachable drives, successfully proliferating the infections.
“The malware self-replicates by infecting new detachable drives which might be plugged right into a compromised system, permitting the malicious payloads to propagate to further methods and doubtlessly acquire knowledge from air-gapped methods,” the researchers defined.
The DARKDEW dropper additional serves to launch one other executable (“DateCheck.exe”), a renamed model of a official, signed software referred to as “Razer Chromium Render Process” that invokes the BLUEHAZE malware.
BLUEHAZE, a launcher written in C/C++, takes the assault chain ahead by beginning a replica of Ncat to create a reverse shell to a hardcoded command-and-control (C2) deal with.
“We imagine this exercise showcases Chinese operations to achieve and keep entry to private and non-private entities for the needs of intelligence assortment associated to China’s political and business pursuits,” the researchers mentioned.