[ad_1]
Amazon Web Services (AWS) has resolved a cross-tenant vulnerability in its platform that could possibly be weaponized by an attacker to realize unauthorized entry to assets.
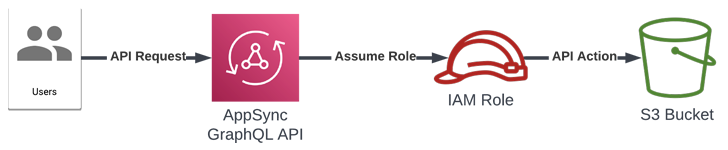
The concern pertains to a confused deputy drawback, a kind of privilege escalation the place a program that does not have permission to carry out an motion can coerce a more-privileged entity to carry out the motion.
The shortcoming was reported by Datadog to AWS on September 1, 2022, following which a patch was shipped on September 6.
“This assault abuses the AppSync service to imagine [identity and access management] roles in different AWS accounts, which permits an attacker to pivot right into a sufferer group and entry assets in these accounts,” Datadog researcher Nick Frichette stated in a report printed final week.
In a coordinated disclosure, Amazon stated that no clients had been affected by the vulnerability and that no buyer motion is required.
It described it as a “case-sensitivity parsing concern inside AWS AppSync, which might probably be used to bypass the service’s cross-account position utilization validations and take motion because the service throughout buyer accounts.”
AWS AppSync provides builders GraphQL APIs to retrieve or modify knowledge from a number of knowledge sources in addition to robotically sync knowledge between cellular and internet purposes and the cloud.
The service can be used to combine with different AWS providers by means of particular roles designed to carry out the mandatory API calls with the required IAM permissions.
While AWS does have safeguards in place to stop AppSync from assuming arbitrary roles by validating the position’s Amazon Resource Name (ARN), the issue stems from the truth that the test could possibly be trivially bypassed by passing the “serviceRoleArn” parameter in a decrease case.
This habits might then be exploited to supply the identifier of a job in a special AWS account.
“This vulnerability in AWS AppSync allowed attackers to cross account boundaries and execute AWS API calls in sufferer accounts through IAM roles that trusted the AppSync service,” Frichette stated.
“By utilizing this technique, attackers might breach organizations that used AppSync and achieve entry to assets related to these roles.”
[ad_2]