[ad_1]
An evaluation of firmware photographs throughout units from Dell, HP, and Lenovo has revealed the presence of outdated variations of the OpenSSL cryptographic library, underscoring a provide chain danger.
EFI Development Kit, aka EDK, is an open supply implementation of the Unified Extensible Firmware Interface (UEFI), which features as an interface between the working system and the firmware embedded within the system’s {hardware}.
The firmware growth surroundings, which is in its second iteration (EDK II), comes with its personal cryptographic bundle referred to as CryptoPkg that, in flip, makes use of companies from the OpenSSL venture.
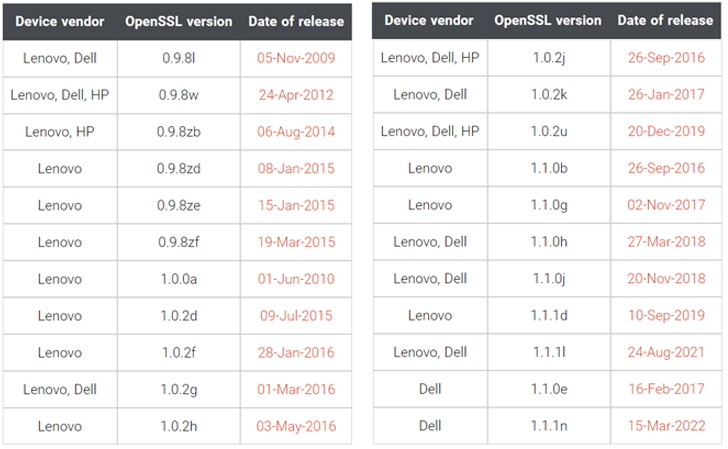
Per firmware safety firm Binarly, the firmware picture related to Lenovo Thinkpad enterprise units was discovered to make use of three completely different variations of OpenSSL: 0.9.8zb, 1.0.0a, and 1.0.2j, the final of which was launched in 2018.
What’s extra, one of many firmware modules named InfineonTpmUpdateDxe relied on OpenSSL model 0.9.8zb that was shipped on August 4, 2014.
“The InfineonTpmUpdateDxe module is liable for updating the firmware of Trusted Platform Module (TPM) on the Infineon chip,” Binarly defined in a technical write-up final week.
“This clearly signifies the provision chain drawback with third-party dependencies when it seems to be like these dependencies by no means acquired an replace, even for vital safety points.”
The range of OpenSSL variations apart, a few of the firmware packages from Lenovo and Dell utilized an excellent older model (0.9.8l), which got here out on November 5, 2009. HP’s firmware code, likewise, used a 10-year-old model of the library (0.9.8w).
The indisputable fact that the system firmware makes use of a number of variations of OpenSSL in the identical binary bundle highlights how third-party code dependencies can introduce extra complexities within the provide chain ecosystem.
Binarly additional identified the weaknesses in what’s referred to as a Software Bill of Materials (SBOM) that arises because of integrating compiled binary modules (aka closed supply) within the firmware.
“We see an pressing want for an additional layer of SBOM Validation on the subject of compiled code to validate on the binary degree, the listing of third-party dependency info that matches the precise SBOM offered by the seller,” the corporate mentioned.
“A ‘trust-but-verify’ method is one of the best ways to take care of SBOM failures and scale back provide chain dangers.”