[ad_1]
The Android banking fraud malware generally known as SharkBot has reared its head as soon as once more on the official Google Play Store, posing as file managers to bypass the app market’s restrictions.
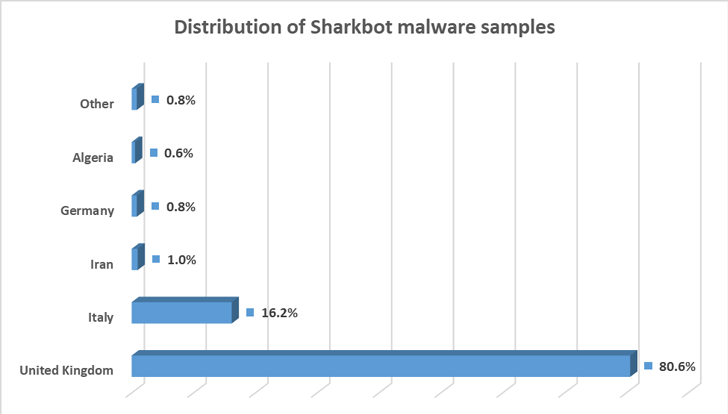
A majority of the customers who downloaded the rogue apps are positioned within the U.Okay. and Italy, Romanian cybersecurity firm Bitdefender stated in an evaluation revealed this week.
SharkBot, first found in the direction of the tip of 2021 by Cleafy, is a recurring cellular menace distributed each on the Google Play Store and different third-party app shops.
One of the trojan’s main targets is to provoke cash transfers from compromised gadgets by way of a way known as “Automatic Transfer System” (ATS), wherein a transaction triggered by way of a banking app is intercepted to swap the payee account with an actor-controlled account within the background.
It’s additionally able to serving a faux login overlay when customers try to open authentic banking apps, stealing the credentials within the course of.
Often, such apps provide seemingly innocent performance, masquerading as antivirus software program and cleaners to sneak into the Google Play Store. But in addition they double up as droppers that, as soon as put in on the system, can fetch the malware payload.
The dropper apps, now taken down, are under –
- X-File Manager (com.victorsoftice.llc) – 10,000+ downloads
- FileVoyager (com.potsepko9.FileManagerApp) – 5,000+ downloads
- LiteCleaner M (com.ltdevelopergroups.litecleaner.m) – 1,000+ downloads
LiteCleaner M remains to be out there for obtain from a third-party app retailer known as Apksos, which additionally homes a fourth SharkBot artifact by the identify “Phone AID, Cleaner, Booster” (com.sidalistudio.developer.app).
The X-File Manager app, which was solely accessible to customers in Italy, attracted over 10,000 downloads earlier than it was eliminated. With Google steadily clamping down on permission abuse, the menace actor’s alternative of utilizing a file supervisor as a lure isn’t a surprise.
That’s as a result of Google’s Developer Program Policy restricts the permission to put in exterior packages (REQUEST_INSTALL_PACKAGES) to a handful of app classes: internet browsers, prompt messengers that help attachments, file managers, enterprise system administration, backup and restore, and system switch.
Invariably, this permission is abused to obtain and set up malware from a distant server. Some of the focused financial institution apps embody Bank of Ireland, Bank of Scotland, Barclays, BNL, HSBC U.Okay., Lloyds Bank, Metro Bank, and Santander.
“The utility [i.e., the dropper] performs anti-emulator checks and targets customers from Great Britain and Italy by verifying if the SIM ISO corresponds with IT or GB,” Bitdefender researchers stated.
Users who’ve put in the aforementioned apps are really useful to delete them and alter their checking account passwords instantly. Users are additionally suggested to allow Play Store Protect, and scrutinize app rankings and critiques earlier than downloading them.
[ad_2]